Abstract
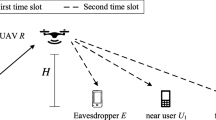
This paper makes an investigation of a secure unmanned aerial vehicle (UAV)-aided communication network based on directional modulation (DM). In this network, ground base station (GBS) acts as a control center to transmit confidential message and artificial noise (AN). The UAV user, moving along a linear flight trajectory, is intended to receive the useful information from GBS. At the same time, it also sends AN signals to further interference eavesdropper’s channel. Aiming at maximizing secrecy rate during the UAV flight process, a joint optimization problem is formulated with respect to power allocation (PA) factors, beamforming vector and AN projection matrices. For simplicity, maximum rate transmission, nullspace projection and the leakage-based method are applied to form the transmit beamforming vector, AN projection matrix at GBS, and AN projection vector at UAV user, respectively. Following this, the optimization problem reduces to a bivariate optimization programme with two PA factors. An alternating iterative algorithm (AIA) is proposed to optimize the two PA factors. Simulation results demonstrate that, compared to the half-duplex (HD) mode, the proposed strategy for full-duplex (FD) mode achieves a higher secrecy rate (SR) and outperforms the FD mode with fixed PA strategy.
Similar content being viewed by others
References
Zeng Y, Zhang R, Lim T J. Wireless communications with unmanned aerial vehicles: opportunities and challenges. IEEE Commun Mag, 2016, 54: 36–42
Wu Q Q, Zeng Y, Zhang R. Joint trajectory and communication design for multi-UAV enabled wireless networks. IEEE Trans Wirel Commun, 2018, 17: 2109–2121
Li A, Zhang W. Mobile jammer-aided secure UAV communications via trajectory design and power control. China Commun, 2018, 15: 141–151
Zhang G C, Wu Q Q, Cui M, et al. Securing UAV communications via trajectory optimization. In: Proceedings of IEEE Global Communications Conference, 2017
Chen Y, Zhao N, Ding Z, et al. Multiple UAVs as relays: multi-hop single link versus multiple dual-hop links. IEEE Trans Wirel Commun, 2018, 17: 6348–6359
Yang D C, Wu Q Q, Zeng Y, et al. Energy trade-off in ground-to-UAV communication via trajectory design. IEEE Trans Veh Technol, 2018, 67: 6721–6726
Xu Y F, Ren G C, Chen J, et al. A one-leader multi-follower bayesian-stackelberg game for anti-jamming transmission in UAV communication networks. IEEE Access, 2018, 6: 21697–21709
Cheng F, Zhang S, Li Z, et al. UAV trajectory optimization for data offloading at the edge of multiple cells. IEEE Trans Veh Technol, 2018, 67: 6732–6736
Zhang G, Yan H, Zeng Y, et al. Trajectory optimization and power allocation for multi-hop UAV relaying communications. IEEE Access, 2018, 6: 48566–48576
Zhou X B, Yan S H, Hu J S, et al. Joint optimization of a UAV’s trajectory and transmit power for covert communications. 2018. ArXiv: 1812.00583
Zhong C, Yao J, Xu J. Secure UAV communication with cooperative jamming and trajectory control. IEEE Commun Lett, 2019, 23: 286–289
Zhou X B, Wu Q Q, Yan S H, et al. UAV-enabled secure communications: joint trajectory and transmit power optimization. IEEE Trans Veh Technol, 2019, 68: 4069–4073
Cai Y, Cui F, Shi Q, et al. Dual-UAV-enabled secure communications: joint trajectory design and user scheduling. IEEE J Sel Areas Commun, 2018, 36: 1972–1985
Liu C, Quek T Q S, Lee J. Secure UAV communication in the presence of active eavesdropper (invited paper). In: Proceedings of International Conference on Wireless Communications and Signal Processing, 2017
Babakhani A, Rutledge D B, Hajimiri A. Transmitter architectures based on near-field direct antenna modulation. IEEE J Solid-State Circ, 2008, 43: 2674–2692
Chen X M, Chen X F, Liu T. A unified performance optimization for secrecy wireless information and power transfer over interference channels. IEEE Access, 2017, 5: 12726–12736
