Abstract
We study a model of terrorism and counterterrorism with three geographic target locations, in which the last location is chosen by the terrorists and is unknown to the defender. We find the choice of location and defender’s allocation of defensive resources to depend on whether the first two locations are attacked simultaneously or sequentially. In the sequential-move game, the final attack is closer to the low-valued target than it is in the simultaneous-move game. In addition, the defender chooses to defend only the location that is attacked first in the sequential game. Results from the model also can shed light on less provocative criminal events such as bank robberies and drug dealings.
Similar content being viewed by others
Notes
Comparatively, there are 4,935 attacks targeted a single geographic location, 3,002 attacks targeted two locations, 467 attacks targeted four locations, 228 attacks targeted five locations, and 553 attacks targeted six or more locations (authors’ calculation).
Game-theoretic models have provided important insights into the analyses of terrorism and counterterrorism. Notable examples include Sandler et al. (1983) and Bueno de Mesquita (2005a, b, c) on various interactions between government and terrorists, Cadigan and Schmitt (2010) on entry deterrence and terrorism, Bandyopadhyay and Sandler (2011) on the interplay between preemptive and defensive measures, Bandyopadhyay et al. (2011, 2014) on the relationship between foreign aid, terrorism, and counterterrorism, and Das and Chowdhury (2014) on deterrence and preemption. For recent surveys, see Sandler and Arce (2003), Sandler and Siqueira (2009), Sandler (2014, 2015), and Schneider et al. (2015).
Even though Bier et al. (2007) present a general model that can deal with more than two potential targets, the main derivation of their results is done in a two-target setting.
Alternatively, one may think of this scenario in the context of two local terrorist groups competing to show their loyalty to the leader by providing “additional” soldiers.
As outlined in Sect. 2.2, the current model assumes that the defender “chooses” the values of \(w_i\). As a result, whether defense may cause a reversal of valuations of the two locations can not be analyzed in the current framework.
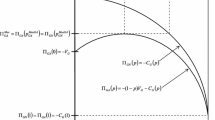
The sufficient and necessary condition for \({\bar{d}}_1={\tilde{d}}_1\) is
$$\begin{aligned} {\left\{ \begin{array}{ll}w_1=2w_1-w_2;\\ w_1^2+w_2^2=4w_1^2-3w_1w_2+w_2^2;\end{array}\right. } \end{aligned}$$which hold true if \(w_1=w_2\).
It is straightforward to verify that
$$\begin{aligned} \frac{\partial ^2{\mathscr {L}}}{\partial w_i^2}=\frac{w_j(w_i+w_j)}{w_i^2(w_i+w_j)^2}>0; \end{aligned}$$and hence the second order condition of a minimization problem is satisfied.
In the movie, Texas Ranger Marcus Hamilton, played by Oscar-winning actor Jeff Bridges, needs to determine which branch of a bank will be attacked next by the Howard brothers. The Howard brothers had previously robbed three other branches of the same bank.
References
Bandyopadhyay, S., & Sandler, T. (2011). The interplay between preemptive and defensive counterterrorism measures: A two-stage game. Economica, 78, 546–564.
Bandyopadhyay, S., Sandler, T., & Younas, J. (2011). Foreign aid as counterterrorism policy. Oxford Economic Papers, 63, 423–447.
Bandyopadhyay, S., Sandler, T., & Younas, J. (2014). Foreign direct investment, aid, and terrorism. Oxford Economic Papers, 66, 25–50.
Bier, V., Oliveros, S., & Samuelson, L. (2007). Choosing what to protect: Strategic defensive allocation against an unknown attacker. Journal of Public Economic Theory, 9, 563–587.
Blomberg, B., Gaibulloev, K., & Sandler, T. (2011). Terrorist group survival: Ideology, tactics, and base of eperations. Public Choice, 149, 441–463.
Buchanan, J. M. (1983). Rent seeking, noncompensated transfers, and laws of succession. Journal of Law and Economics, 26, 71–85.
Bueno de Mesquita, E. (2005a). Conciliation, counterterrorism, and patterns of terrorist violence. International Organization, 59, 145–176.
Bueno de Mesquita, E. (2005b). The quality of terror. American Journal of Political Science, 49, 515–530.
