Abstract
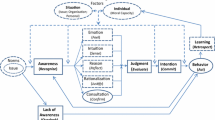
It is widely agreed that employee non-adherence to information security policies poses a major problem for organizations. Previous research has pointed to the potential of theories of moral reasoning to better understand this problem. However, we find no empirical studies that examine the influence of moral reasoning on compliance with information security policies. We address this research gap by proposing a theoretical model that explains non-compliance in terms of moral reasoning and values. The model integrates two well-known psychological theories: the Theory of Cognitive Moral Development by Kohlberg and the Theory of Motivational Types of Values by Schwartz. Our empirical findings largely support the proposed model and suggest implications for practice and research on how to improve information security policy compliance.


Similar content being viewed by others
Notes
Philosophers have defined moral conflicts in a variety of ways (Nagel, 1987; Hill, 1996; Mason, 1996), but consensus holds that in a moral conflict the moral agent should do A, but, simultaneously, should also do B. However, the agent cannot do both A and B.
References
Akers RL and Sellers CS (1994) Criminological Theories: Introduction, Evaluation, and Application. Roxbury Publishing, Los Angeles, CA.
Allport G (1963) Pattern and Growth in Personality. Holt, Rinehart & Winston, London.
Banerjee D, Cronan TP and Jones TW (1998) Modeling IT ethics: a study in situational ethics. MIS Quarterly 22 (1), 31–60.
Bardi A and Schwartz SH (2003) Values and behaviour: strength and structure of relations. Personality and Social Psychology Bulletin 29 (10), 1207–1220.
Bilsky W and Schwartz SH (1994) Values and personality. European Journal of Personality 8 (3), 161–181.
Blasi A (1980) Bridging moral cognition and moral action: a critical review of the literature. Psychological Bulletin 88 (1), 1–45.
Carpendale J and Krebs DL (1992) Situational variation in moral judgment: in a stage or on a stage? Journal of Youth and Adolescence 21 (2), 203–224.
Carpendale J and Krebs DL (1995) Variations in level of moral judgments as a function of type of dilemma and moral choice. Journal of Personality 63 (2), 289–313.
Colby A and Kohlberg L (1987) The Measurement of Moral Judgment, Vols. 1 and 2. Cambridge University Press, New York.
D'Arcy J, Hovav A and Galletta DF (2009) User awareness of security countermeasures and its impact on information systems misuse: a deterrence approach. Information Systems Research 20 (1), 79–98.
Denton K and Krebs K (1990) From the scene to the crime: the effect of alcohol and social context on moral judgment. Journal of Personality and Social Psychology 59 (2), 242–248.
Deutsch M (1985) Distributive Justice: A Social-Psychological Perspective. Yale University Press, New Haven.
Devos T, Spini D and Schwartz SH (2002) Conflicts among human values and trust in institutions. British Journal of Social Psychology 41 (4), 491–494.
deVries B and Walker LJ (1986) Moral reasoning and attitudes toward capital punishment. Developmental Psychology 22 (4), 509–513.
Emler N, Tarry H and St. James A (2007) Post-conventional moral reasoning and reputation. Journal of Research in Personality 41 (1), 76–89.
Feather NT (1990) Bridging the gap between values and actions. Recent applications of the expectancy-value model. In Handbook of Motivation and Cognition (HIGGINS ET and SORRENTINO RM, Eds), Vol. 2, pp 151–192, Guilford Press, New York.
Feather NT (1992) Values, valences, expectations, and actions. Journal of Social Issues 48 (2), 109–124.
Finne T (1996) The information security chain in a company. Computers & Security 15 (4), 297–316.
Greenberg J (2002) Who stole the money, and when? Individual and situational determinants of employee theft. Organizational Behavior and Human Decision Processes 89 (1), 985–1003.
Hair JF, Anderson RE, Tatham RL and Black WC (1998) Multivariate Data Analysis 5th edn, Prentice Hall, Englewood Cliffs, NJ.
Hare RM (1981) Moral Thinking: Its Levels, Methods, and Point. Clarendon Press, Oxford.
Harré R (1983) Personal Being. A Theory for Individual Psychology. Blackwell, Oxford.
Harrington SJ (1996) The effects of codes of ethics and personal denial of responsibility on computer abuse judgments and intentions. MIS Quarterly 20 (3), 257–278.
Helkama K, Uutela A, Pohjanheimo E, Salminen S, Koponen A and Rantanen-Väntsi L (2003) Moral reasoning and values in medical school: a longitudinal study in Finland. Scandinavian Journal of Educational Research 47 (4), 399–411.
Hill TE (1996) Moral dilemmas, gaps, and residues: a Kantian perspective. In Moral Dilemmas and Moral Theory (MASON HE, Ed), pp 167–198, Oxford University Press, New York.
