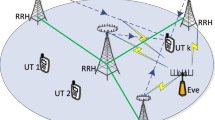
Abstract
This paper considers a unicast multiuser multiple-input single-output (MISO) downlink system overheard by multiple single-antenna eavesdroppers. The objective is to jointly design the beamforming vectors and the artificial noise (AN) covariance matrix with imperfect channel state information (CSI) at the transmitter, such that the total transmit power is minimized while satisfying probabilistic quality of service (QoS) constraints at legitimate users and the eavesdroppers. Using Bernstein-type inequalities and the S-procedure, we recast the non-convex power minimization problem as two different convex semidefinite programs (SDPs) which can be solved using interior-point methods. Simulation results show that the proposed methods outperform a nonrobust method and the ones using the isotropic AN.
创新点
本文考虑了存在多个单天线窃听者的多用户单播MISO通信系统。提出了人工噪声辅助的安全波束成形发送方法。其目的为, 根据非理想信道状态信息对发送端的波束成形向量和人工噪声协方差矩阵进行联合优化, 在满足合法用户和窃听者的概率服务质量(Quality of Service, QoS)约束下, 最小化发送功率。由于无法获得概率QoS约束的解析表达式, 分别采用Bernstein-type不等式和S-过程将其转化为两种不同的确定性约束, 进而得到两种不同的半定规划(Semidefinite Program, SDP)问题。仿真结果表明所提方法的性能优于非鲁棒方法和全向人工噪声(Isotropic Artificial Noise)辅助波束成形方法。
Similar content being viewed by others
References
Jiang SQ. Ont-time secure key agreement. Sci China Inf Sci, 2015, 58: 012110
Ni L, Chen G L, Li J H, et al. Strongly secure identity-based authenticated key agreement protocols in the escrow mode. Sci China Inf Sci, 2013, 56: 082113
Wyner A D. The wire-tap channel. Bell Syst Tech J, 1975, 54: 1355–1387
Zhang Z, Zhang W, Tellambura C. MIMO-OFDM channel estimation in the presence of frequency offsets. IEEE Trans Wirel Commun, 2008, 7: 2329–2339
Li Q, Ma W K. Spatially selective artificial-noise aided transmit optimization for MISO multi-Eves secrecy rate maximization. IEEE Trans Signal Process, 2013, 61: 2704–2717
Wang B, Mu P C, Yang P Z, et al. Two-step transmission with artificial noise for secure wireless SIMO communications. Sci China Inf Sci, 2015, 58: 042308
Wang H M, Liu F, Xia X G. Joint source-relay precoding and power allocation for secure amplify-and-forward MIMO relay networks. IEEE Trans Inf Forens Secur, 2014, 9: 1240–1250
Liu L, Zhang R, Chua K C. Secrecy wireless information and power transfer with MISO beamforming. IEEE Trans Signal Process, 2014, 62: 1850–1863
Wang J, Bengtsson M, Ottersten B, et al. Robust MIMO precoding for several classes of channel uncertainty. IEEE Trans Signal Process, 2013, 61: 3056–3070
Tang Y, Xiong J, Ma D, et al. Robust artificial noise aided transmit design for MISO wiretap channels with channel uncertainty. IEEE Commun Lett, 2013, 17: 2096–2099
Li J, Petropulu A P. Explicit solution of worst-case secrecy rate for MISO wiretap channels with spherical uncertainty. IEEE Trans Signal Process, 2012, 60: 3892–3895
Guan X, Cai Y, Yang W. On the reliability-security tradeoff and secrecy throughput in cooperative ARQ. IEEE Commun Lett, 2014, 18: 479–482
Cai Y, Guan X, Yang W. Secure transmission design and performance analysis for cooperation exploring outdated CSI. IEEE Commun Lett, 2014, 18: 1637–1640
Wang L, Yang N, Elkashlan M, et al. Physical layer security of maximal ratio combining in two-wave with diffuse power fading channels. IEEE Trans Inf Forens Secur, 2014, 9: 247–258
Li Q, Ma W K, So A M C. A safe approximation approach to secrecy outage design for MIMO wiretap channels. IEEE Signal Process Lett, 2014, 21: 118–121
Pei M Y, Wei J B, Wong K K, et al. Masked beamforming for multiuser MIMO wiretap channels with imperfect CSI. IEEE Trans Wirel Commun, 2012, 11: 544–549
Lin P H, Lai S H, Lin S C, et al. On secrecy rate of the generalized artificial-noise assisted secure beamforming for wiretap channels. IEEE J Sel Area Commun, 2013, 31: 1728–1740
Liao W C, Chang T H, Ma W K, et al. QoS-based transmit beamforming in the presence of eavesdroppers: an optimized artificial-noise-aided approach. IEEE Trans Signal Process, 2011, 59: 1202–1216
Romero-Zurita N, Ghogho M, Mc Lernon DC. Outage probability based power distribution between data and artificial noise for physical layer security. IEEE Signal Process Lett, 2012, 19: 71–74
Fei Z S, Ni J Q, Zhao D, et al. Ergodic secrecy rate of two-user MISO interference channels with statistical CSI. Sci China Inf Sci, 2014, 57: 102302
Xu Y, Wang J, Wu Q. Effective capacity region of two-user opportunistic spectrum access. Sci China Inf Sci, 2011, 54: 1928–1937
Goel S, Negi R. Guaranteeing secrecy using artificial noise. IEEE Trans Wirel Commun, 2008, 7: 2180–2189
Zhou X, Mc Kay M R. Secure transmission with artificial noise over fading channels: achievable rate and optimal power allocation. IEEE Trans Veh Technol, 2010, 59: 3831–3842
Luo Z Q, Ma W K, So A C, et al. Semidefinite relaxation of quadratic optimization problems. IEEE Signal Process Mag, 2010, 27: 20–34
Ma S, Sun D. Chance constrained robust beamforming in cognitive radio networks. IEEE Commun Lett, 2013, 17: 67–70
Boyd S, Vandenberghe L. Convex Optimization. Cambridge: Cambridge University Press, 2004
Li Q, Ma W K, So A C. Safe convex approximation to outage-based MISO secrecy rate optimization under imperfect CSI and with artificial noise. In: Proceedings of 2011 Conference Record of the 45th Asilomar Conference on Signals, Systems and Computers (ASILOMAR), Pacific Grove, 2011. 207–211
Grant M, Boyd S. CVX: Matlab software for disciplined convex programming. version 2.0. http://cvxr.com/cvx, 2012
Wang K Y, Chang T H, Ma W K, et al. A semidefinite relaxation based conservative approach to robust transmit beamforming with probabilistic SINR constraints. In: Proceedings of European Signal Processing Conference (EUSIPCO), Aalborg, 2010. 23–27
Leon-Garcia A. Probability, Statistics, and Random Processes for Electrical Engineering. Upper Saddle River: Pearson Education Inc., 2008
Ben-Tal A, Nemirovski A. Lectures on Modern Convex Optimization: Analysis, Algorithms, and Engineering Applications. Philadelphia: SIAM, 2001
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Zhang, L., Jin, L., Luo, W. et al. Robust secure transmission for multiuser MISO systems with probabilistic QoS constraints. Sci. China Inf. Sci. 59, 1–13 (2016). https://doi.org/10.1007/s11432-015-5342-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11432-015-5342-6
Keywords
- physical layer security
- artificial noise
- imperfect CSI
- robust beamforming
- semidefinite program
- outage probability