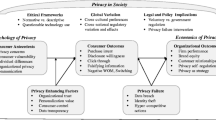
Abstract
Increasing quantities of medical and health data are being created outside of HIPAA protection, primarily by patients. Data sources are varied, including the use of credit cards for physician visit and medication co-pays, Internet searches, email content, social media, support groups, and mobile health apps. Most medical and health data not covered by HIPAA are controlled by third party data brokers and Internet companies. These companies combine this data with a wide range of personal information about consumer daily activities, transactions, movements, and demographics. The combined data are used for predictive profiling of individual health status, and often sold for advertising and other purposes. The rapid expansion of medical and health data outside of HIPAA protection is encroaching on privacy and the doctor-patient relationship, and is of particular concern for psychiatry. Detailed discussion of the appropriate handling of this medical and health data is needed by individuals with a wide variety of expertise.
Similar content being viewed by others
References
Papers of particular interest, published recently, have been highlighted as: • Of importance •• Of major importance
Mechanic D, Meyer S. Concepts of trust among patients with serious illness. Soc Sci Med. 2000;51(5):657–68.
Narayanan A, Shmatikov V. Myths and fallacies of personally identifiable information. Commun ACM. 2010;53(6):24–6.
Ohm P. Broken promises of privacy: responding to the surprising failure of anonymization. UCLA Law Rev. 2010;57(6).
World Economic Forum. Personal data: the emergence of a new asset class. 2011. http://www.weforum.org/reports/personal-data-emergence-new-asset-class. Accessed 31 May 2014.
Cukier KN, Mayer-Schoenberger V. The rise of big data: how it’s changing the way we think about the world. Foreign Aff. 2013. http://www.foreignaffairs.com/articles/139104/kenneth-neil-cukier-and-viktor-mayer-schoenberger/the-rise-of-big-data. Accessed 31 May 2014.
IDC. The digital universe in 2020: big data, bigger digital shadows, and the biggest growth in the far east - United States. 2013. http://www.emc.com/collateral/analyst-reports/idc-digital-universe-united-states.pdf. Accessed 31 May 2014.
Guardian. A Guardian guide to your metadata. 2013. http://www.theguardian.com/technology/interactive/2013/jun/12/what-is-metadata-nsa-surveillance#meta=0000000. Accessed 31 May 2014. Clear tables on what is included in metadata for email, phone, Facebook, Twitter, search and web browser.
IDC. The diverse and exploding digital universe. 2008. http://www.emc.com/collateral/analyst-reports/diverse-exploding-digital-universe.pdf. Accessed 31 May 2014.
IDC. The digital universe decade - are you ready? 2010. http://www.emc.com/collateral/analyst-reports/idc-digital-universe-are-you-ready.pdf. Accessed 31 May 2014.
Cohen JE. What privacy is for (November 5, 2012). Harv Law Rev. 2013;126.
Norberg PA, Horne DR, Horne DA. The privacy paradox: personal information disclosure intentions versus behaviors. J Consum Aff. 2007;41(1):100–26.
McDonald AM, Cranor LF. Americans’ attitudes about internet behavioral advertising practices. In: Proceedings of the 9th annual ACM workshop on privacy in the electronic society. ACM; 2010. 63–72.
Bauer C, Korunovska J, Spiekermann, S. On the value of information–what facebook users are willing to pay. In: 20th European Conference on Information Systems proceedings (ECIS 2012). 2012.
Hann IH, Hui KL, Lee SYT, et al. Overcoming online information privacy concerns: an information-processing theory approach. J Manag Inf Syst. 2007;24(2):13–42.
Abelson H, Leeden K, Lewis H. Blown to bits: your life, liberty, and happiness after the digital explosion. Addison-Wesley Professional; 2008. For those wanting background information, excellent introduction to the digital world.
Black A, Gen Y. Gen Y: who they are and how they learn. Educ Horiz. 2010;88(2):92–101.