Hoffman ML (1970) Moral development. In Carmichael's Manual of Child Psychology (MUSSEN PH, Ed), Vol. 2, 3rd edn, Wiley, Wiley, New York.
Hofstede G (1980) Culture's Consequences: International Differences in Work-related Values. Sage, London.
Inglehart R (1977) The Silent Revolution: Changing Values and Political Styles in Advanced Industrial Society. Princeton University Press, Princeton, NJ.
King PM and Mayhew MJ (2002) Moral judgment development in higher education: insights from the defining issues test. Journal of Moral Education 31 (3), 247–270.
Kohlberg L (1969) Stage and sequence: the cognitive-developmental approach to socialization. In Handbook of Socialization Theory and Research (GOSLIN D, Ed), pp 347–480, Rand McNally, Chicago.
Kohlberg L (1984) The Psychology of Moral Development. Harper & Row, New York.
Kristiansen CM and Hotte AM (1996) Morality and self: implications for the when and how of value-attitude-behaviour relations. In Ontario Symposium on Personality and Social Psychology: Values (SELIGMAN C, OLSON J and ZANNA MP, Eds), Vol. 8, pp 77–106, Erlbaum, Hillsdale, NJ.
Lan G, Gowing M, McMahon S, Rieger F and King N (2008) A study of the relationship between personal values and moral reasoning of undergraduate business students. Journal of Business Ethics 78 (1), 121–139.
Lee AS and Baskerville RL (2003) Generalizing generalizability in information systems research. Information Systems Research 14 (3), 221–243.
Lee J and Lee Y (2002) A holistic model of computer abuse within organizations. Information Management and Computer Security 10 (2), 57–63.
Lind G and Wakenhut R (1985) Testing for moral judgment competence. In Moral Development and the Social Environment (LIND G, HARTMANN HA and WAKENHUT R, Eds), pp 79–115, Precedent Publishing, Chicago.
Logsdon JM, Thompson JK and Reid RA (1994) Software piracy: is it related to level of moral judgment? Journal of Business Ethics 13 (11), 849–857.
Macquarrie J and Childress J (1986) A New Dictionary of Christian Ethics 2nd edn, SCM Press, London.
Malhotra N, Kim S and Agarwal J (2004) Internet users’ information privacy concerns (IUIPC): the construct, the scale, and a causal model. Information Systems Research 15 (4), 336–355.
Mason HE (1996) Introduction. In Moral Dilemmas and Moral Theory (MASON HE, Ed), pp 3–9, Oxford University Press, New York.
Moores T and Chang J (2006) Ethical decision making in software piracy: initial development and test of a four-component model. MIS Quarterly 30 (1), 167–180.
Myyry L (2002) Everyday value conflicts and integrative complexity of thought. Scandinavian Journal of Psychology 43 (5), 385–395.
Myyry L and Helkama K (2002) The role of value priorities and professional ethics training in moral sensitivity. Journal of Moral Education 31 (1), 35–50.
Nagel T (1987) The fragmentation of value. In Moral Dilemmas (GOWANS CW, Ed), pp 174–187, Oxford University Press, New York.
Narvaez D and Bock T (2002) Moral schemas and tacit judgment or how the defining issues test is supported by cognitive science. Journal of Moral Education 31 (3), 297–314.
Nunnally JC (1967) Psychometric Theory. McGraw-Hill, New York.
Pahnila S, Siponen MT and Mahmood A (2007) Which factors explain employees’ adherence to information security policies? An empirical study. Proceedings of the PACIS 2007, 3–6 July 2007, Auckland, New Zealand.
Popper K (1985) Popper Selections (MILLER DW, Ed), Princeton University Press, Princeton, NJ.
Puhakainen P (2006) Design theory for information security awareness. Unpublished Ph.D. Thesis, University of Oulu, Finland.
Renwick S and Emler N (1984) Moral reasoning and delinquent behaviour among students. British Journal of Social Psychology 23 (3), 281–283.
Rest JR (1979) Development in Judging Moral Issues. University of Minnesota, Minneapolis, MN.
Rest JR (1986) Moral Development: Advances in Research and Theory. Praeger, New York.
Rest JR (1994) Background: theory and research. In Moral Development in the Professions: Psychology and Applied Ethics (REST JR and NARVAEZ D, Eds), pp 1–26, Lawrence Erlbaum Associates, Hillsdale, NJ.
Rest JR, Thoma S and Edwards L (1997) Designing and validating a measure of moral judgment: stage preference and stage consistency approaches. Journal of Educational Psychology 89 (1), 5–28.
Rokeach M (1973) The Nature of Human Values. Free Press, New York.
Sagiv L and Schwartz SH (2000) Value priorities and subjective well-being: direct relations and congruity effects. European Journal of Social Psychology 30 (2), 177–198.
Sagiv L and Schwartz SH (2004) Values, intelligence and client behaviour in career counselling: a field study. European Journal of Psychology of Education 19 (3), 237–254.
