Abstract
We consider a game on a graph \(G=\langle V, E\rangle \) with two confronting classes of randomized players: \(\nu \) attackers, who choose vertices and seek to minimize the probability of getting caught, and a single defender, who chooses edges and seeks to maximize the expected number of attackers it catches. In a Nash equilibrium, no player has an incentive to unilaterally deviate from her randomized strategy. The Price of Defense is the worst-case ratio, over all Nash equilibria, of \(\nu \) over the expected utility of the defender at a Nash equilibrium.
We orchestrate a strong interplay of arguments from Game Theory and Graph Theory to obtain both general and specific results in the considered setting:
(1) Via a reduction to a Two-Players, Constant-Sum game, we observe that an arbitrary Nash equilibrium is computable in polynomial time. Further, we prove a general lower bound of \(\frac{\textstyle |V|}{\textstyle 2}\) on the Price of Defense. We derive a characterization of graphs with a Nash equilibrium attaining this lower bound, which reveals a promising connection to Fractional Graph Theory; thereby, it implies an efficient recognition algorithm for such Defense-Optimal graphs.
(2) We study some specific classes of Nash equilibria, both for their computational complexity and for their incurred Price of Defense. The classes are defined by imposing structure on the players’ randomized strategies: either graph-theoretic structure on the supports, or symmetry and uniformity structure on the probabilities. We develop novel graph-theoretic techniques to derive trade-offs between computational complexity and the Price of Defense for these classes. Some of the techniques touch upon classical milestones of Graph Theory; for example, we derive the first game-theoretic characterization of König-Egerváry graphs as graphs admitting a Matching Nash equilibrium.







Similar content being viewed by others
Notes
In a star graph, a distinguished vertex, called center, is connected to all other vertices, called terminals.
A similar problem is defined when the input is an arbitrary graph and we are asking about the existence of a collection of Hamiltonian circuits \(V_1, V_2, \ldots , V_k\), for some k that cover the graph G, such that \(|V_i|\ge 6\), for each \(i \in [k]\). The latter problem is mentioned in the discussion following [11, GT13] as an \(\mathcal{NP}\)-complete problem (with attribution to personal communication with C. H. Papadimitriou).
References
Aspvall, B., Plass, M.F., Tarjan, R.E.: A linear-time algorithm for testing the truth of certain quantified boolean formulas. Inf. Process. Lett. 8(3), 121–123 (1979)
Bonifaci, V., Di Iorio, U., Laura, L.: The complexity of uniform Nash equilibria and related regular subgraph problems. Theor. Comput. Sci. 401(1–3), 144–152 (2008)
Bourjolly, J.-M., Pulleyblank, W.R.: König-Egerváry graphs, 2-bicritical graphs and fractional matchings. Discrete Appl. Math. 24(1–3), 63–82 (1989)
Calinescu, G., Kapoor, S., Qiao, K., Shin, J.: Stochastic strategic routing reduces attack effects. In: Proceedings of the IEEE Global Communications Conference, pp. 1–5 (2011)
Cheswick, E.R., Bellovin, S.M.: Firewalls and Internet Security. Addison-Wesley, Reading (1994)
Dasgupta, A., Ghosh, S., Tixeuil, S.: Selfish stabilization. In: Proceedings of the 8th International Symposium on Stabilization, Safety, and Security of Distributed Systems. Lecture Notes in Computer Science, vol. 4280, pp. 231–243. Springer (2006)
Deming, R.W.: Independence numbers of graphs—an extension of the König-Egerváry theorem. Discrete Math. 27(1), 23–33 (1979)
Egerváry, E.: On combinatorial properties of matrices (in Hungarian with German summary). Matematikai és Fizikai Lapok 38, 16–28 (1931)
Fultz, N., Grossklags, J.: Blue versus red: towards a model of distributed security attacks. In: Proceedings of the 13th International Conference on Financial Cryptography and Data Security. Lecture Notes in Computer Science, vol. 5628, pp. 167–183. Springer (2009)
Gallai, T.: Über Extreme Punkt-und Kantenmengen. Annales Universitatis Scientiarum Budapestinensis de Rolando Eötvös Nominatae, Sectio Mathematica 2, 133–138 (1959)
Garey, M.R., Johnson, D.S.: Computers and Intractability: A Guide to the Theory of ${\cal{NP}}$–Completeness. W. H. Freeman and Co., New York (1979)
