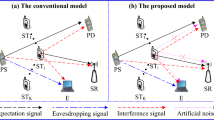
Abstract
Cognitive radio networks (CRNs) have a shortcoming in that attackers can increase their ability to disturb secondary users (SUs). This paper focuses on jamming attacks in the physical layer, in which several attackers try to interrupt SUs by injecting the interference into their communications. Once a jammer transmits interfering signals on the channel during the defined time, all ongoing transmissions on this channel will be corrupted. It is quite difficult for SUs to protect a single-hop data transmission from jammers. So, obtaining a solution for secure multi-hop data transmission in the presence of jammers becomes a more challenging task in CRNs. This paper investigates a strategy to find the optimal route and channels for transmission between cognitive transmitters and receivers in the presence of jammers in CRNs. In this scenario, the jammers are located randomly and their jamming behavior is assumed to follow a Gaussian distribution. We provide an optimal link–channel pair allocation scheme in which the secondary transmitter (the source) selects the best relay and a suitable channel for each hop in the source-to-destination route to protect the information intended to the secondary receiver (the destination) from the jammers. Simulation results prove the efficiency of the proposed scheme in a CR network.








Similar content being viewed by others
References
Federal Communications Commission. (2002). FCC spectrum policy task force report, ET Docket, No. 02–135.
Wyglinski, A. M., Nekovee, M., & Hou, Y. T. (2009). Cognitive radio communications and networks: principles and practice. New York: Elsevier.
Wang, B., & Liu, K. J. R. (2011). Advances in cognitive radio networks: A survey. IEEE Journal of Selected Topics in Signal Processing, 5(1), 5–23.
Haykin, S. (2005). Cognitive radio: Brain-empowered wireless communications. IEEE Journal on Selected Areas in Communications, 23(2), 201–220.
Mitola, J., & Maguire, G. (1999). Cognitive radio: Making software radios more personal. IEEE Personal Communications, 6(4), 13–18.
Shu, Z., Qian, Y., & Ci, S. (2013). On physical layer security for cognitive radio networks. IEEE Network, 27(3), 28–33.
Sharma, R., & Rawat, D. (2014). Advances on security threats and countermeasures for cognitive radio networks: A survey. IEEE Communications Surveys and Tutorials, 17(2), 1023–1043.
Li, H., & Han, Z. (2010). Dogfight in spectrum: Combating primary user emulation attacks in cognitive radio systems, part I: Known channel statistics. IEEE Transactions on Wireless Communications, 9(11), 3566–3577.
Brown, T. & Sethi, A. (2007). Potential cognitive radio denial-of-service vulnerabilities and protection countermeasures: A multi-dimensional analysis and assessment. In Proceedings of IEEE International Conference on Cognitive Radio Oriented Wireless Network Communications (pp. 456–464).
Zhang, L., Zhang, R., Liang, Y., Xin, Y., & Cui, S. (2010). On the relationship between the multi-antenna secrecy communications and cognitive radio communications. IEEE Transactions on Communications, 58(6), 1877–1886.
Xu, W. et al. (2004). Channel surfing and spatial retreats: Defenses against wireless denial of service. In Proceedings of the 3rd ACM workshop wireless security, Philadelphia, PA (pp. 80–89).
Attar, A., Tang, H., Vasilakos, A. V., Yu, F. R., & Leung, V. C. M. (2012). A survey of security challenges in cognitive radio networks: Solutions and future research directions. In Proceedings of the IEEE (pp. 3172–3186). https://doi.org/10.1109/JPROC.2012.2208211.
Sydir, J., & Taori, R. (2009). An evolved cellular system architecture incorporating relay stations. IEEE Communications Magazine, 47(6), 115–121.
Ruan, L. Z., & Lau, V. K. N. (2010). Decentralized dynamic hop selection and power control in cognitive multi-hop relay systems. IEEE Transactions Wireless Communications, 9(10), 3024–3030.
Zhang, Q., Feng, Z., Yang, T., & Li, W. (2016). Optimal power allocation and relay selection in multi-hop cognitive relay networks. Wireless Personal Communications, 86(3), 1673–1692.
Ho-Van, K. & Sofotasios, P. C. (2013). Bit error rate of underlay multi-hop cognitive networks in the presence of multipath fading. In 2013 fifth international conference on ubiquitous and future networks (ICUFN), Da Nang (pp. 620–624). https://doi.org/10.1109/ICUFN.2013.6614893.
Wang, W., Kwasinski, A. & Han, Z. (2014). A routing game in cognitive radio networks against routing-toward-primary-user attacks. In IEEE wireless communications and networking conference (pp. 2510–2515). https://doi.org/10.1109/WCNC.2014.6952783.
Wu, Y., Wang, B., Liu, K., & Clancy, T. (2012). Anti-jamming games in multi-channel cognitive radio networks. IEEE Journal on Selected Areas in Communications, 30(1), 4–15.
Wang, Q., Ren, K., Ning, P., & Hu, S. (2016). Jamming-resistant multiradio multichannel opportunistic spectrum access in cognitive radio networks. IEEE Transactions on Vehicular Technology, 65(10), 8331–8344.
Adem, N., Hamdaoui, B. & Yavuz, A. (2015). Pseudorandom time-hopping anti-jamming technique for mobile cognitive users. In 2015 IEEE globecom workshops, (pp. 1–16). https://doi.org/10.1109/GLOCOMW.2015.7414043.
Arunthavanathan, S., Goratti, L., Maggi, L., De Pellegrini, F. & Kandeepan, S. (2014). On the achievable rate in a D2D cognitive secondary network under jamming attacks. In 2014 9th international conference on cognitive radio oriented wireless networks and communications, (pp. 39–44). https://doi.org/10.4108/icst.crowncom.2014.255665.
Wang, P. & Henz, B. (2014). Throughput analysis of channel surfing in jammed single-hop wireless networks. In 2014 wireless telecommunications symposium, (pp. 1–8). https://doi.org/10.1109/WTS.2014.6834998.
Zou, Y. (2017). Physical-layer security for spectrum sharing systems. IEEE Transactions on Wireless Communications, 16(2), 1319–1329.
Mokari, N., Parsaeefard, S., Saeedi, H., & Azmi, P. (2014). Cooperative secure resource allocation in cognitive radio networks with guaranteed secrecy rate for primary users. IEEE Transactions on Wireless Communications, 13(2), 1058–1073.
Liu, W., Sarkar, M. Z. I., Ratnarajah, T., & Du, H. (2017). Securing cognitive radio with a combined approach of beamforming and cooperative jamming. IET Communications, 11(1), 1–9. https://doi.org/10.1049/iet-com.2016.0114.
Zhao, R., Yuan, Y., Fan, L., & He, Y. C. (2017). Secrecy performance analysis of cognitive decode-and-forward relay networks in nakagami- \(m\) fading channels. IEEE Transactions on Communications, 65(2), 549–563.
Acknowledgements
This research was supported by Basic Science Research Program through the National Research Foundation of Korea (NRF) funded by the Ministry of Education (2015R1D1A1A09057077) as well as by the MEST (2017R1D1A1B03029448).
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Thanh, P.D., Vu-Van, H. & Koo, I. Secure Multi-hop Data Transmission in Cognitive Radio Networks Under Attack in the Physical Layer. Wireless Pers Commun 103, 1615–1631 (2018). https://doi.org/10.1007/s11277-018-5871-6
Published:
Issue Date:
DOI: https://doi.org/10.1007/s11277-018-5871-6