Abstract
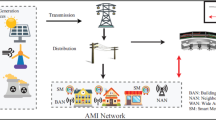
Advanced Metering Infrastructure (AMI) is enabling technology for smart grid and it act as a bridge between cyber and physical systems of the smart grid. The major parts of AMI are cyber systems; hence it’s more vulnerable to attacks. The normal security protection scheme is not suitable for AMI because it consists of computation restricted components such as smart meters. The AMI networks also increase the challenges in the design of common protocol for end-to-end security (E2S) due to interoperability of its components. Data transfer in the AMI system requires E2S protection and security is one of the most challenging in AMI components development and deployment. Motivated by these limitations, the E2S scheme for AMI smart grid is proposed. In the proposed scheme includes the following properties. (i) Protracted publisher key per smart meter that are given by the Head End System (ii) Encryption key for each message sent from smart meter is derived from the publisher key (iii) Authentication of every message sent that consist of identity of smart meter such as Message Authentication Code (MAC). Compare with the existing end-to-end security schemes, the proposed scheme improves the E2S in terms of confidentiality, integrity and authentication with increasing scalability.




Similar content being viewed by others
References
Alohali B, KashifKifayat QS, Hurst W (2015) A Survey on cryptography key management schemes for smart grid. J Comput Sci Appl 3(3A):27–39
Andreadou N, Kotsakis E, Masera M (2018) Smart meter traffic in a real LV distribution network. Energies. https://doi.org/10.3390/en11051156
Badra M, Hajjeh I (2009) ECDHE_PSK cipher suites for transport layer security (TLS). Internet Engineering Task Force, RFC5489, Fremont, CA, USA, pp 1–7. https://doi.org/10.17487/RFC5489
Balaji VR, Maheswaran S, Babu MR, Kowsigan M, Prabhu E, Venkatachalam K (2020) Combining statistical models using modified spectral subtraction method for embedded system. Microproces Microsyst 73:102957
Barker EB, Johnson D, Smid M (2006) Recommendation for pair-wise key establishment schemes using discrete logarithm cryptography. NIST Special Publication, Gaithersburg
Baugher M, McGrew D, Naslund M, Carrara E, Norrman K (2004) The secure real-time transport protocol (SRTP). IETF, RFC 3711, Fremont, CA, USA, pp 1–56. https://doi.org/10.17487/RFC3711
Benmalek M, Challal Y (2015) eSKAMI: efficient and scalable multi-group key management for advanced metering infrastructure in smart grid. In: Proceedings of the 2015 IEEE Trustcom BigDataSE/ISPA, vol 1. IEEE, pp 782–789
Benmalek M, Challal Y (2016) MK-AMI: efficient multi-group key management scheme for secure communications in AMI systems. In: IEEE wireless communications and networking conference, pp 1–6
Das S, Ohba Y, Kanda M, Famolari D, Das SK (2012) A key management framework for AMI networks in smart grid. IEEE Commun Mag 50(8):30–37
Dietrich D, Bruckner D, Zucker G, Palensky P (2010) Communication and computation in buildings: a short introduction and overview. IEEE Trans Ind Electron 57(11):3577–3584
Garrido JM (2019) High-level specification and modeling of cyber-physical systems. In: ACM southeastern conference, pp 245–248. https://doi.org/10.1145/3299815.3314469
Ghosal A, Conti M (2018) Key management systems for smart grid advanced metering infrastructure: A Survey arXiv: 1806.00121v1.
