Abstract
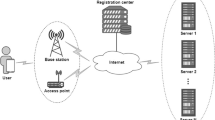
Authentication and key agreement (AKA) provides flexible and convenient sercices. Most traditional AKA protocols are designed to apply in single-server environment, where a user has to register at different servers to access different types of network services and the user have to remember or manage a large number of usernames and passwords. Later, multi-server AKA protocols resolve the repeated registration problem of single-server AKA protocols, where a user can access different servers to get different services using a single registration and the same username and password. Recently, in 2015, Lu et al proposed a light-weight ID based authentication and key agreement protocol for multi-server architecture, referred to as LAKA protocol. They claimed their protocol can overcome all shortcomings which existed in Xue et al’s protocol. Unfortunately, our further research shows that LAKA protocol still suffers from server spoofing attack, stolen smart card attack etc. To overcome the weakness of LAKA protocol, an energy-efficient and lightweight authentication and key agreement protocol for multi-server architecture is proposed (abbreviated to ELAKA). The ELAKA protocol not only provides the security features declared by LAKA protocol, but also has some other advantages. First, the ELAKA protocol can realize authentication and key agreement just by three handshakes with extremely low communication cost and computation cost between users and servers, which can achieve a delicate balance of security and performance. Second, ELAKA protocol can enable the user enjoy the remote services with privacy protection. Finally the ELAKA protocol is proved secure against known possible attacks by using BAN logic. As a result, these features make ELAKA protocol is very suitable for computation-limited mobile devices (such as smartphone, PAD, tablets) in comparison to other related existing protocols.





Similar content being viewed by others
References
Florencio, D., & Herley, C. (2007). A large-scale study of web password habits. In Proceedings of the 16th international conference on world wide web (pp. 657–666).
Liao, Y., & Wan, S. (2009). A secure dynamic ID based remote user authentication scheme for multi-server environment. Computer Standards & Interfaces., 31(1), 24–29.
He, D., & Wang, D. (2015). Robust biometrics-based authentication scheme for multiserver environment. IEEE Systems Journal, 9(3), 816–823.
Odelu, V., Das, A. K., & Goswami, A. (2015). A secure biometrics-based multi-Server authentication protocol using smart cards. In Information forensics and security, IEEE transactions (pp. 1953–1966).
Shen, H., Gao, C., He, D., et al. (2015). New biometrics-based authentication scheme for multi-server environment in critical systems. Journal of Ambient Intelligence and Humanized Computing, 6(6), 825–834.
Chuang, M., & Chen, M. (2014). An anonymous multi-server authenticated key agreement scheme based on trust computing using smart cards and biometrics. Expert Systems with Applications, 41(4), 1411–1418.
Mishra, D., Das, A. K., & Mukhopadhyay, S. (2014). A secure user anonymity-preserving biometric-based multi-server authenticated key agreement scheme using smart cards. Expert Systems with Applications, 41(18), 8129–8143.
Choi, Y., Nam, J., Lee, D., et al. (2014). Security enhanced anonymous multiserver authenticated key agreement scheme using smart cards and biometrics. The Scientific World Journal, 2014(4), 281305. https://doi.org/10.1155/2014/281305.
Lin, H., Wen, F., Du, C. (2015). An improved anonymous multi-server authenticated key agreement scheme using smart cards and biometrics. Wireless Personal Communications, 84(4), 2351–2362. https://doi.org/10.1007/s11277-015-2708-4.
Li, C., Lee, C., Chen, H., et al. (2015). Cryptanalysis of an anonymous multi-server authenticated key agreement scheme using smart cards and biometrics. In IEEE international conference on information networking (ICOIN)2015 (pp. 498–502).
Zan, Y., Liu, W., & Wei, J. (2014). Negotiation sheme of multi-server authentication key based on dynamic ID. Journal of Information Engineering University, 15(6), 654–663.
Baruah, K., Banerjee, S., & Dutta, M. (2015). An improved biometric-based multi-server authentication scheme using smart card. International Journal of Security and its Applications, 9(1), 397–408.
Kuo, W., Wei, H., & Chen, Y. et al. (2015). An enhanced secure anonymous authentication scheme based on smart cards and biometrics for multi-server environments. In IEEE 10th Asia joint conference on information security (AsiaJCIS), 2015 (pp. 1–5).
Chaudhry, S. A. (2015). A secure biometric based multi-server authentication scheme for social multimedia networks. Multimedia Tools and Applications, 75(20), 1–16. https://doi.org/10.1007/s11042-015-3194-0.
Chaudhry, S.A., Naqvi, H., Farash, M. S., et al. (2015). An improved and robust biometrics-based three factor authentication scheme for multiserver environments. Journal of Supercomputing, 1–17. https://doi.org/10.1007/s11227-015-1601-y.
Chaudhry, S. A., Naqvi, H., Sher, M., et al. (2015). An improved and provably secure privacy preserving authentication protocol for SIP. Peer-to-Peer Networking and Applications pp. 1–15.