Newman J. Google’s Schmidt roasted for privacy comments. PC World. 2009. http://www.pcworld.com/article/184446/googles_schmidt_roasted_for_privacy_comments.html. Accessed 31 May 2014.
Johnson B. Privacy no longer a social norm, says Facebook founder. The Guardian. 2010. http://www.theguardian.com/technology/2010/jan/11/facebook-privacy. Accessed 31 May 2014.
Shapiro G. Op-Ed: don’t let privacy concerns stifle innovation. Nextgov.com. 2013. http://www.nextgov.com/emerging-tech/2013/06/op-ed-dont-let-privacy-concerns-stifle-innovation/65195/. Accessed 31 May 2014.
Kaye J. The tension between data sharing and the protection of privacy in genomics research. Annu Rev Genomics Hum Genet. 2012;13:415–31.
Lane J, Schur C. Balancing access to health data and privacy: a review of the issues and approaches for the future. Health Serv Res. 2010;45(5 Pt 2):1456–67.
Shachak A, Jadad AR. Electronic health records in the age of social networks and global telecommunications. JAMA. 2010;303(5):452–3.
Groves P, Kayyali B, Knott D, et al. The ‘big data’ revolution in healthcare: accelerating value and innovation. McKinsey & Company; 2013. http://www.mckinsey.com/insights/health_systems_and_services/the_big-data_revolution_in_us_health_care. Accessed 31 May 2014.
Institute of Medicine. Best care at lower cost. The path to continuously learning health care in America. 2012. http://www.iom.edu/~/media/Files/Report%20Files/2012/Best-Care/Best%20Care%20at%20Lower%20Cost_Recs.pdf. Accessed 31 May 2014.
Murdoch TB, Detsky AS. The inevitable application of big data to health care. JAMA. 2013;309(13):1351–2.
Swan M. The quantified self: fundamental disruption in big data science and biological discovery. Big Data. 2013;1:85–99.
Ramirez E. How can we get more meaning out of our data? Quantified Self knowledge through numbers. 2013. http://quantifiedself.com/2013/08/how-can-we-get-more-meaning-out-of-our-data/ Accessed 31 May 2014.
Government Accountability Office. Information resellers: consumer privacy framework needs to reflect changes in technology and the marketplace. 2013. http://www.gao.gov/assets/660/658151.pdf. Accessed 31 May 2014.
Dixon P, Gellman R. The scoring of America: how secret consumer scores threaten your privacy and your future. World Privacy Forum. 2014. http://www.worldprivacyforum.org/2014/04/wpf-report-the-scoring-of-america-how-secret-consumer-scores-threaten-your-privacy-and-your-future/. Accessed 31 May 2014. A review of consumer scoring, describing scores and rankings created from consumer data such as for health, financial, identity and authentication.
Federal Trade Commission. Data brokers: a call for transparency and accountability. 2014. http://www.ftc.gov/system/files/documents/reports/data-brokers-call-transparency-accountability-report-federal-trade-commission-may-2014/140527databrokerreport.pdf Accessed 31 May 2014.
Monteith S, Glenn T, Bauer M. Searching the internet for health information about bipolar disorder: some cautionary issues. Int J Bipolar Disord. 2013;1:22.
Sheehan KB. In poor health: an assessment of privacy policies at direct-to-consumer web sites. J Public Policy Mark. 2005;24(2):273–83.
Mackey TK, Yagi N, Liang BA. Prescription drug coupons: evolution and need for regulation in direct-to-consumer advertising. Res Soc Adm Pharm. 2014;10(3):588–94.
Fox S, Duggan M. Health online. Pew Res. 2013. http://www.pewinternet.org/Reports/2013/Health-online.aspx Accessed 31 May 2014.
Krishnamurthy B, Naryshkin K, Wills C. Privacy leakage vs. protection measures: the growing disconnect. In: Web 2.0 Security and Privacy Workshop, 2011. http://www2.research.att.com/~bala/papers/. Accessed 31 May 2014.