Zou Y, Champagne B, Zhu W P, et al. Relay-selection improves the security-reliability trade-off in cognitive radio systems. IEEE Trans Commun, 2015, 63: 215–228
Lee H, Eom S, Park J, et al. UAV-aided secure communications with cooperative jamming. IEEE Trans Veh Technol, 2018, 67: 9385–9392
Khuwaja A A, Chen Y, Zhao N, et al. A survey of channel modeling for UAV communications. IEEE Commun Surv Tut, 2018, 20: 2804–2821
Negi R, Goel S. Secret communication using artificial noise. In: Proceedings of IEEE Vehicular Technology Conference, 2005. 3: 1906–1910
Wu Y P, Wang J B, Wang J, et al. Secure transmission with large numbers of antennas and finite alphabet inputs. IEEE Trans Commun, 2017, 65: 3614–3628
Ding Y, Fusco V F. A vector approach for the analysis and synthesis of directional modulation transmitters. IEEE Trans Antenn Propagat, 2014, 62: 361–370
Shu F, Xu L, Wang J, et al. Artificial-noise-aided secure multicast precoding for directional modulation systems. IEEE Trans Veh Technol, 2018, 67: 6658–6662
Wan S M, Shu F, Lu J H, et al. Power allocation strategy of maximizing secrecy rate for secure directional modulation networks. IEEE Access, 2018, 6: 38794–38801
Shu F, Qin Y L, Liu T T, et al. Low-complexity and high-resolution DOA estimation for hybrid analog and digital massive MIMO receive array. IEEE Trans Commun, 2018, 66: 2487–2501
Shu F, Zhu W, Zhou X B, et al. Robust secure transmission of using main-lobe-integration-based leakage beamforming in directional modulation MU-MIMO systems. IEEE Syst J, 2018, 12: 3775–3785
Shu F, Wu X M, Hu J S, et al. Secure and precise wireless transmission for random-subcarrier-selection-based directional modulation transmit antenna array. IEEE J Sel Areas Commun, 2018, 36: 890–904
El Shafie A, Niyato D, Al-Dhahir N. Artificial-noise-aided secure MIMO full-duplex relay channels with fixed-power transmissions. IEEE Commun Lett, 2016, 20: 1591–1594
Lee J H. Full-duplex relay for enhancing physical layer security in multi-hop relaying systems. IEEE Commun Lett, 2015, 19: 525–528
Chen G J, Gong Y, Xiao P, et al. Physical layer network security in the full-duplex relay system. IEEE Trans Inform Forensic Secur, 2015, 10: 574–583
Li Y Z, Tao C, Liu L, et al. Energy-efficiency-aware relay selection in distributed full duplex relay network with massive MIMO. Sci China Inf Sci, 2017, 60: 022309
Li S, Li Q, Shao S H. Robust secrecy beamforming for full-duplex two-way relay networks under imperfect channel state information. Sci China Inf Sci, 2018, 61: 022307
Shu F, Wang M M, Wang Y X, et al. An efficient power allocation scheme for leakage-based precoding in multi-cell multiuser MIMO downlink. IEEE Commun Lett, 2011, 15: 1053–1055
Acknowledgements
This work was supported in part by National Natural Science Foundation of China (Grant Nos. 61771244, 61501238, 61702258, 61472190, 61801453, 61271230), in part by Open Research Fund of National Key Laboratory of Electromagnetic Environment, China Research Institute of Radiowave Propagation (Grant No. 201500013), in part by Jiangsu Provincial Science Foundation (Grant No. BK20150786), in part by Specially Appointed Professor Program in Jiangsu Province, 2015, in part by Fundamental Research Funds for the Central Universities (Grant No. 30916011205), and in part by Open Research Fund of National Mobile Communications Research Laboratory, Southeast University, China (Grant Nos. 2017D04, 2013D02).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Lu, Z., Sun, L., Zhang, S. et al. Optimal power allocation for secure directional modulation networks with a full-duplex UAV user. Sci. China Inf. Sci. 62, 80304 (2019). https://doi.org/10.1007/s11432-019-9928-5
Received:
Revised:
Accepted:
Published:
DOI: https://doi.org/10.1007/s11432-019-9928-5