Abstract
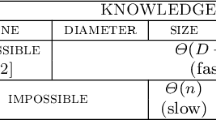
We study the minimum memory size with which nodes of a network have to be equipped, in order to solve deterministically the leader election problem. Nodes are unlabeled, but ports at each node have arbitrary fixed labelings which, together with the topology of the network, can create asymmetries to be exploited in leader election. We consider two versions of the leader election problem: strong LE in which exactly one leader has to be elected, if this is possible, while all nodes must terminate in a state “infeasible” when the election of a unique leader fails, and weak LE, which differs from strong LE in that no requirement on the behavior of nodes is imposed, if leader election is impossible. Nodes are modeled as identical automata and we ask what is the minimum amount of memory of such an automaton to enable leader election. We show that logarithmic memory is optimal for both strong and weak leader election in the class of arbitrary connected graphs. By contrast we show that strong LE can be accomplished in the class of trees of maximum degree Δ using only O(log log Δ) bits of memory, thus proving an exponential gap in memory requirements for leader election between the class of trees and the class of arbitrary graphs.
Similar content being viewed by others
References
Attiya H., Snir M., Warmuth M.: Computing on an anonymous ring. J. ACM 35, 845–875 (1988)
Attiya H., Snir M.: Better computing on the anonymous ring. J. Algorithms 12, 204–238 (1991)
Boldi, P., Shammah, S., Vigna, S., Codenotti, B., Gemmell, P., Simon, J.: Symmetry breaking in anonymous networks: characterizations. In: Proceedings of the 4th Israel Symposium on Theory of Computing and Systems (ISTCS), pp. 16–26 (1996)
Boldi, P., Vigna, S.: Computing anonymously with arbitrary knowledge. In: Proceedings of the 18th ACM Symposium on Principles of Distributed Computing, pp. 181–188 (1999)
Burns, J.E.: A Formal Model for Message Passing Systems, Technical Report TR-91. Computer Science Department, Indiana University, Bloomington, September 1980
Chalopin, J.: Local Computations on Closed Unlabelled Edges: The Election Problem and the Naming Problem SOFSEM: Theory and Practice of Computer Science 82–91 (2005)
Chalopin, J., Mazurkiewicz, A.W., Métivier, Y.: Labelled (Hyper)graphs, negotiations and the naming problem. In: Proceedings of the 4th International Conference on Graph Transformations (ICGT), pp. 54–68 (2008)
Chalopin, J., Métivier, Y.: Election and local computations on edges. In: Proceedings of the Foundations of Software Science and Computation Structures (FoSSaCS), pp. 90–104 (2004)
Cook S.A., Rackoff C.: Space lower bounds for maze threadability on restricted machines. SIAM J. Comput. 9, 636–652 (1980)
Czyzowicz, J., Kosowski, A., Pelc, A.: How to meet when you forget: log-space rendezvous in arbitrary graphs. In: Proceedings of the 29th ACM Symposium on Principles of Distributed Computing (PODC), pp. 450–459 (2010)
Diks K., Kranakis E., Malinowski A., Pelc A.: Anonymous wireless rings. Theor. Comput. Sci. 145, 95–109 (1995)
Dobrev S., Pelc A.: Leader election in rings with nonunique labels. Fundam. Inf. 59, 333–347 (2004)
Flocchini P., Kranakis E., Krizanc D., Luccio F.L., Santoro N.: Sorting and election in anonymous asynchronous rings. J. Parallel Distrib. Comput. 64(2), 254–265 (2004)
Fraigniaud, P., Gavoille, C.: Routing in trees. In: Proceedings of the 28th International Colloquium on Automata, Languages and Programming (ICALP), pp. 757–772 (2001)
Fraigniaud, P., Gavoille, C.: A space lower bound for routing in trees. In: Proceedings of the 19th Annual Symposium on Theoretical Aspects of Computer Science (STACS), pp. 65–75 (2002)
Fraigniaud, P., Ilcinkas, D.: Digraphs exploration with little memory. In: Proceedings of the 21st Symposium on Theoretical Aspects of Computer Science (STACS), pp. 246–257 (2004)
Fraigniaud, P., Pelc, A.: Deterministic rendezvous in trees with little memory. In: Proceedings of the 22nd International Symposium on Distributed Computing (DISC), pp. 242–256 (2008)