Huesch MD. Privacy threats when seeking online health information. JAMA Intern Med. 2013;173(19):1838–9.
Pwc. Social media “likes” healthcare: from marketing to social business. 2013. www.pwc.com/us/en/health-industries/publications/health-care-social-media.jhtml. Accessed 31 May 2014.
Mayer J, Mutchler P. MetaPhone: the sensitivity of telephone metadata. http://webpolicy.org/2014/03/12/metaphone-the-sensitivity-of-telephone-metadata/. Accessed 31 May 2014.
Lazarus D. CVS thinks $50 is enough reward for giving up healthcare privacy. Los Angeles Times. 2013. http://www.latimes.com/business/la-fi-lazarus-20130816,0,6519110,full.column. Accessed 31 May 2014.
Valentino-DeVries J, Singer-Vine J. They know what you’re shopping for. Wall Str J. 2012. http://online.wsj.com/news/articles/SB10001424127887324784404578143144132736214#printMode.
Tudor ML. Protecting privacy of medical records of employees and job applicants in the digital era under the Americans with Disabilities Act. North Ky Law Rev. 2013;40:635–65.
Dickson V. Offshore health record storage may pose privacy risks. Mod Healthc. 2014. http://www.modernhealthcare.com/article/20140418/blog/304189995. Accessed 31 May 2014.
Hooley S, Sweeney L. Survey of publicly available state health databases. Harvard University Data Privacy Lab. 1064-1. 2013. http://privacytools.seas.harvard.edu/files/privacytools/files/1075-1.pdf.
Lowe SA, Ólaighin G. Monitoring human health behaviour in one’s living environment: a technological review. Med Eng Phys. 2014;36(2):147–68. Review of technologies used for behavioral monitoring.
Dolan B. Report:13K iPhone consumer health apps in 2012. MobileHealthNews. 2012. http://mobihealthnews.com/13368/report-13k-iphone-consumer-health-apps-in-2012/. Accessed 31 May 2014.
IMS. Patient apps for improved healthcare from novelty to mainstream. 2013. http://www.imshealth.com/portal/site/imshealth/menuitem.762a961826aad98f53c753c71ad8c22a/?vgnextoid=e0f913850c8b1410VgnVCM10000076192ca2RCRD. Accessed 31 May 2014.
Landman Z. Debunking the most common myths about HIPAA. mHealthnews.com. 2013. http://www.mhealthnews.com/news/debunking-most-common-myths-about-hipaa?single-page=true. Accessed 31 May 2014.
Marcus AD, Weaver C. Heart gadgets test privacy-law limits. Wall Str J. 2012. http://online.wsj.com/news/articles/SB10001424052970203937004578078820874744076 Accessed 31 May 2014.
Privacy Rights Clearinghouse. Technical analysis of data practices and privacy risks of 43 popular mobile health and fitness applications. 2013. https://www.privacyrights.org/mobile-medical-apps-privacy-technologist-research-report.pdf. Accessed 31 May 2014.
President’s Council of Advisors on Science and Technology. Big data and privacy: a technological Perspective. 2014. http://www.whitehouse.gov/sites/default/files/microsites/ostp/PCAST/pcast_big_data_and_privacy_-_may_2014.pdf.
Fernandez-Luque L, Elahi N, Grajales FJ. An analysis of personal medical information disclosed in youtube videos created by patients with multiple sclerosis. In: Adlassnig K-P, et al. (Eds.) Medical Informatics in a United and Healthy Europe: Proceedings of MIE 2009, the XXII International Congress of the European Federation for Medical Informatics. IOS Press; 2009. 150:292.
US Senate Committee on Commerce, Science, and Transportation. A review of the data broker industry: collection, use, and sale of consumer data for marketing purposes. 2013. http://www.commerce.senate.gov/public/?a=Files.Serve&File_id=0d2b3642-6221-4888-a631-08f2f255b577. A clearly written review of the data broker industry.
