Abstract
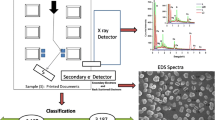
When trying to identify a printed forged document, examining digital evidence can prove to be a challenge. In this study, microscopic images are used for printed source identification due to their high magnification properties resulting in detailed texture and structure information. Prior research implemented a scanner as a digitizing technique to resolve very fine printed identification, but this technique provided limited information on the resolution and magnification of the sample. In contrast, the performance of microscopy techniques can retrieve the shape and surface texture of a printed document with differing micro structures among printer sources. To explore the relationship between source printers and images obtained by the microscope, the proposed approach utilizes image processing techniques and data exploration methods to calculate many important statistical features, including: Local Binary Pattern (LBP), Gray Level Co-occurrence Matrix (GLCM), Discrete Wavelet Transform (DWT), Spatial filters, the Wiener filter, the Gabor filter, Haralick, and SFTA features. Among the different set of features, the LBP approach achieves the highest identification rate and is significantly superior to other methods. As a result, the proposed technique using microscopic images achieves a high classification accuracy rate, which shows promising applications for real world digital forensics research.
















Similar content being viewed by others
References
Ali GN, Chiang PJ, Mikkilineni AK, Chiu GT, Delp EJ, Allebach JP (2004) Application of principal components analysis and Gaussian mixture models to printer identification. In: Intl. Conference on digital printing technologies. Salt Lake City, pp. 301–305
Bekhti MA, Kobayashi Y (2016) Prediction of vibrations as a measure of terrain traversability in outdoor structured and natural environments, in: image and video technology, Vol. 9431 of the series lecture notes in computer Science. Springer International Publishing, Auckland, pp 282–294. doi:10.1007/978-3-319-29451-3_23
Buchanan JDR et al (2005) Fingerprinting’ documents and packaging. Nature 436:475. doi:10.1038/436475a
Bulan O, Mao J, Sharma G (2009) Geometric distortion signatures for printer identification International conference on acoustics, speech and signal processing (ICASSP). Taipei pp 1401-1404. doi: 10.1109/ICASSP.2009.4959855
Chiang PJ, Khanna N, Mikkilineni AK, Segovia MVO, Suh S, Allebach JP, Chiu GTC, Delp EJ (2009) Printer and scanner forensics: examining the security mechanisms for a unique interface. IEEE signal processing magazine. March, pp.72-83. doi: 10.1109/MSP.2008.931082
Choi JH, Lee HY, Lee HK (2013) Color laser printer forensic based on noisy feature and support vector machine classifier. Multimedia Tools Applications 67:363–382. doi:10.1007/s11042-011-0835-9
Chu PC, Cai BY, Tsoi YK, Yuen R, Leung KSY, Cheung NH (2013) Forensic analysis of laser printed ink by X-ray fluorescence and laser-excited plume fluorescence. Anal Chem 85(9):4311–4315. doi:10.1021/ac400378q
Chun-Lin L, (2010) A tutorial of the wavelet transforms. National Taiwan University http://disp.ee.ntu.edu.tw/tutorial/WaveletTutorial.pdf. Accessed 13 July 2016
Costa AF, Humpire-Mamani G, Traina AJM (2012) An efficient algorithm for fractal analysis of textures. SIBGRAPI Conference on Graphics, Patterns and Images, August, Ouro Preto. pp. 39–46. doi:10.1109/SIBGRAPI.2012.15
Cox IJ, Miller ML, Bloom JA, Fridrich J, Kalker T (2008) Digital watermarking and steganography, 2nd edn. Morgan Kaufmann Publishers, Amsterdam
Abramowitz M, Davidson MW, The concept of magnification. Olympus America, Inc. https://micro.magnet.fsu.edu/primer/anatomy/magnification.html. Accessed 2 Feb 2017
Ferreira A, Navarro LC, Pinheiro G, Santos JAD, Rocha A (2015) Laser printer attribution: exploring new features and beyond. Forensic Sci Int 247:105–125. doi:10.1016/j.forsciint.2014.11.030
Gonzales RC, Woods RE (2008) Digital Image Processing, 3rd edn. Prentice Hall, New Jersey