Chaudhry, S. A., Farash, M. S., Naqvi, H., et al. (2015). An enhanced privacy preserving remote user authentication scheme with provable security. Security and Communication Networks, 8(18), 3782–3795.
He, D., Kumar, N., & Chilamkurti, N. (2015). A secure temporal-credential-based mutual authentication and key agreement scheme with pseudo identity for wireless sensor networks. Information Sciences, 321, 263–277.
Farash, M. S., Turkanovi, M., Kumari, S., et al. (2016). An efficient user authentication and key agreement scheme for heterogeneous wireless sensor network tailored for the internet of things environment. Ad Hoc Networks, 36, 152–176.
Xue, K., Hong, P., & Ma, C. (2014). A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. Journal of Computer and System Sciences, 80(1), 195–206.
Lu, Y., Li, L., & Peng, H., et al. (2015). A lightweight ID based authentication and key agreement protocol for multiserver architecture. International Journal of Distributed Sensor Networks, 1–9. https://doi.org/10.1155/2015/635890
Lin, H., Wen, F., & Du, C. (2016). An improved lightweight pseudonym identity based authentication scheme on multi-server environment. In Wireless communications, networking and applications (pp. 1115–1126). Springer, New Delhi.
Dawson, E., Lopez, J., Montenegro, J. A. et al. (2004). BAAI: biometric authentication and authorization infrastructure proc. In IEEE International conference information technology: research and education (ITRE) (pp. 274–278).
Li, X., Niu, J., & Khan, M. K., et al. (2013). Robust biometrics based three-factor remote user authentication scheme with key agreement proc. In IEEE international symposium biometrics security technologies (pp. 105–110).
Makrushin, A., Scheidat, T., & Vielhauer, C. (2012). Improving reliability of biometric hash generation through the selection of dynamic handwriting features[M]//Transactions on data hiding and multimedia security VIII (pp. 19–41). Berlin: Springer.
Zhang, Q., Yin, Y., Zhan, D., et al. (2014). A novel serial multimodal biometrics framework based on semisupervised learning techniques. IEEE Trans Inf Forensic Secur, 9(10), 1681–1694.
Pathak, M. A., Raj, B., Rane, S. D., & Smaragdis, P. (2013). Privacy-preserving speech processing: cryptographic and string-matching frameworks show promise. IEEE Signal Process, 30(2), 62–74.
Wang, Y. (2012). Password protected smart card and memory stick authentication against off-line dictionary attacks. In 27th IFIP TC 11 information security and privacy conference, SEC 2012. Boston: Springer, pp. 489–500.
Wang, D., Ma, C., & Wang, P. et al. (2012). Robust smart card based password authentication scheme against smart card security breach. Cryptology ePrint Archive, Report 2012/439.
Xie, Q., Liu, W., Wang, S., et al. (2014). Robust password and smart card based authentication scheme with smart card revocation. Journal of Shanghai Jiaotong University, 19(4), 418–424.
Pippal, R., Jaidhar, C., & Tapaswi, S. (2013). Robust smart card authentication scheme for multi-server architecture. Wireless Personal Communications, 72(1), 729–745.
Taylor, G., Moore, S., Anderson, R. et al. (2012). Improving smart card security using self-timed circuits. In IEEE 18th international symposium on asynchronous circuits and systems. IEEE computer society (pp. 211–211).
Zhang, N., Zang, Y., & Tian, J. (2015). The integration of biometrics cryptography a new solution for secure identity authentication. Journal of Cryptologic Research, 2(2), 159–176.
Li, X., Niu, J., Kumari, S., et al. (2015). An enhancement of a smart card authentication scheme for multi-server architecture. Wireless Personal Communications, 80(1), 175–192.
Kilinc, H., & Yanik, T. (2014). A survey of SIP authentication and key agreement schemes. IEEE Communications Surveys & Tutorials, 16(2), 1005–1023.
Wander, A. S., Gura, N., & Eberle, H. et al. (2005). Energy analysis of public-key cryptography for wireless sensor networks. In Third IEEE international conference on pervasive computing and communications, PerCom.
Acknowledgements
This work was partly supported by the National Natural Science Foundation of China under Grant 61402275, 61402015, 61373150, 61572246, 61272436, Shaanxi Province Natural Science Basic Research Program Funded Project 2016JM6069, the Scientific Research Foundation for the Returned Overseas Chinese Scholars of MOHRSS, the Fundamental Research Funds for the Central Universities under Grant GK201603012, GK201402004, the Innovation Fund Designated for Graduate Students of Shaanxi Normal University (2015CXS022).
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Liu, X., Li, Y., Qu, J. et al. ELAKA: Energy-Efficient and Lightweight Multi-Server Authentication and Key Agreement Protocol Based on Dynamic Biometrics. Wireless Pers Commun 100, 767–785 (2018). https://doi.org/10.1007/s11277-018-5348-7
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5348-7