Armour S. Data Brokers come under fresh scrutiny. Wall Str J. 2014. http://online.wsj.com/news/articles/SB10001424052702303874504579377164099831516.
Michael K, Clarke R. Location and tracking of mobile devices: Überveillance stalks the streets. Comput Law Secur Rev. 2013;29(3):216–28. A review of how mobile devices are used for location tracking.
Steel E. Acxiom to create ‘master profiles’ tying offline and online data. Financ Times. 2013. http://www.ft.com/cms/s/0/151d940e-2431-11e3-8905-00144feab7de.html. Accessed 31 May 2014.
Epsilon. Consumer data and data cards - Ailments/health. http://lists.epsilon.com/market;jsessionid=E46C0F404A2FCB1EF6F0A24EE0DEC61A?page=research/datacard&id=91407. Accessed 31 May 2014.
TargetSource. U.S. health and ailment database. http://lists.nextmark.com/market;jsessionid=1E89AC694197AB78C356A7B6672FD5BA?page=order/online/datacard&id=210939. Accessed 31 May 2014.
DMDatabase.com. Ailments mailing list. http://dmdatabases.com/databases/consumer-mailing-lists/ailments-lists. Accessed 31 May 2014.
Garla S, Hopping A, Monaco R, Rittman R. What do your consumer habits say about your health? Using third-party data to predict individual health risk and costs. SAS Institute. 2013. http://support.sas.com/resources/papers/proceedings13/170-2013.pdf.
Acxiom Update Newsletter. Stay current with Acxiom product and industry alerts. 2009. http://www.mktgservices.com/marketing/newsletter/myAcxiomUpdate/0509/v1/acxiom-alerts.html. Accessed 31 May 2014.
FICO. Medication adherence score. http://www.fico.com/en/products/fico-medication-adherence-score/. Accessed 31 May 2014.
Scism L, Maremont M. Insurers test data profiles to identify risky clients. Wall Str J. 2010. http://online.wsj.com/news/articles/SB10001424052748704648604575620750998072986. Accessed 31 May 2014.
Hill T. Predictive modeling in life insurance underwriting. Society of Actuaries. The Future of Preferred Underwriting. 2013. http://www.soa.org/search.aspx?searchterm=tim%20hill%202013. Accessed 31 May 2014.
Network Advertising Initiative. Study finds behaviorally-targeted ads more than twice as valuable, twice as effective as non-targeted online ads. 2010. http://www.networkadvertising.org/pdfs/NAI_Beales_Release.pdf. Accessed 31 May 2014.
Acxiom Annual Report. 2013. http://acxiom.com/wp-content/uploads/2013/09/2013-Annual-Report.pdf. Accessed 31 May 2014.
De Choudhury M, Counts S, Horvitz E. Major life changes and behavioral markers in social media: case of childbirth. In: Proceedings of the 2013 conference on Computer supported cooperative work. ACM; 2013. 1431–42.
Golbeck J, Robles C, Turner K. Predicting personality with social media. In: CHI’11 extended abstracts on human factors in computing systems. ACM; 2011. 253–62.
Marcus B, Machilek F, Schütz A. Personality in cyberspace: personal Web sites as media for personality expressions and impressions. J Pers Soc Psychol. 2006;90(6):1014–31.
Bachrach Y, Kosinski M, Graepel T, et al. Personality and patterns of Facebook usage. In: Proceedings of the 3rd Annual ACM Web Science Conference. ACM; 2012. 24–32.
Moreno MA, Jelenchick LA, Egan KG, et al. Feeling bad on Facebook: depression disclosures by college students on a social networking site. Depress Anxiety. 2011;28(6):447–55.
Kosinski M, Stillwell D, Graepel T. Private traits and attributes are predictable from digital records of human behavior. Proc Natl Acad Sci U S A. 2013;110(15):5802–5. Example of how a range of sensitive personal attributes can be predicted from Facebook Likes.
