Abstract
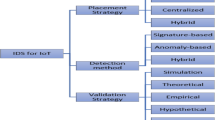
The application of the Internet of Things concept in domains such as industrial control, building automation, human health, and environmental monitoring, introduces new privacy and security challenges. Consequently, traditional implementation of monitoring and security mechanisms cannot always be presently feasible and adequate due to the number of IoT devices, their heterogeneity and the typical limitations of their technical specifications. In this paper, we propose an IP flow-based Intrusion Detection System (IDS) framework to monitor and protect IoT networks from external and internal threats in real-time. The proposed framework collects IP flows from an IoT network and analyses them in order to monitor and detect attacks, intrusions, and other types of anomalies at different IoT architecture layers based on some flow features instead of using packet headers fields and their payload. The proposed framework was designed to consider both the IoT network architecture and other IoT contextual characteristics such as scalability, heterogeneity, interoperability, and the minimization of the use of IoT networks resources. The proposed IDS framework is network-based and relies on a hybrid architecture, as it involves both centralized analysis and distributed data collection components. In terms of detection method, the framework uses a specification-based approach drawn on normal traffic specifications. The experimental results show that this framework can achieve ≈ 100% success and 0% of false positives in detection of intrusions and anomalies. In terms of performance and scalability in the operation of the IDS components, we study and compare it with three different conventional IDS (Snort, Suricata, and Zeek) and the results demonstrate that the proposed solution can consume fewer computational resources (CPU, RAM, and persistent memory) when compared to those conventional IDS.




















Similar content being viewed by others
References
Santos, L., Rabadão, C., Gonçalves, R.: Flow monitoring system for IoT networks. In: Rocha, Á., Adeli, H., Reis, L., Costanzo, S. (eds.) WorldCIST'19 - 7th World Conference on Information Systems and Technologies, Galicia, Spain 2019. Advances in intelligent systems and computing, New Knowledge in information systems and technologies, pp. 420–430. Springer, Cham (2019)
Bradley, J., Barbier, J., Handler, D.: Embracing the Internet of everything to capture your share of $14.4 trillion. White Paper, Cisco (2013)
Lee, I., Lee, K.: The Internet of things (IoT): applications, investments, and challenges for enterprises. Bus. Horiz. 58(4), 431–440 (2015)
Atzori, L., Iera, A., Morabito, G.: The internet of things: a survey. Comput. Netw. 54(15), 2787–2805 (2010)
Sha, K., Wei, W., Yang, T., Wang, Z., Shi, W.: On security challenges and open issues in Internet of things. Future Gener. Comput. Syst. 83, 326–337 (2018)
Kothmayr, T., Schmitt, C., Hu, W., Brünig, M., Carle, G.: DTLS based security and two-way authentication for the Internet of things. Ad Hoc Netw. 11(8), 2710–2723 (2013). https://doi.org/10.1016/j.adhoc.2013.05.003
Raza, S., Wallgren, L., Voigt, T.: SVELTE: real-time intrusion detection in the Internet of things. Ad Hoc Netw. 11(8), 2661–2674 (2013)
Raza, S., Duquennoy, S., Höglund, J., Roedig, U., Voigt, T.: Secure communication for the Internet of things—a comparison of link-layer security and IPsec for 6LoWPAN. Secur. Commun. Netw. 7(12), 2654–2668 (2014)
Granjal, J., Monteiro, E., Silva, J.: Security for the internet of things: a survey of existing protocols and open research issues. IEEE Commun. Surv. Tutor. 17(3), 1294–1312 (2015)
Khan, M., Salah, K.: IoT security: review, blockchain solutions, and open challenges. Future Gener. Comput. Syst. 82, 395–411 (2018)