Fraigniaud, P., Pelc, A.: Delays induce an exponential memory gap for rendezvous in trees. In: Proceedings of the 22nd Annual ACM Symposium on Parallel Algorithms and Architectures (SPAA), pp. 224–232 (2010)
Fredrickson G.N., Lynch N.A.: Electing a leader in a synchronous ring. J. ACM 34, 98–115 (1987)
Haddar, M.A., Kacem, A.H., Métivier, Y., Mosbah, M., Jmaiel, M.: Electing a leader in the local computation model using mobile agents. In: Proceedings of the 6th ACS/IEEE International Conference on Computer Systems and Applications (AICCSA), pp. 473–480 (2008)
Hirschberg D.S., Sinclair J.B.: Decentralized extrema-finding in circular configurations of processes. Commun. ACM 23, 627–628 (1980)
Jurdzinski, T., Kutylowski, M., Zatopianski, J.: Efficient algorithms for leader election in radio networks. In: Proceedings of the 21st ACM Symposium on Principles of Distributed Computing (PODC), pp. 51–57 (2002)
Kouckỳ M.: Universal traversal sequences with backtracking. J. Comput. Syst. Sci. 65, 717–726 (2002)
Kowalski, D., Pelc, A.: Leader election in ad hoc radio networks: a keen ear helps. In: Proceedings of the 36th International Colloquium on Automata, Languages and Programming (ICALP), LNCS 5556, pp. 521–533 (2009)
Kranakis, E.: Symmetry and computability in anonymous networks: a brief survey. In: Proceedings of the 3rd International Conference on Structural Information and Communication Complexity, pp. 1–16 (1997)
Kranakis E., Krizanc D., van der Berg J.: Computing Boolean functions on anonymous networks. Inf. Comput. 114, 214–236 (1994)
Kranakis, E., Krizanc, D., Morin, P.: Randomized Rendez-Vous with Limited Memory. In: Proceedings of the 8th Latin American Theoretical Informatics (LATIN), pp. 605–616 (2008)
Le Lann, G.: Distributed systems—towards a formal approach. In: Proceedings of the IFIP Congress. North Holland, pp. 155–160 (1977)
Lindell, S.: A logspace algorithm for tree canonization. In: Proceedings of the 24th ACM Symposium on Theory of Computing (STOC), pp. 400–404 (1992)
Nakano K., Olariu S.: Uniform leader election protocols for radio networks. IEEE Trans. Parallel Distrib. Syst. 13, 516–526 (2002)
Norris N.: Universal covers of graphs: isomorphism to depth N−1 implies isomorphism to all depths. Discrete Appl. Math. 56(1), 61–74 (1995)
Peterson G.L.: An O(n log n) unidirectional distributed algorithm for the circular extrema problem. ACM Trans. Program. Lang. Syst. 4, 758–762 (1982)
Reingold O.: Undirected connectivity in log-space. J. ACM 55, 1–24 (2008)
Sakamoto, N.: Comparison of initial conditions for distributed algorithms on anonymous networks. In: Proceedings of the 18th ACM Symposium on Principles of Distributed Computing (PODC), pp. 173–179 (1999)
Willard D.E.: Log-logarithmic selection resolution protocols in a multiple access channel. SIAM J. Comput. 15, 468–477 (1986)
Yamashita, M., Kameda, T.: Computing on anonymous networks. In: Proceedings of the 7th ACM Symposium on Principles of Distributed Computing (PODC), pp. 117–130 (1988)
Yamashita, M., Kameda, T.: Electing a leader when procesor identity numbers are not distinct. In: Proceedings of the 3rd Workshop on Distributed Algorithms, LNCS vol. 392, Springer-Verlag (WDAG), pp. 303–314 (1989)
Yamashita M., Kameda T.: Computing on anonymous networks: Part I—characterizing the solvable cases. IEEE Trans. Parallel Distrib. Syst. 7, 69–89 (1996)
Author information
Authors and Affiliations
Corresponding author
Additional information
A preliminary version of this paper appeared in the Proceedings of the 24th International Symposium on Distributed Computing (DISC 2010), LNCS 6343.
This work was done during the visit of Emanuele G. Fusco at the Research Chair in Distributed Computing of the Université du Québec en Outaouais.
Andrzej Pelc was partially supported by NSERC discovery grant and by the Research Chair in Distributed Computing at the Université du Québec en Outaouais.
Rights and permissions
About this article
Cite this article
Fusco, E.G., Pelc, A. How much memory is needed for leader election. Distrib. Comput. 24, 65–78 (2011). https://doi.org/10.1007/s00446-011-0131-y
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s00446-011-0131-y