Gelastou, M., Mavronicolas, M., Papadopoulou, V., Philippou, A., Spirakis, P.: The power of the defender. In: CD-ROM Proceedings of the 2nd International Workshop on Incentive-Based Computing (2006)
Ghani, A.T.A., Tanaka, K.: Network games with and without synchroneity. In: Proceedings of the 2nd International Conference in Decision and Game Theory for Security. Lecture Notes in Computer Science, vol. 7037, pp. 87–103. Springer (2011)
Gordon, L., Loeb, M.: The economics of information security investment. ACM Trans. Inf. Syst. Secur. 5(4), 438–457 (2002)
Haifeng, X.: The mysteries of security games: equilibrium computation becomes combinatorial algorithm design. In: Proceedings of the 2016 ACM Conference on Economics and Computation, pp. 497–514 (2016)
Hausken, K., Bier, V.M.: Defending against multiple different attackers. Eur. J. Oper. Res. 211(2), 370–384 (2011)
Karlin, A.R., Peres, Y.: Game Theory, Alive. American Mathematical Society, Providence (2017)
Kearns, M., Ortiz, L.: Algorithms for interdependent security games. In: Advances in Neural Information Processing Systems, pp. 561–568. MIT Press (2004)
Khachiyan, L.: A polynomial algorithm in linear programming. Sov. Math. Dokl. 20, 191–194 (1979)
König, D.: Graphen und Matrizen. Matematikai Lapok 38, 116–119 (1931)
Korach, E., Nguyen, T., Peis, B.: Subgraph characterization of red/blue-split graphs and König-Egerváry graphs. In: Proceedings of the 17th Annual ACM-SIAM Symposium on Discrete Algorithms, pp. 842–850 (2006)
Koutsoupias, E., Papadimitriou, C.H.: Worst-case equilibria. Comput. Sci. Rev. 3(2), 65–69 (2009)
Letchford, J., Conitzer, V.: Solving security games on graphs via marginal probabilities. In: Proceedings of the 27th AAAI Conference on Artificial Intelligence pp. 591–597 (2013)
Lye, K., Wing, J.: Game strategies in network security. Int. J. Inf. Secur. 4(1), 71–86 (2005)
Liu, P., Zang, W., Yu, M.: Incentive-based modeling and inference of attacker intent, objectives, and strategies. ACM Trans. Inf. Syst. Secur. 8(1), 78–118 (2005)
Markham, T., Payne, C.: Security at the network edge: a distributed firewall architecture. In: Proceedings of the 2nd DARPA Information Survivability Conference and Exposition, vol. 1, pp. 279–286 (2001)
Mavronicolas, M., Monien, B., Papadopoulou, V.G.: How many attackers can selfish defenders catch? Discrete Appl. Math. 161(16–17), 2563–2586 (2013)
Mavronicolas, M., Papadopoulou, V.G., Philippou, A., Spirakis, P.G.: A network game with attackers and a defender. Algorithmica 51(3), 315–341 (2008)
Mavronicolas, M., Papadopoulou, V.G., Philippou, A., Spirakis, P.G.: A graph-theoretic network security game. Int. J. Auton. Adapt. Commun. Spec. Issue Algorithmic Game Theory 1(4), 390–410 (2008)
Moore, C., Mertens, S.: The Nature of Computation. Oxford University Press, Oxford (2011)
Nash, J.F.: Equilibrium points in N-person games. Proc. Natl. Acad. Sci. USA 36, 48–49 (1950)
Nash, J.F.: Non-cooperative games. Ann. Math. 54(2), 286–295 (1951)
Okamoto, S., Hazon, N., Sycara, K.: Solving non-zero-sum multiagent network flow security games with attack costs. In: Proceedings of the 11th International Conference on Autonomous Agents and Multiagent Systems, pp. 879–888 (2012)
Oláron Evans, T., Bishop, S.R.: Static search games played over graphs and general metric spaces. Eur. J. Oper. Res. 231, 667–689 (2013)
Scheinerman, E.R., Ullman, D. H.: Fractional Graph Theory, Wiley-Interscience Series in Discrete Mathematics and Optimization (1997)
Sterboul, F.: A characterization of the graphs in which the transversal number equals the matching number. J. Comb. Theory (Ser. B) 27(2), 228–229 (1979)
Tsai, J., Yin, Z., Kwak, J., Kempe, D., Kiekintveld, C., Tambe, M.: Urban security: game-theoretic resource allocation in networked physical domains. In: Proceedings of the 24th AAAI Conference on Artificial Intelligence, p. 881 (2010)
Tsai, J., Yin, Z., Kwak, J., Kempe, D., Kiekintveld, C., Tambe, M.: Game-theoretic allocation of security forces in a city. In: Proceeding of the 3th International Workshop on Optimisation in Multi-agent Systems (OPTMAS III) (2010)
Valiant, L.G.: The complexity of computing the permanent. Theor. Comput. Sci. 8(2), 189–201 (1979)
von Neumann, J.: Zur Theorie der Gesellschaftsspiele. Math. Ann. 100, 295–320 (1928)
West, D.B.: Introduction to Graph Theory, 2nd edn. Prentice Hall, Upper Saddle River (2001)
Acknowledgements