Haghighat M, Zonous S, Abdel-Mottaleb M (2015) CloudID: trustworthy cloud-based and cross-enterprise biometric identification. Expert Syst Appl 42(21):7905–7916. doi:10.1016/j.eswa.2015.06.025
Haralick RM, Shanmugam K, Dinstein I (1973) Textural features for image classification. IEEE Trans Syst, Man Cybern SMC-3(6):610–621
Herman B, Lemasters JJ (1993) Optical microscopy: emerging methods and applications. Academic Press, San Diego
Hewlett-Packard Company (2002) HP LaserJet 4200 and 4300 series printers http://www.nuigalway.ie/psy/sub/manuals/hp_lj4200.pdf. Accessed 21 June 2016
Hsu CW, Chang CC, Lin CJ (2003) A practical guide to support vector classification, Taipei: National Taiwan University. http://www.csie.ntu.edu.tw/~cjlin/papers/guide/guide.pdf. Accessed 18 July 2016
https://en.wikipedia.org/wiki/Digitizing. Accessed 2 Aug 2016
Jurič I, Ranđelović D, Karlović I, Tomić I (2014) Influence of the surface roughness of coated and uncoated papers on the digital print mottle. Journal of Graphic Engineering and Design 5(1):17–23
Juuti M, Prykäri T, Alarousu E, Koivula H, Myllys M, Lähteelä A, Toivakka M, Timonen J, Myllylä R, Peiponen KE (2007) Detection of local specular gloss and surface roughness from black prints, in: colloids and surfaces a: physicochemical and engineering aspects. Elsevier 299(1-3):101–108. doi:10.1016/j.colsurfa.2006.11.039
Kawasaki M, Ishisaki M ( 2009) Investigation into the cause of print mottle in halftone dots of coated paper: effect of optical dot gain non-uniformity, vol.63. No.11, pp.1362–1373. http://www.tappi.org/content/06IPGA/5-4%20Kawasaki%20M%20Ishisaki.pdf. Accessed 27 June 2016
Kim DG, Lee HK (2014) Color laser printer identification using photographed halftone images, Proc. of EUSIPCO. September, IEEE, Lisbon, pp. 795–799
Kim KI, Jung K, Park SH, Kim HJ (2002) Support vector machines for texture classification. IEEE Trans Pattern Anal Mach Intell 24(11):1542–1550. doi:10.1109/TPAMI.2002.1046177
Kundur D, Lin CY, Macq B, H. Yu (2004) Scanning the issue: special issue on enabling security technologies for digital rights management, in Proceedings of the IEEE, pp. 879–882
Li Q, Zhang Z, Lu W, Yang J, Ma Y, Yao W (2016) From pixels to patches: a cloud classification method based on a bag of micro-structures. Atmospheric Measurement Techniques 9:753–764
Mäenpää T, Pietikäinen M (2004) Texture analysis with local binary patterns. In: Chen CH, Wang PSP (eds) Handbook of Pattern Recognition & Computer Vision, 3rd edn. World Scientific, Singapore, pp 115–118
Marcella AJ Jr, Guillossou F (2012) Cyber forensics: from data to digital evidence. John Willy & Sons, New Jersey
Mihlbachler MC, Beatty BL, Caldera-Siu A, Chan D (2012) Error rates in dental microwear analysis using light microscopy. Palaeontol Electron 15(12A):22
Mikkilineni AK, Chiang PJ, Ali GN, Chiu GTC, Allebach JP, Delp EJ (2005) Printer identification based on graylevel co-occurrence features for security and forensic applications. In Proceedings of the SPIE International Conference on Security, vol. 5681, pp. 430–440
Mikkilineni AK, Arslan O, Chiang PJ, Kumontoy RM, Allebach JP, Chiu GTC, Delp EJ (2005) Printer forensics using svm techniques in Proceedings of the IS&T’s NIP21: International conference on digital printing technologies, vol. 21, Baltimore, October, pp. 223–226
Ojala T, Pietikäinen M, Mäenpää T (2002) Multiresolution gray-scale and rotation invariant texture classification with LBP, IEEE Trans. Pattern Analysis & Machine Intelligence 24(7):971–987. doi:10.1109/TPAMI.2002.1017623
Oravec M, Gál L, Čeppan M (2015) Pre-processing of inkjet prints NIR spectral data for principal component analysis. Acta Chim Slov 8(2):191–196. doi:10.1515/acs-2015-0031
Osadchy M, Jacobs DW, Lindenbaum M (2007) Surface dependent representations for illumination insensitive image comparison. IEEE Trans Pattern Anal Mach Intell 29(1):98–111. doi:10.1109/TPAMI.2007.19