Martin EA, Bailey DH, Cicero DC, et al. Social networking profile correlates of schizotypy. Psychiatry Res. 2012;200(2–3):641–6.
Duhigg C. How companies learn your secrets. New York Times 2,16,2012. http://www.nytimes.com/2012/02/19/magazine/shopping-habits.html?ref=general&src=me&pagewanted=all&_r=0. Accessed 31 May 2014.
Crawford K, Schultz J. Big data and due process: toward a framework to redress predictive privacy harms. Boston Coll Law Rev. 2014. http://bclawreview.org/files/2014/01/03_crawford_schultz.pdf.
Terry N. Protecting patient privacy in the age of big data. Univ Missouri-Kansas City Law Rev. 2012;81(2). http://ssrn.com/abstract=2153269.
Walker J. Data mining to recruit sick people. Wall Str J. 2013. http://online.wsj.com/news/articles/SB10001424052702303722104579240140554518458. Accessed 31 May 2014.
Lupton D. The commodification of patient opinion: the digital patient experience economy in the age of big data. Sociol Health Illn. 2014. doi:10.1111/1467-9566.12109.
Li J. Privacy policies for health social networking sites. J Am Med Inform Assoc. 2013;20(4):704–7.
Weigmann K. Health research 2.0: the use in research of personal fitness or health data shared on social network raises both scientific and ethical concerns. EMBO Rep. 2014;15(3):223–6.
Williams J. Social networking applications in health care: threats to the privacy and security of health information. In: Proceedings of the 2010 ICSE Workshop on Software Engineering in Health Care. ACM; 2010. 39–49.
Ball DE, Tisocki K, Herxheimer A. Advertising and disclosure of funding on patient organisation websites: a cross-sectional survey. BMC Public Health. 2006;6:201.
Treato. Treato: patient intelligence based on real-life experiences. http://treato.com/about/. Accessed 31 May 2014.
Tene O, Polonetsky J. Privacy in the age of big data: a time for big decisions. Stanf Law Rev Online. 2012;64:63.
Center for Democracy and Technology. Rethinking the role of consent in protecting health information privacy. 2009. https://www.cdt.org/files/pdfs/20090126Consent.pdf. Accessed 31 May 2014.
Turow J, Hoofnagle CJ, Mulligan DK, et al. The Federal Trade Commission and consumer privacy in the coming decade. ISJLP. 2007;3:723. http://scholarship.law.berkeley.edu/cgi/viewcontent.cgi?article=1934&context=facpubs. Accessed 31 May 2014.
Determann L. Social media privacy: a dozen myths and facts. Stan Tech L Rev. 2012. 7–10. http://stlr.stanford.edu/2012/07/social-media-privacy/. Accessed 31 May 2014.
Brandimarte L, Acquisti A, Loewenstein G. Misplaced confidences privacy and the control paradox. Soc Psychol Personal Sci. 2013;4(3):340–7.
El Emam K, Moher E. Privacy and anonymity challenges when collecting data for public health purposes. J Law Med Ethics. 2013;41 Suppl 1:37–41.
Savla P, Martino LD. Content analysis of privacy policies for health social networks.” IEEE International Symposium on Policies for Distributed Systems and Networks. 2012;94–101.
Anton A, Earp JB, Vail M, et al. HIPAA’s effect on web site privacy policies. IEEE Secur Priv. 2007;45–52.
Milne GR, Culnan MJ, Greene H. A longitudinal assessment of online privacy notice readability. J Public Policy Mark. 2006;25(2 (Fall)):238–49.
Graber MA, D’Alessandro DM, Johnson-West J. Reading level of privacy policies on Internet health Web sites. J Fam Pract. 2002;51(7):642–5.
Ryan C, Siebens J. Educational attainment in the United States: 2009. U.S. Census Bureau. 2012. http://www.census.gov/prod/2012pubs/p20-566.pdf.