This work was partially supported by the IST Program of the European Union under Contract Numbers IST-2004-001907 (DELIS) and IST-015964 (AEOLUS). The work of Loizos Michael was supported by funding from the EU’s Horizon 2020 Research and Innovation Programme under grant agreement no. 739578, and from the Government of the Republic of Cyprus through the Directorate General for European Programmes, Coordination, and Development.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
This paper combines, unifies and extends results that appeared in preliminary form in the Proceedings of the 31st International Symposium on Mathematical Foundations of Computer Science, pp. 717–728, Vol. 4162, Lecture Notes in Computer Science, Springer-Verlag, August/September 2006, and in the Proceedings of the 8th International Conference on Distributed Computing and Networking, pp. 115–126, Vol. 4308, Lecture Notes in Computer Science, Springer-Verlag, December 2006.
Appendix: Proof of Lemma 11.5
Appendix: Proof of Lemma 11.5
Set:
-
\(V^{\prime }:=\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}}) \),
-
\(E^{\prime }: =\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) and \(r: =d_{G(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v)\) for an arbitrary vertex \(v\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\).
By Lemma 11.3, \(V^{\prime }\), \(E^{\prime }\) and r satisfy Conditions (1) and (2) in the characterization of Defender-Uniform Graphs (Theorem 11.1). We first prove:
Lemma A.1
\(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})=E\).
Proof
Assume, by way of contradiction, that \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}) \subset E\). Then, there is an edge \((v_{i},v_{i+1}) \not \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), for some i, \(1\le i \le n\). Since a Nash equilibrium is a Covering profile (Proposition 7.1), Condition (1) in the definition of a Covering profile implies that \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) is an Edge Cover. Since n is odd, this implies that \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) contains two adjacent edges. Assume, without loss of generality, that both edges \((v_n,v_1),(v_1,v_2)\in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\). Thus, \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v_1)=2\). On the other hand, since \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) is an Edge Cover and \((v_{i},v_{i+1}) \not \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), it follows that \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v_i)= 1\). We continue to prove:
Claim A.2
For any vertex \(v\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\), \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v)= 1\).
Proof
Since \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) is an Edge Cover, \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v)\ge 1\). Assume, by way of contradiction, that \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v)>1\). It follows that \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v)> d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v_i)\). Conditions (1/a) and (1/b) in the characterization of Defender-Uniform Graphs (Theorem 11.1) together imply that \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v_i)\ge d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v)\). A contradiction. \(\square \)
\({\textit{Proof that}}\; v_1\not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) By Claim A.2, for any vertex \(v\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\), \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v)\) \( =1\). Since \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v_1) =2\), it follows that \(v_1\not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\).
\({\textit{Proof that}}\;v_n, v_2\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) Since a Nash equilibrium is a Covering profile (Proposition 7.1), Condition (2) in the definition of a Covering profile implies that \(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) is a Vertex Cover of the graph \(\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))\). Since \(v_1 \not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) while both \((v_n,v_1),\) \((v_1,v_2)\in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), this implies that both \(v_n, v_2\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\).