AlRidhawi, I., Otoum, S., Aloqaily, M., Jararweh, Y., Baker, T.: Providing secure and reliable communication for next generation networks in smart cities. Sustain. Cities Soc. 56, 102080 (2020)
Otoum, S., Kantarci, B., Mouftah, H.: Empowering reinforcement learning on big sensed data for intrusion detection. In Icc 2019–2019 IEEE international conference on communications (ICC). IEEE, 2019
Zarpelao, B., Miani, R., Kawakani, C., de Alvarenga, S.: A survey of intrusion detection in Internet of things. J. Netw. Comput. Appl. 84, 25–37 (2017)
Santos, L., Rabadao, C., Gonçalves, R.: Intrusion detection systems in Internet of things: a literature review. In: 2018 13th Iberian Conference on Information Systems and Technologies (CISTI), Caceres, Spain, pp. 1–7. IEEE, 2018
Hajiheidari, S., Wakil, K., Badri, M., Navimipour, N.J.: Intrusion detection systems in the Internet of things: a comprehensive investigation. Comput. Netw. 160, 165–191 (2019)
Alaba, F., Othman, M., Hashem, I., Alotaibi, F.: Internet of things security: a survey. J. Netw. Comput. Appl. 88, 10–28 (2017)
Al-Fuqaha, A., Guizani, M., Mohammadi, M., Aledhari, M., Ayyash, M.: Internet of things: a survey on enabling technologies, protocols, and applications. IEEE Commun. Surv. Tutor. 17(4), 2347–2376 (2015)
Botta, A., De Donato, W., Persico, V., Pescapé, A.: Integration of cloud computing and internet of things: a survey. Future Gener. Comput. Syst. 56, 684–700 (2016)
Miorandi, D., Sicari, S., De Pellegrini, F., Chlamtac, I.: Internet of things: vision, applications and research challenges. Ad Hoc Netw. 10(7), 1497–1516 (2012)
Ziegler, S., Crettaz, C., Ladid, L., Krco, S., Pokric, B., Skarmeta, A., Jara, A., Kastner, W., Jung, M.: Iot6–moving to an ipv6-based future iot. In: Alex, G., Anastasius, G. (eds.) The future internet assembly, Dublin, Ireland 2013. Lecture notes in computer science, pp. 161–172. Springer, Berlin, Heidelberg (2013)
Khan, R., Khan, S., Zaheer, R., Khan, S.: Future internet: the internet of things architecture, possible applications and key challenges. In: 2012 10th international conference on frontiers of information technology, Islamabad, Pakistan, pp. 257–260. IEEE, 2012
Yang, Z., Yue, Y., Yang, Y., Peng, Y., Wang, X., Liu, W.: Study and application on the architecture and key technologies for IOT. In: 2011 International Conference on Multimedia Technology, Hangzhou, China, pp. 747–751. IEEE, 2011
Lin, J., Yu, W., Zhang, N., Yang, X., Zhang, H., Zhao, W.: A survey on internet of things: architecture, enabling technologies, security and privacy, and applications. IEEE Internet Things J. 4(5), 1125–1142 (2017)
Leo, M., Battisti, F., Carli, M., Neri, A.: A federated architecture approach for Internet of Things security. In: 2014 Euro Med Telco Conference (EMTC), pp. 1–5. IEEE, 2014
Zegzhda, D., Stepanova, T.: Achieving Internet of things security via providing topological sustainability. In: 2015 Science and Information Conference (SAI), pp. 269–276. IEEE, 2015
Meddeb, A.: Internet of things standards: who stands out from the crowd? IEEE Commun. Mag. 54(7), 40–47 (2016)
Gubbi, J., Buyya, R., Marusic, S., Palaniswami, M.: Internet of Things (IoT): a vision, architectural elements, and future directions. Future Gener. Comput. Syst. 29(7), 1645–1660 (2013)
Gluhak, A., Krco, S., Nati, M., Pfisterer, D., Mitton, N., Razafindralambo, T.: A survey on facilities for experimental internet of things research. IEEE Commun. Mag. 49(11), 58–67 (2011)
Sheng, Z., Yang, S., Yu, Y., Vasilakos, A., McCann, J., Leung, K.: A survey on the ietf protocol suite for the internet of things: standards, challenges, and opportunities. IEEE Wirel. Commun. 20(6), 91–98 (2013)
Stankovic, J.: Research directions for the internet of things. IEEE Internet Things J. 1(1), 3–9 (2014). https://doi.org/10.1109/JIOT.2014.2312291
