Abstract
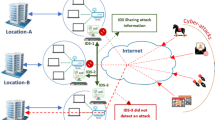
DDoS attacks that depend on Internet Control Message Protocol version 6 (ICMPv6) are one of the most commonly performed IPv6 attacks against today’s IPv6 networks. A few detection systems were proposed to detect these attacks based on self-generated datasets. These datasets used an unsuitable representation that depends on packets format as well as they include non-qualified features which lead to false alerts if the systems are applied in real networks. Moreover, most of the existing datasets are unavailable for other researchers’ usage due to their author’s privacy issues. The objective of this paper is benchmarking datasets of ICMPv6-based DDoS attacks to be used for the tuning, evaluations, and comparisons of any detection system of the attacks. The datasets setup is based on a real IPv6-enabled network topology and ensuring attack exposure. The proposed datasets are considered as the first labeled and publically available flow-based datasets represented using a set of flow-based features of the ICMPv6-based DDoS attacks. The requirements of good datasets have been achieved in the proposed datasets to ensure they are worthy be used by other researchers. Moreover, the datasets and their features proved their abilities to represent the attacks traffics by achieving robust and acceptable high detection accuracies as well as low false positive rate.
Similar content being viewed by others
References
Conta A, Gupta M (2006) Internet control message protocol (icmpv6) for the internet protocol version 6 (ipv6) specification. Request for Comments 4443 [online]. https://tools.ietf.org/html/rfc4443.Last Accessed Aug 2015
Postel J (1981) Rfc 792: Internet control message protocol. Request for Comments 792 [online]. https://tools.ietf.org/html/rfc792.Last Accessed 2016
Elejla OE, Anbar M, Belaton B (2016) Icmpv6-based dos and ddos attacks and defense mechanisms: Review. IETE Tech Rev 34:1–18
Ard JB (2012) Internet protocol version six (ipv6) at uc davis: traffic analysis with a security perspective. University of California, Davis
Weber J, Wegener C, Schwenk J (2013) Ipv6 security test laboratory,” master dissertation Department of Network and Data Security. Ruhr-University Bochum, Bochum
Elejla OE, Belaton B, Anbar M, Alnajjar A (2016) A reference dataset for icmpv6 flooding attacks. J Eng Appl Sci 11(3):476–481
Lakhina A, Crovella M, Diot C (2004) Characterization of network-wide anomalies in traffic flows. In: Proceedings of the 4th ACM SIGCOMM conference on internet measurement, pp 201–206
Sperotto A, Sadre R, Pras A (2008) Anomaly characterization in flow-based traffic time series. In: International workshop on IP operations and management, Springer, Berlin, pp 15–27
Strayer WT, Lapsely D, Walsh R, Livadas C (2008) Botnet detection based on network behavior. In: Lee W, Wang C, Dagon D (eds) Botnet detection. Advances in Information Security, vol 36. Springer, New York, pp 1–24
Sheikhan M, Jadidi Z (2014) Flow-based anomaly detection in high-speed links using modified GSA-optimized neural network. Neural Comput Appl 24(3–4):599–611
Sperotto A (2010) Flow-based intrusion detection. Ph.D. thesis Centre for Telematics and Information Technology. University of Twente, Enschede
Winter P, Hermann E, Zeilinger M (2011) Inductive intrusion detection in flow-based network data using one-class support vector machines. In: 4th IFIP international conference on IEEE new technologies, mobility and security (NTMS), pp 1–5
Jacobson V, Craig Leres S (2016) Mccanne. Tcpdump. http://www.tcpdump.org, Accessed 2016
Chappell L, Combs G (2010) Wireshark network analysis: The official wireshark certified network analyst study guide. https://www.wireshark.org/, Accessed 2016
Nsl-Kdd (1998) Dataset for network –based intrusion detection systems. http://iscx.info/NSL-KDD/ Accessed 2016
Lippmann R, Haines JW, Fried DJ, Korba J, Das K (2000) The 1999 darpa off-line intrusion detection evaluation. Comput Netw 34(4):579–595