We continue to prove:
Claim A.3
Consider any vertex \(v_i\), \(i\ge 2\) such that \(v_i\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}}) \), \(( v_{i-1},v_i )\in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) and \(v_{i-1}\not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}}) \). Then, the following conditions hold: (1) \((v_i, v_{i+1})\not \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), (2) \(v_{i+1}\not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\), (3) \((v_{i+1}, v_{i+2})\in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), and (4) \(v_{i+2} \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\).
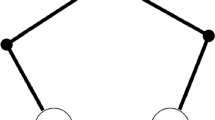
An illustration of Claim A.3 is shown in Fig. 8.
An illustration of the sets \(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) and \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) in a Defender-Uniform Nash equilibrium for the odd cycle graph \(\mathcal{C}_n\), where n is an odd integer. The edges in \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) are shown with bold edges and the vertices in \(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) are shown with surrounding circles
Proof
We separately prove each of the four claims.
(1): Since \(v_i\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\), by Claim A.2, \(d_{\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))}(v_i) =1\). Since \((v_i,v_{i-1}) \) \(\in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), it follows that \((v_{i},v_{i+1}) \) \(\not \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\).
(2): Assume, by way of contradiction, that \(v_{i+1}\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\). Then, \( \mathsf{A_{\varvec{\sigma }}}(v_{i+1})>0\), so that
Since \((v_i,v_{i-1})\in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), Condition (C.2) in the characterization of Nash equilibria (Proposition 3.2) implies that \(\mathsf{A_{\varvec{\sigma }}}(v_{i},v_{i-1})\ge \mathsf{A_{\varvec{\sigma }}}(v_i,v_{i+1})\). A contradiction.
(3): Recall that \(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) is an Edge Cover of \(\mathcal{C}_n \). Consider vertex \(v_{i+1}\); since \((v_{i},v_{i+1}) \not \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\), it follows that \((v_{i+1},v_{i+2}) \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\).
(4): Recall that \(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) is a Vertex Cover of the graph \(\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))\). Since \((v_{i+1},v_{i+2}) \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\) while \( v_{i+1} \not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\), it follows that \(v_{i+2}\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\).
The claim follows. \(\square \)
Consider now vertex \(v_2\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\). By Claim A.3, \((v_1,v_2) \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}) \) but \(v_1\not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\). Hence, Claim A.3 applies repeatedly (in a clockwise fashion) to yield that \(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}}) =\left\{ v_2,v_4,\right. \) \(\left. \ldots , v_{n-1},v_1 \right\} \); thus, \(v_1\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\). A contradiction. \(\square \)
We continue to prove:
Lemma A.4
\(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})=V\).
Proof
Since a Nash equilibrium is a Covering profile (Proposition 7.1), Condition (2) in the definition of a Covering profile implies that \(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) is a Vertex Cover of the graph \(\mathcal{C}_n(\mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d}))\). Since n is odd, this implies that \(\mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\) contains at least two adjacent vertices of \(\mathcal{C}_n\). We prove:
Claim A.5
Assume that vertices \(v_{i}, v_{i+1}\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\). Then, \(v_{i+2}\in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\).
Proof
Assume, by way of contradiction, that \(v_{i+2}\not \in \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})\). Then,
Lemma A.1 implies that both edges \((v_{i},v_{i+1}), (v_{i+1},v_{i+2}) \in \mathsf{Supp_{\varvec{\sigma }}}(\mathsf{d})\). Hence, by Condition (C.2) in the characterization of Nash equilibria (Proposition 3.2), \(\mathsf{A_{\varvec{\sigma }}}(v_{i},v_{i+1})= \mathsf{A_{\varvec{\sigma }}}(v_{i+1},v_{i+2})\). A contradiction. \(\square \)
By repeated application of Claim A.5, it follows that \( \mathsf{Supp_{\varvec{\sigma }}}({{\mathcal {A}}})= V\). \(\square \)
Rights and permissions
About this article
Cite this article
Mavronicolas, M., Michael, L., Papadopoulou Lesta, V. et al. The Price of Defense. Algorithmica 83, 1256–1315 (2021). https://doi.org/10.1007/s00453-020-00783-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00453-020-00783-7