Breese P, Burman W. Readability of notice of privacy forms used by major health care institutions. JAMA. 2005;293(13):1593–4.
Gralton E, Sher M, Lopez CD. Information and readability issues for psychiatric patients: e-learning for users. Psychiatr Bull. 2010;34:376–80.
Goldston DB, Walsh A, Mayfield Arnold E, et al. Reading problems, psychiatric disorders, and functional impairment from mid- to late adolescence. J Am Acad Child Adolesc Psychiatry. 2007;46(1):25–32.
Federal Trade Commission. Mobile privacy disclosures. Building trust through transparency. 2013. http://www.ftc.gov/sites/default/files/documents/reports/mobile-privacy-disclosures-building-trust-through-transparency-federal-trade-commission-staff-report/130201mobileprivacyreport.pdf1.
Carrión Señor I, Fernández-Alemán JL, Toval A. Are personal health records safe? A review of free web-accessible personal health record privacy policies. J Med Internet Res. 2012;14(4):e114.
Hargittai E. Digital na(t)ives? variation in internet skills and uses among members of the “Net Generation”. Sociol Inq. 2010;80:92–113.
Park YJ. Digital literacy and privacy behavior online. Commun Res. 2013;40(2):215–36.
Leon P, Ur B, Shay R, et al. Why Johnny can’t opt out: a usability evaluation of tools to limit online behavioral advertising. In: Proceedings of the SIGCHI Conference on Human Factors in Computing Systems. ACM; 2012. 589–98.
Solove DJ. HIPAA turns 10. J AHIMA. 2013;84(4):22–8.
Ponemon. Fourth Annual Benchmark Study on Patient Privacy and Data Security. 2014. http://www.ponemon.org/blog/fourth-annual-benchmark-study-on-patient-privacy-and-data-security. Accessed 31 May 2014.
McCann E. HIPAA data breaches climb 138 percent. Healthcare IT News. 2014. http://www.healthcareitnews.com/news/hipaa-data-breaches-climb-138-percent.
US Department of Health and Human Services. Breaches affecting 500 or more individuals. http://www.hhs.gov/ocr/privacy/hipaa/administrative/breachnotificationrule/breachtool.html.
Redspin. Breach report 2013: protected health information (PHI). 2014. http://www.redspin.com/resources/whitepapers-datasheets/Request-2013-Breach-Report-Protected-Health-Information-PHI-Redspin.php.
Johnson ME, Willey ND. Will HITECH heal patient data hemorrhages? In: System Sciences (HICSS), 2011 44th Hawaii International Conference on IEEE. 2011. 1–10.
Figg WC, Kam HJ. Medical information security. Int J Secur (IJS). 2011;5(1):22.
KrebsonSecurity. Data broker giants hacked by id theft service. 2013. http://krebsonsecurity.com/2013/09/data-broker-giants-hacked-by-id-theft-service/. Accessed 31 May 2014.
Schwartz MJ. Experian breach fallout: ID theft nightmares continue. Inf Week. 2013. http://www.darkreading.com/risk-management/experian-breach-fallout-id-theft-nightmares-continue/d/d-id/1112058? Accessed 31 May 2014.
Rosencrance L. Acxiom database hacked. Computerworld. 2003. http://www.computerworld.com/s/article/83854/Acxiom_database_hacked. Accessed 31 May 2014.
Federal Trade Commission. Health privacy. http://www.business.ftc.gov/documents/bus56-complying-ftcs-health-breach-notification-rule. Accessed 31 May 2014.
Harris Interactive. Many U.S. adults are satisfied with use of their personal health information. 2007. http://www.harrisinteractive.com/vault/Harris-Interactive-Poll-Research-Health-Privacy-2007-03.pdf. Accessed 31 May 2014.
California HealthCare Foundation. Consumers and health information technology: a national survey. 2010. http://www.chcf.org/publications/2010/04/consumers-and-health-information-technology-a-national-survey. Accessed 31 May 2014.