Kim JY, Choi HK (2012) An efficient and versatile key management protocol for secure smart grid communications. In: Proceedings on IEEE wireless communication networking conference, Paris, pp 1823–1828
Kim Y-J, Lee J, Atkinson G, Kim H, Thottan M (2012) SeDAX: a secure, resilient and scalable platform. IEEE J Sel Areas Commun 30(6):1119–1136
Kim Y, Kolesnikov V, Thottan M (2018) Resilient end-to-end message protection for cyber-physical system communications. IEEE Trans Smart Grid. https://doi.org/10.1109/TSG.2016.2613545
Kuzlu M, Pipattanasomporn M, Rahman S (2014) Communication network requirements for major smart grid applications in HAN, NAN and WAN. Comput Netw 67:74–88
Liu N, Chen J, Zhu L, Zhang J, He Y (2012) A key management scheme for secure communications of advanced metering infrastructure in smart Grid. IEEE Trans Ind Electron 60:4746–4756
London Government Sample Smart Meter Data. https://data.london.gov.uk/dataset/smartmeter-energy-use-data-in-londonhouseholds. Accessed 01 Nov 2019
Long X, Tipper D, Qian Y (2016) A key management architecture and protocols for secure smart grid communications. Secur Commun Netw. https://doi.org/10.1002/sec.1564
Nabeel M, Ding X, Seo S-H, Bertino E (2015) Scalable end-to-end security for advanced metering infrastructures. J Inf Syst 53:213–223
Neuman C, Yu T, Hartman S, Raeburn K (2005) The kerberos network authentication service (V5). IETF RFC 4120, pp 1–138. https://doi.org/10.17487/RFC4120
Perrig A, Canetti R, Song D, Tygar JD (2001) Efficient and secure source authentication for multicast. Netw Distrib Syst Secur Symp NDSS 1:35–46
Ponnan S, Saravanan AK, Iwendi C, Ibeke E, Srivastava G (2021) An artificial intelligence based quorum system for the improvement of the lifespan of sensor networks. IEEE Sens J 21(15):17373–17385
Rao V, Prema KV (2020) A review on lightweight cryptography for Internet-of-Things based applications. J Ambient Intell Human Comput. https://doi.org/10.1007/s12652-020-02672-x
Song JH, Poovendran R, Lee J, Iwata T (2006) The AES-CMAC algorithm. Internet Engineering Task Force, RFC 4493, Fremont, CA, USA, pp 1–20. https://doi.org/10.17487/RFC4493
Suresh P, Saravanakumar U, Iwendi C, Mohan S, Srivastav G (2021) Field-programmable gate arrays with low power vision system using dynamic switching. Comput Elect Eng 90:106996
Wang J, Leung VCM (2011) A survey of technical requirements and consumer application standards for IP-based smart grid AMI network. In: IEEE international conference on information networking, pp 114–119. https://doi.org/10.1109/ICOIN.2011.5723144
Wong CK, Gouda M, Lam SS (2000) Secure group communications using key graphs. IEEE/ACM Trans Netw. https://doi.org/10.1109/90.836475
Wu D, Zhou C (2011) Fault-tolerant and scalable key management for smart grid. IEEE Trans Smart Grid 2(2):375–381
Wu L, Wang J, Zeadally S, He D (2019) Anonymous and efficient message authentication scheme for smart grid. Secur Commun Netw 2019:4836016. https://doi.org/10.1155/2019/4836016
Xia J, Wang Y (2012) Secure key distribution for the smart grid. IEEE Trans Smart Grid 3:1437–1443
Yan Y, Qian Y, Sharif H (2011) A secure and reliable in-network collaborative communication scheme for advanced metering infrastructure in smart grid. In: IEEE wireless communications and networking conference, pp 909–914. https://doi.org/10.1109/WCNC.2011.5779257
Zimmermann P, Johnston A, Callas J (2011) ZRTP: media path key agreement for unicast secure RTP. Internet Engineering Task Force, RFC 6189, Fremont, CA, USA, pp 1–115. https://doi.org/10.17487/RFC6189
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kalidass, J., Purusothaman, T. & Suresh, P. Enhancement of end-to-end security in advanced metering infrastructure. J Ambient Intell Human Comput (2021). https://doi.org/10.1007/s12652-021-03409-0
Received:
Accepted:
Published:
DOI: https://doi.org/10.1007/s12652-021-03409-0