Pollard SB, Simske SJ, Adams GB (2010) Model based print signature profile extraction for forensic analysis of individual text glyphs. IEEE workshop on information forensics and security - WIFS'10, Seattle, December 12-15. http://www.hpl.hp.com/techreports/2010/HPL-2010-173.html. Accessed 6 Aug 2016
Pollard S, Simske S, Adams G (2013) Print Biometrics: Recovering forensic signatures from halftone images, Hewlett-Packard Development Company http://www.hpl.hp.com/techreports/2013/HPL-2013-1.pdf. Accessed 30 Jul 2016
Ryu SJ, Lee HY, Im DH, Choi JH, Lee HK (2010) Electrophotographic printer identification by halftone texture analysis. In: IEEE Intl. Conference on acoustics speech and signal processing (ICASSP). pp. 1846–1849. doi:10.1109/ICASSP.2010.5495377
Say OT, Sauli Z, Retnasamy V (2013) High density printing paper quality investigation, IEEE Regional Symposium on Micro and Nano electronics (RSM). Langkawi, pp. 273-277. doi:10.1109/RSM.2013.6706528
Schalkoff RJ (1989) Digital image processing and computer vision. John Wiley & Sons, Australia
Sharma G (2016) Image-based data interfaces revisited: barcodes and watermarks for the mobile and digital worlds. 8th International conference on communication systems and networks (COMSNETS). 5-10 January, 6 p. doi:10.1109/COMSNETS.2016.7440021
Sharma A, Subramanin L, Brewer E (2011) PaperSpeckle: microscopic fingerprinting of paper. Proceedings of the 18th ACM conference on Computer and communications security, Chicago, Illinois, USA — October 17–21, pp. 99–110 doi: 10.1145/2046707.2046721
Simske SJ, Adams G (2010) High-resolution glyph-inspection based security system, IEEE International Conference on Acoustics, Speech, and Signal Processing, 14–19 March, pp. 1794–1797. doi: 10.1109/ICASSP.2010.5495416
Su R, Pekarovicova A, Fleming PD, Bliznyuk V (2005) Physical Properties of LWC Papers and Gravure Ink Mileage https://www.researchgate.net/publication/251423637_Physical_Properties_of_LWC_Papers_and_Gravure_Ink_Mileage. Accessed 23 June 2016
Szynkowska MI, Czerski K, Paryjczak T, Parczewski A (2010) Ablative analysis of black and colored toners using LA-ICP-TOF-MS for the forensic discrimination of photocopy and printer toners. Survey and Interface Analysis 42:429–437. doi:10.1002/sia.3194
Tsai MJ, Liu J (2013) Digital forensics for printed source identification. In IEEE International Symposium on Circuits and Systems (ISCAS). May, pp. 2347–2350. doi: 10.1109/ISCAS.2013.6572349
Tsai MJ, Yin JS, Yuadi I, Liu J (2014) Digital forensics of printed source identification for Chinese characters. Multimedia Tools and Applications 73:2129–2155. doi:10.1007/s11042-013-1642-2
Tsai MJ, Hsu CL, Yin JS, Yuadi I (2015) Japanese character based printed source identification, IEEE International Symposium on Circuits and Systems (ISCAS). May, Lisbon. pp. 2800-2803. doi: 10.1109/ISCAS.2015.7169268
Vega LR, Rey H (2013) A rapid introduction to adaptive filtering. Springer-Verlag, Berlin Heidelberg
Voloshynovskiy S, Holotyak T, Bas P (2016) Physical object authentication: detection-theoretic comparison of natural and artificial randomness. IEEE International conference on acoustics, speech and signal processing, 20-25 March, pp. 2029-2033. doi: 10.1109/ICASSP.2016.7472033
Zhu B, Wu J, Kankanhalli MS (2003) Print signatures for document authentication. Proceedings of the 10th ACM conference on Computer and communications security. Washington D.C., USA October 27–30, 2003, pp. 145–154. doi: 10.1145/948109.948131
Acknowledgments
This work was partially supported by the National Science Council in Taiwan, Republic of China, under NSC104-2410-H-009-020-MY2.
Author information
Authors and Affiliations
Corresponding author
Appendix: Formula of feature extraction
Appendix: Formula of feature extraction
Rights and permissions
About this article
Cite this article
Tsai, MJ., Yuadi, I. Digital forensics of microscopic images for printed source identification. Multimed Tools Appl 77, 8729–8758 (2018). https://doi.org/10.1007/s11042-017-4771-1
Received:
Revised:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11042-017-4771-1