Bueno de Mesquita, E. (2005c). The terrorist endgame: A model with moral hazard and learning. Journal of Conflict Resolution, 49, 237–258.
Cadigan, J., & Schmitt, P. M. (2010). Strategic entry deterrence and terrorism: Theory and experimental evidence. Public Choice, 143, 3–22.
Chang, Y. M., & Luo, Z. (2015). Endogenous division rules as a family constitution: Strategic altruistic transfers and sibling competition. Journal of Population Economics, 28, 173–194.
Chang, Y. M., & Weisman, D. L. (2005). Sibling rivalry and strategic parental transfers. Southern Economic Journal, 71, 821–836.
Das, S. P., & Chowdhury, P. R. (2014). Deterrence, preemption, and panic: A common-enemy problem o terrorism. Economic Inquiry, 52, 219–238.
Eaton, C. (2004). The elementary economics of social dilemmas. Canadian Journal of Economics, 37(4), 805–829.
Farrow, S. (2007). The economics of homeland security expenditures: Foundational expected cost-effectiveness approaches. Contemporary Economic Policy, 25(1), 14–26.
Gal-Or, E. (1985). First mover and second mover advantages. International Economic Review, 26(3), 649–653.
Hausken, K. (2012). The economics of terrorism against two targets. Applied Economics Letters, 19, 1135–1138.
Kovenock D, Roberson B (2017) The optimal defense of networks of targets. http://digitalcommons.chapman.edu/esi_working_papers/230
National Consortium for the Study of Terrorism and Responses to Terrorism (START) (2016) Global terrorism database [data file]. Retrieved from https://www.start.umd.edu/gtd
Powell, R. (2007). Defending against terrorist attacks with limited resources. American Political Science Review, 101, 527–541.
Powell, R. (2009). Sequential, nonzero-sum “Blotto”: Allocating defensive resources prior to attack. Games and Economic Behavior, 67, 611–615.
Sandler, T. (2014). The analytical study of terrorism: Taking stock. Journal of Peace Research, 51(2), 257–271.
Sandler, T. (2015). Terrorism and counterterrorism: An overview. Oxford Economic Papers, 67, 1–20.
Sandler, T., & Arce, D. G. (2003). Terrorism & game theory. Simulation & Gaming, 34, 319–337.
Sandler, T., & Lapan, H. E. (1988). The calculus of dissent: An analysis of terrorists’ choice of targets. Synthese, 76, 245–261.
Sandler, T., & Siqueira, K. (2006). Global terrorism: Detterence versus pre-emption. Canadian Journal of Economics, 19(4), 1370–1387.
Sandler, T., & Siqueira, K. (2009). Games and terrorism: Recent developments. Simulation & Gaming, 40, 164–192.
Sandler, T., Tschirhart, J. T., & Cauley, J. (1983). A theoretical analysis of transnational terrorism. American Political Science Review, 77, 36–54.
Schneider, F., Brück, T., & Meierrieks, D. (2015). The economics of counterterrorism: A survey. Journal of Economic Surveys, 29, 131–157.
Siqueira, K., & Sandler, T. (2008). Defensive counterterrorism measures and domestic politics. Defence and Peace Economics, 19, 405–413.
Skaperdas, S. (1992). Cooperation, conflict, and power in the absence of property rights. American Economic Review, 82(4), 720–739.
Tullock, G. (1980). Efficient rent seeking. In J. Buchanan, R. Tollison, & G. Tullock (Eds.), Toward a theory of the rent-seeking society (pp. 97–1120). College Station: Texas A&M University Press.
Acknowledgements
We thank the editors and two anonymous referees for helpful comments, which have significantly improved the qualify of the paper. An earlier version of this paper was presented at Jinan University, South China Normal University, and the 28th International Conference on Game Theory. We thank seminar and conference participants especially Timothy Mathews, Shane Sanders, Xianbin Wang, and Zhibo Wang for helpful comments. Any remaining errors are ours.
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Jiao, Y., Luo, Z. A model of terrorism and counterterrorism with location choices. Public Choice 179, 301–313 (2019). https://doi.org/10.1007/s11127-018-0559-8
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11127-018-0559-8