California HealthCare Foundation. National consumer health privacy survey. 2005. http://www.chcf.org/~/media/MEDIA%20LIBRARY%20Files/PDF/C/PDF%20ConsumerPrivacy2005ExecSum.pdf Accessed 31 May 2014.
Ancker JS, Silver M, Miller MC, et al. Consumer experience with and attitudes toward health information technology: a nationwide survey. J Am Med Inform Assoc. 2013;20(1):152–6.
National Partnership for Women and Families. Making IT meaningful: how consumers value and trust health IT. 2012. http://go.nationalpartnership.org/site/DocServer/HIT_Making_IT_Meaningful_National_Partnership_February_2.pdf.
Westin AF. Institute of Medicine project survey findings on health research and privacy. 2007. http://www.iom.edu/~/media/Files/Activity%20Files/Research/HIPAAandResearch/AlanWestinIOMsrvyRept.ashx. Accessed 31 May 2014.
Employee Benefit Research Institute. Health confidence survey. 2008. http://www.ebri.org/publications/notes/index.cfm?fa=notesDisp&content_id=3987. Accessed 31 May 2014.
Markle. Survey finds Americans want electronic personal health information to improve own health care. 2006. http://www.markle.org/publications/1214-survey-finds-americans-want-electronic-personal-health-information-improve-own-hea. Accessed 31 May 2014.
Deloitte. Survey of U.S. health care consumers: the performance of the health care system and health care reform. 2012. https://www.deloitte.com/view/en_US/us/Industries/US-federal-government/center-for-health-solutions/517f54995c0e7310VgnVCM2000001b56f00aRCRD.htm. Accessed 31 May 2014.
Agaku IT, Adisa AO, Ayo-Yusuf OA, et al. Concern about security and privacy, and perceived control over collection and use of health information are related to withholding of health information from healthcare providers. J Am Med Inform Assoc. 2014;21(2):374–8.
NPR/Kaiser Family Foundation. The public and the health care delivery system. 2009. http://www.npr.org/documents/2009/apr/nprpoll_topline.pdf. Accessed 31 May 2014.
Fair Warning. How privacy considerations drive patient decisions and impact patient care outcomes. 2011. http://www.fairwarning.com/whitepapers/2011-09-WP-US-PATIENT-SURVEY.pdf.
Lowes R. Fear of data theft blunts public acceptance of EHRS. Medscape. 2012. http://www.medscape.com/viewarticle/769778.
Flynn HA, Marcus SM, Kerber K, et al. Patients’ concerns about and perceptions of electronic psychiatric records. Psychiatr Serv. 2003;54(11):1539–41.
Office of National Coordinator for HIT. Health care providers’ role in protecting EHRs: implications for consumer support of EHRs, HIE and patient-provider communication. 2014. http://www.healthit.gov/sites/default/files/022414_hit_attitudesaboutprivacydatabrief.pdf.
Sankar P, Moran S, Merz JF, et al. Patient perspectives of medical confidentiality: a review of the literature. J Gen Intern Med. 2003;18:659–69.
Compliance with Ethics Guidelines
Conflict of Interest
Scott Monteith declares no conflict of interest.
Tasha Glenn shares a patent for ChronoRecord software but does not receive any financial compensation from The ChronoRecord Association, a 501(c)(3) nonprofit organization.
Human and Animal Rights and Informed Consent
This article does not contain any studies with human or animal subjects performed by any authors.
Author information
Authors and Affiliations
Corresponding author
Additional information
This article is part of the Topical Collection on Psychiatry in the Digital Age
Rights and permissions
About this article
Cite this article
Glenn, T., Monteith, S. Privacy in the Digital World: Medical and Health Data Outside of HIPAA Protections. Curr Psychiatry Rep 16, 494 (2014). https://doi.org/10.1007/s11920-014-0494-4
Published:
DOI: https://doi.org/10.1007/s11920-014-0494-4