Schwartz SH (1992) Universals in the content and structure of values: theoretical advances and empirical tests in 20 countries. In Advances in Experimental Social Psychology (ZANNA MP, Ed), Vol. 25, pp 1–65, Academic Press, San Diego, CA.
Schwartz SH (2007) Universalism values and the inclusiveness of our moral universe. Journal of Cross-Cultural Psychology 38 (6), 711–728.
Schwartz SH and Boehnke K (2004) Evaluating the structure of human values with confirmatory factor analysis. Journal of Research in Personality 38 (3), 230–255.
Schwartz SH, Lehmann A and Roccas S (1999) Multimethod probes of basic human values. In Social Psychology and Cultural Context (ADAMOPOULS J and KASHIMA Y, Eds), pp 107–123, Sage, Thousand Oaks, CA.
Schwartz SH and Rubel T (2005) Sex differences in value priorities: cross-cultural and multimethod studies. Journal of Personality and Social Psychology 89 (6), 1010–1028.
Schwartz SH, Sagiv L and Boehnke K (2000) Worries and values. Journal of Personality 68 (2), 309–346.
Silfver M, Helkama K, Lönnqist J and Verkasalo M (2008) The relation between value priorities and proneness to guilt, shame, and empathy. Motivation and Emotion 32 (2), 69–80.
Siponen M (2000) A conceptual foundation for organizational is security awareness. Information Management & Computer Security 8 (1), 31–41.
Siponen MT (2002) On the role of human morality in information system security: from the problems of descriptivism to non-descriptive foundations. In Ethical Issues of Information Systems (SALEHNIA A, Ed), Idea Group Publishing, Hershey, PA.
Siponen MT and Vartiainen T (2004) Unauthorized copying of software and levels of moral development: implications for research and practice. Information Systems Journal 14 (4), 387–407.
Siponen MT, Pahnila S and Mahmood A (2007) Employees’ adherence to information security policies: an empirical study. Proceedings of the IFIP SEC 2007, 14–16 May 2007, Sandton, Gauteng, South Africa.
Skoe EEA (1998) The ethic of care: issues in moral development. In Personality Development in Adolescence: A Cross National and Life Span Perspective (SKOE E and VON DER LIPPE A, Eds), pp 143–171, Routledge, London.
Straub DW (1990) Effective IS security: an empirical study. Information Systems Research 1 (3), 255–276.
Straub DW and Welke RJ (1998) Coping with systems risk: security planning models for management decision making. MIS Quarterly 22 (4), 441–469.
Trevino LK (1992) Experimental approaches to studying ethical-unethical behavior in organizations. Business Ethics Quarterly 2 (2), 121–136.
Vartiainen T (2007) Moral conflicts in teaching project work: a job burdened by role strains. Communications of the Association for Information Systems 20 (1), 681–711.
Verkasalo M, Daun Å and Niit T (1994) Universal values in Estonia, Finland and Sweden. Ethonologia Europaea 24 (2), 101–117.
Walker L, deVries B and Bichard SL (1984) The hierarchical nature of stages of moral development. Developmental Psychology 20 (5), 960–966.
Warkentin M, Shropshire J and Johnston AC (2007) The IT security adoption conundrum: an initial step towards validation of applicable measures. Proceedings of the 13th Americas Conference on Information Systems, Keystone, CO.
Weber J (1992) Scenarios in business ethics research: review, critical assessment, and recommendations. Business Ethics Quarterly 2 (2), 137–160.
Whitman ME and Mattord HJ (2008) Management of Information Security 2nd edn, Thompson Course Technology, Boston, MA.
Willison R (2006) Understanding the perpetration of employee computer crime in the organisational context. Information and Organization 16 (4), 304–324.
Author information
Authors and Affiliations
Corresponding author
Appendix A
Appendix A
The case: sharing personal user name and password with co-workers
Nurses use a healthcare information system. They obtain patient information from this system, and the nurses have to use a personal user name and password in the system. Many nurses find the use of personal user names and passwords to be cumbersome because they have difficulty remembering their passwords. One of the nurses wondered whether he should share his username and password with his co-workers.
Should the nurse share his password with his co-workers? (Mark only one answer.) illustration

How important do you regard each of the following questions to be when it comes to the question of whether the nurse should share his/her password to his/her co-workers. (Please mark only one ‘X’ for each line.) illustration

Select the four most important questions:
Most important _____
Next most important _____
Third in importance _____
Fourth in importance _____
Rights and permissions
About this article
Cite this article
Myyry, L., Siponen, M., Pahnila, S. et al. What levels of moral reasoning and values explain adherence to information security rules? An empirical study. Eur J Inf Syst 18, 126–139 (2009). https://doi.org/10.1057/ejis.2009.10
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1057/ejis.2009.10