Chen, S., Xu, H., Liu, D., Hu, B., Wang, H.: A vision of IoT: applications, challenges, and opportunities with china perspective. IEEE Internet Things J. 1(4), 349–359 (2014)
Lee, S., Levanti, K., Kim, H.: Network monitoring: present and future. Comput. Netw. 65, 84–98 (2014)
Velan, P.: Improving network flow definition: formalization and applicability. In: NOMS 2018–2018 IEEE/IFIP Network Operations and Management Symposium, Taipei, Taiwan, pp. 1–5. IEEE, 2018
Claise, B., Trammell, B., Aitken, P.: Specification of the IP flow information export (IPFIX) protocol for the exchange of flow information. In: RFC 7011 (INTERNET STANDARD), Internet Engineering Task Force. (2013)
Sperotto, A., Schaffrath, G., Sadre, R., Morariu, C., Pras, A., Stiller, B.: An overview of IP flow-based intrusion detection. IEEE Commun. Surv. Tutor. 12(3), 343–356 (2010)
Hofstede, R., Čeleda, P., Trammell, B., Drago, I., Sadre, R., Sperotto, A., Pras, A.: Flow monitoring explained: from packet capture to data analysis with netflow and ipfix. IEEE Commun. Surv. Tutor. 16(4), 2037–2064 (2014)
Zseby, T., Boschi, E., Brownlee, N., Claise, B.: IP flow information export (IPFIX) applicability. In, vol. RFC 5472. Internet Engineering Task Force (IETF), (2009)
Li, B., Springer, J., Bebis, G., Gunes, M.: A survey of network flow applications. J. Netw. Comput. Appl. 36(2), 567–581 (2013)
Halme, L., Bauer, R.: Aint misbehaving - A taxomony of anti-intrusion techniques. In: Wakid, S., Davis, J. (eds.) National information systems security 95, pp. 163–172. DIANE Publishing, Baltimore, EUA (1996)
AbuHmed, T., Mohaisen, A., Nyang, D.: A survey on deep packet inspection for intrusion detection systems. Magazine Korea Telecommun. Soc. 24(11), 25–36 (2008)
Husák, M., Velan, P., Vykopal, J.: Security monitoring of http traffic using extended flows. In: 2015 10th International Conference on Availability, Reliability and Security, Toulose, France, pp. 258–265. IEEE, 2015
Liao, H., Lin, C., Lin, Y., Tung, K.: Intrusion detection system: a comprehensive review. J. Netw. Comput. Appl. 36(1), 16–24 (2013)
Koch, R.: Towards next-generation intrusion detection. In: 2011 3rd International Conference on Cyber Conflict, Tallinn, Estonia, pp. 1–18. IEEE, 2011
Garcia-Teodoro, P., Diaz-Verdejo, J., Maciá-Fernández, G., Vázquez, E.: Anomaly-based network intrusion detection: techniques systems and challenges. Comput. Secur. 28, 18–28 (2009)
Umer, M., Sher, M., Bi, Y.: Flow-based intrusion detection: techniques and challenges. Comput. Secur. 70, 238–254 (2017)
Abuadlla, Y., Kvascev, G., Gajin, S., Jovanovic, Z.: Flow-based anomaly intrusion detection system using two neural network stages. Comput. Sci. Inf. Syst. 11(2), 601–622 (2014)
Costa, K., Pereira, L., Nakamura, R., Pereira, C., Papa, J., Falcão, A.: A nature-inspired approach to speed up optimum-path forest clustering and its application to intrusion detection in computer networks. Inf. Sci. 294, 95–108 (2015)
Satoh, A., Nakamura, Y., Ikenaga, T.: A flow-based detection method for stealthy dictionary attacks against secure shell. J. Inf. Secur. Appl. 21, 31–41 (2015)
Liu, C., Yang, J., Chen, R., Zhang, Y., Zeng, J.: Research on immunity-based intrusion detection technology for the internet of things. In: 2011 Seventh International Conference on Natural Computation, Shanghai, China, pp. 212–216. IEEE, 2011
Kasinathan, P., Costamagna, G., Khaleel, H., Pastrone, C., Spirito, M.: An IDS framework for internet of things empowered by 6LoWPAN. In: Proceedings of the 2013 ACM SIGSAC conference on Computer and communications security, Berlin, Germany, pp. 1337–1340. ACM, 2013
