Abstract
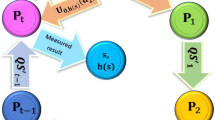
To detect frauds from some internal participants or external attackers, some verifiable threshold quantum secret sharing schemes have been proposed. In this paper, we present a new verifiable threshold structure based on a single qudit using bivariate polynomial. First, Alice chooses an asymmetric bivariate polynomial and sends a pair of values from this polynomial to each participant. Then Alice and participants implement in sequence unitary transformation on the d-dimensional quantum state based on unbiased bases, where those unitary transformations are contacted by this polynomial. Finally, security analysis shows that the proposed scheme can detect the fraud from external and internal attacks compared with the exiting schemes and is comparable to the recent schemes.
Similar content being viewed by others
References
Hillery, M., BuÚCzek, V., Berthiaume, A.: Quantum secret sharing. J. Physical Review A 59(3), 1829 (1999)
Cleve, R., Gottesman, D., Lo, H.K.: How to share a quantum secret. J. Physical Review Letters 83(3), 648 (1999)
Karlsson, A., Koashi, M., Imoto, N.: Quantum entanglement for secret sharing and secret splitting. J. Physical Review A 59(1), 162 (1999)
Guo, G.P., Guo, G.C.: Quantum secret sharing without entanglement. J. Physics Letters A 310(4), 247–251 (2003)
Xiao, L., Long, G.L., Deng, F.G., et al.: Efficient multiparty quantum-secret-sharing schemes. J. Physical Review A 69(5), 052–307 (2004)
Zhang, Z., Li, Y., Man, Z.: Multiparty quantum secret sharing. J. Physical Review A 71(4), 044–301 (2005)
Yang, Y.G., Jia, X., Wang, H.Y., et al.: Verifiable quantum (k, n)-threshold secret sharing. J. Quantum Information Processing 11(6), 1619–1625 (2012)
Song, X., Liu, Y.: Cryptanalysis and improvement of verifiable quantum (k, n) secret sharing. J. Quantum Information Processing 15(2), 851–868 (2016)
Lu, C., Miao, F., Hou, J., et al.: Verifiable threshold quantum secret sharing with sequential communication. J. Quantum Information Processing 17 (11), 310 (2018)
Chor, B., Goldwasser, S., Micali, S., et al.: Verifiable secret sharing and achieving simultaneity in the presence of faults. In: 26th Annual Symposium on Foundations of Computer Science (sfcs 1985). IEEE, pp 383–395 (1985)
Shor, P.W.: Algorithms for quantum computation: Discrete logarithms and factoring. In: Proceedings 35th annual symposium on foundations of computer science. Ieee, pp 124–134 (1994)
Grover, L.K.: A fast quantum mechanical algorithm for database search, quant-ph/9605043 (1996)
Tavakoli, A., Herbauts, I., Żukowski, M., et al.: Secret sharing with a single d-level quantum system. J. Physical Review A 92(3), 030–302 (2015)
Gennaro, R., Ishai, Y., Kushilevitz, E., et al.: The round complexity of verifiable secret sharing and secure multicast. In: Proceedings of the thirty-third annual ACM symposium on Theory of computing. ACM, pp. 580–589 (2001)
Katz, J., Koo, C.Y., Kumaresan, R.: Improving the round complexity of VSS in point-to-point networks. In: International Colloquium on Automata, Languages, and Programming. Springer, Berlin, Heidelberg, pp 499–510 (2008)
Kumaresan, R., Patra, A., Rangan, C.P.: The round complexity of verifiable secret sharing: The statistical case. In: International Conference on the Theory and Application of Cryptology and Information Security. Springer, Berlin, Heidelberg, pp 431–447 (2010)
Nikov, V., Nikova, S.: On proactive secret sharing schemes. In: International Workshop on Selected Areas in Cryptography. Springer, Berlin, Heidelberg, pp 308–325 (2004)
Ivonovic, I.D.: Geometrical description of quantal state determination. Journal of Physics A: Mathematical and General 14(12), 3241 (1981)
Wootters, W.K., Fields, B.D.: Optimal state-determination by mutually unbiased measurements. Annals of Physics 191(2), 363–381 (1989)
Qin, H., Dai, Y.: Verifiable (t, n) threshold quantum secret sharing using d-dimensional Bell state. Information Processing Letters 116(5), 351–355 (2016)
Acknowledgements
We would like to thank anonymous reviewer for valuable comments. This work is supported by the National Natural Science Foundation of China under Grant No.11671244.
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher’s Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Zhi, DL., Li, ZH., Han, ZW. et al. Verifiable Quantum Secret Sharing Based on a Single Qudit. Int J Theor Phys 59, 3672–3684 (2020). https://doi.org/10.1007/s10773-020-04599-7
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s10773-020-04599-7