U. O. California, Kdd cup (1999). http://kdd.ics.uci.edu/databases/kddcup99/kddcup99.html, Accessed 2016
L. B. N. Laboratory (2004) Lbnl/icsi enterprise tracing project. http://www.icir.org/enterprise-tracing/. Accessed 2016
Elejla OE, Jantan AB, Ahmed AA (2014) Three layers approach for network scanning detection. J Theor Appl Inf Technol 70(2):251–264
Wide (2016) Mawi working group traffic archive. http://mawi.wide.ad.jp/mawi/. Accessed 2016
Barrera D, Van Oorschot P (2009) Security visualization tools and ipv6 addresses. In: 6th international workshop on IEEE visualization for cyber security, VizSec 2009. pp 21–26
Caida (2014) The cooperative association for internet data analysis. https://www.caida.org/data/active/ipv6_allpref_topology_dataset.xml. Accessed 25 Feb 2016
Gray MD (2015) Discovery of ipv6 router interface addresses via heuristic methods. Monterey, Naval Postgraduate School, California
Fomenkov M, Claffy K (2011) Internet measurement data management challenges. In: Workshop on research data lifecycle management, Princeton
Zulkiflee M, Haniza N, Shahrin S, Ghani M (2014) A framework of ipv6 network attack dataset construction by using testbed environment. Int Rev Comput Softw (IRECOS) 9(8):1434–1441
Zulkiflee MA, Ahmad MSss, Sahib S, Ghani M (2015) A framework of features selection for ipv6 network attacks detection. WSEAS Trans Commun 14(46):399–408
Saad R, Manickam S, Alomari E, Anbar M, Singh P (2014) Design & deployment of testbed based on icmpv6 flooding attack. J Theor Appl Inf Technol 64(3):795–801
Najjar F, Kadhum MM (2015) Reliable behavioral dataset for ipv6 neighbor discovery protocol investigation. In: 5th international conference on, IEEE IT convergence and security (ICITCS), pp 1–5
Elejla OE, Anbar M, Belaton B (2016) Flow-based datasets. https://sites.google.com/site/flowbaseddatasets/. Accessed 2016
Usm (2016) Universiti sain malaysia (usm). https://www.usm.my/index.php/en/. Accessed 2016
Heuse M (2013) Thc ipv6 attack tool kit. http://www.aldeid.com/wiki/THC-IPv6-Attack-Toolkit. Accessed 2015
Gont F (2012) Si6 networks’ ipv6 toolkit. http://www.si6networks.com. Accessed 2015
Grossman J, Marsili B, Goudjil C, Eromenko A (2013) Gns3 graphical network simulator. https://www.gns3.com/. Accessed 23 Jan 2016
Cisco N (2001) Netflow services solutions guide. http://www.cisco.com/c/en/us/td/docs/ios/solutions_docs/netflow/nfwhite.html#wp1030058. Accessed 2016
Baldi M, Baralis EM, Risso FGO (2004) Data mining techniques for effective flow-based analysis of multi-gigabit network traffic
Yu S (2014) Distributed denial of service attack and defense. Springer, Berlin
Vykopal J (2010) Flow-based intrusion detection in large and high-speed networks. PhD thesis
Tavallaee M, Bagheri E, Lu W, Ghorbani AA (2012) Nsl-kdd dataset
Hall M, Frank E, Holmes G, Pfahringer B, Reutemann P, Witten IH (2009) The weka data mining software: an update. ACM SIGKDD Explor Newslett 11(1):10–18
Japkowicz N (2000) The class imbalance problem: Significance and strategies. In: Proceedings of the international conference on artificial intelligence, Citeseer
Weiss GM, Provost F (2003) Learning when training data are costly: the effect of class distribution on tree induction. J Artif Intell Res 19:315–354
Acknowledgements
This research was supported by the Short Term Research Grant, Universiti Sains Malaysia (USM) No: 304/PNAV/6313272.
Author information
Authors and Affiliations
Corresponding author
Ethics declarations
Disclosure
The authors declare that there is no conflict of interest regarding the publication of this paper.
Rights and permissions
About this article
Cite this article
Elejla, O.E., Anbar, M., Belaton, B. et al. Labeled flow-based dataset of ICMPv6-based DDoS attacks. Neural Comput & Applic 31, 3629–3646 (2019). https://doi.org/10.1007/s00521-017-3319-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00521-017-3319-7