Kasinathan, P., Pastrone, C., Spirito, M., Vinkovits, M.: Denial-of-service detection in 6LoWPAN based Internet of things. In: 2013 IEEE 9th international conference on wireless and mobile computing, networking and communications (WiMob), Lyon, France, pp. 600–607. IEEE, 2013
Shreenivas, D., Raza, S., Voigt, T.: Intrusion detection in the RPL-connected 6LoWPAN networks. In: Proceedings of the 3rd ACM International Workshop on IoT Privacy, Trust, and Security, Abu Dhabi, United Arab Emirates, pp. 31–38. ACM, 2017
Jun, C., Chi, C.: Design of complex event-processing IDS in internet of things. In: 2014 Sixth International Conference on Measuring Technology and Mechatronics Automation, Zhangjiajie, China, pp. 226–229. IEEE, 2014
Pongle, P., Chavan, G.: Real time intrusion and wormhole attack detection in internet of things. Int. J. Comput. Appl. 121(9), 1–9 (2015)
Midi, D., Rullo, A., Mudgerikar, A., Bertino, E.: Kalis—A system for knowledge-driven adaptable intrusion detection for the Internet of things. In: 2017 IEEE 37th International Conference on Distributed Computing Systems (ICDCS), pp. 656–666. IEEE, 2017
Aloqaily, M., Otoum, S., Al Ridhawi, I., Jararweh, Y.: An intrusion detection system for connected vehicles in smart cities. Ad Hoc Netw. 90, 101842 (2019)
Diro, A.A., Chilamkurti, N.: Distributed attack detection scheme using deep learning approach for Internet of things. Future Gener. Comput. Syst. 82, 761–768 (2018)
Li, J., Zhao, Z., Li, R., Zhang, H.: Ai-based two-stage intrusion detection for software defined IoT networks. IEEE Internet Things J. 6(2), 2093–2102 (2018)
Deng, L., Li, D., Yao, X., Cox, D., Wang, H.: Mobile network intrusion detection for IoT system based on transfer learning algorithm. Clust. Comput. 22(4), 9889–9904 (2019)
Gajewski, M., Batalla, J.M., Mastorakis, G., Mavromoustakis, C.X.: A distributed IDS architecture model for smart home systems. Clust. Comput. 22, 1–11 (2019)
Pajouh, H.H., Javidan, R., Khayami, R., Dehghantanha, A., Choo, K.R.: A two-layer dimension reduction and two-tier classification model for anomaly-based intrusion detection in IoT backbone networks. IEEE Ann. Hist. Comput. 02, 314–323 (2019)
Siddiqui, A.J., Boukerche, A.: TempoCode-IoT: temporal codebook-based encoding of flow features for intrusion detection in Internet of things. Clust. Comput. 1, 1–19 (2020)
Eskandari, M., Janjua, Z.H., Vecchio, M., Antonelli, F.: Passban IDS: an intelligent anomaly based intrusion detection system for IoT edge devices. IEEE Internet Things J. 7(8), 6882–6897 (2020)
Santos, L., Gonçalves, R., Rabadão, C.: A novel intrusion detection system architecture for internet of things networks. In: ECCWS 2019 18th European Conference on Cyber Warfare and Security, Coimbra, Portugal, p. 428. Academic Conferences and publishing limited, 2019
Canuto, L., Santos, L., Vieira, L., Gonçalves, R., Rabadão, C.: CoAP flow signatures for the internet of things. In 2019 14th Iberian Conference on Information Systems and Technologies (CISTI). IEEE, 2019
Leal, R., Santos, L., Vieira, L., Gonçalves, R., Rabadão, C.: MQTT flow signatures for the Internet of things. In 2019 14th Iberian Conference on Information Systems and Technologies (CISTI). IEEE, 2019
Vieira, L., Santos, L., Gonçalves, R., Rabadão, C.: Identifying attack signatures for the internet of things: an IP flow based approach. In 2019 14th Iberian Conference on Information Systems and Technologies (CISTI). IEEE, 2019.
Acknowledgements
This work was supported by Portuguese national funds through the FCT—Foundation for Science and Technology, I.P., under the project UID/CEC/04524/2019.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Santos, L., Gonçalves, R., Rabadão, C. et al. A flow-based intrusion detection framework for internet of things networks. Cluster Comput 26, 37–57 (2023). https://doi.org/10.1007/s10586-021-03238-y
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10586-021-03238-y