Abstract
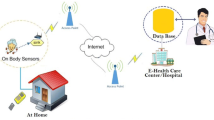
In recent years, the Internet of Things (IoT) has gained increasing popularity due to the usage of Internet-enabled devices. However, Internet-enabled devices, also known as smart devices, share the information using an insecure channel, i.e., the Internet. Hence, the security and privacy of shared information remain the biggest concern. To ensure both security and privacy, many smart card based and biometric based schemes have been proposed for different Internet-based applications. Telecare Medical Information System (TMIS) is such an application which makes medical treatment easier by interacting with the patient and doctors. However, the transmission of the patient’s private information over an insecure channel is prone to several attacks. In order to protect the medical privacy of the patient and the reliability of the system, both the patient and medical server should be mutually authenticated. In this paper, we propose a three factor-based authentication scheme for health care system using IoT enabled devices (TFASH) that are secure and more efficient than other relevant schemes. We use Elliptic Curve Cryptography (ECC) for the scheme due to its smaller key size and high level of security. The session key security and the mutual authentication of the TFASH scheme have been proved using Real-Or-Random (ROR) model and Burrows–Abadi–Needham (BAN) logic. The simulation result of the proposed scheme shows that the scheme is safe under the OFMC and CLAtSe models. Moreover, compared to the existing schemes, the TFASH scheme provides better communicational and computational cost, which makes it suitable for practical use.



Similar content being viewed by others
References
Alemdar H, Ersoy Cem (2010) Wireless sensor networks for healthcare: a survey. Comput Netw 54(15):2688–2710
Amin R, Biswas GP (2015) A secure three-factor user authentication and key agreement protocol for tmis with user anonymity. J Med Syst 39(8):78
Amin R, Biswas GP (2015) An improved rsa based user authentication and session key agreement protocol usable in tmis. J Med Syst 39(8):79
Amin R, Islam SKH, Biswas GP, Khan MK, Kumar N (2015) An efficient and practical smart card based anonymity preserving user authentication scheme for tmis using elliptic curve cryptography. J Med Syst 39(11):180
Amin R, Kumar N, Biswas GP, Iqbal R, Chang V (2018) A light weight authentication protocol for iot-enabled devices in distributed cloud computing environment. Future Generation Comput Syst 78:1005–1019
Armando A, Basin D, Boichut Y, Chevalier Y, Compagna L, Cuéllar J, Hankes Drielsma P, Héam P-C, Kouchnarenko O, Mantovani J, et al. (2005) The avispa tool for the automated validation of internet security protocols and applications. In: International conference on computer aided verification, pp 281–285. Springer
Arakala A, Jeffers J, and Horadam KJ (2007) Fuzzy extractors for minutiae-based fingerprint authentication. In: Lee S-W, Li SZ (eds) Advances in biometrics, pp 760–769, Berlin, Heidelberg, 2007. Springer Berlin Heidelberg
Arshad H, Nikooghadam M (2014) Three-factor anonymous authentication and key agreement scheme for telecare medicine information systems. J Med Syst 38(12):136
AVISPA Automated Validation of Internet Security Protocols and Applications. http://www.avispa-project.org/, 2015
Bellare M, Pointcheval D, Rogaway P (2000) Authenticated key exchange secure against dictionary attacks. In: International conference on the theory and applications of cryptographic techniques, pp 139–155. Springer
Belguith S, Kaaniche N, Laurent M, Jemai A, Attia R (2020) Accountable privacy preserving attribute based framework for authenticated encrypted access in clouds. J Parallel Distributed Comput 135:1–20
Belguith S, Kaaniche N, Laurent M, Jemai A, Attia R (2018) Phoabe: Securely outsourcing multi-authority attribute based encryption with policy hidden for cloud assisted iot. Comput Netw 133:141–156
Chaudhry SA, Naqvi H, Shon T, Sher M, Farash Mohammad Sabzinejad (2015) Cryptanalysis and improvement of an improved two factor authentication protocol for telecare medical information systems. J Med Syst 39(6):66
Chaudhry SA, Khan MT, Khan MK, Shon T (2016) A multiserver biometric authentication scheme for tmis using elliptic curve cryptography. J Med Syst 40(11):230
Debiao He, Jianhua Chen, Rui Zhang (2012) A more secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1989–1995
Dodis Y, Reyzin L, Smith A (2004) Fuzzy extractors: How to generate strong keys from biometrics and other noisy data. In International conference on the theory and applications of cryptographic techniques, pages 523–540. Springer
Dolev Danny, Yao Andrew (1983) On the security of public key protocols. IEEE Trans Inform Theory 29(2):198–208
Fan C-I, Lin Y-H (2009) Provably secure remote truly three-factor authentication scheme with privacy protection on biometrics. IEEE Trans Inform Forensics Secur 4(4):933
Fan W, Lili X, Kumari S, Li X (2017) A privacy-preserving and provable user authentication scheme for wireless sensor networks based on internet of things security. J Ambient Intell Human Comput 8(1):101–116
Giri D, Maitra T, Amin R, Srivastava PD (2015) An efficient and robust rsa-based remote user authentication for telecare medical information systems. J Med Syst 39(1):145
He D, Wang D (2014) Robust biometrics-based authentication scheme for multiserver environment. IEEE Syst J 9(3):816–823
He D, Kumar N, Chen J, Lee C-C, Chilamkurti Naveen, Yeo Seng-Soo (2015) Robust anonymous authentication protocol for health-care applications using wireless medical sensor networks. Multimedia Syst 21(1):49–60
Irshad A, Sher M, Nawaz O, Chaudhry SA, Khan I, Kumari S (2017) A secure and provable multi-server authenticated key agreement for tmis based on amin et al. scheme. Multimedia Tools Appl 76(15):16463–16489
Islam SkH, Khan MK (2014) Cryptanalysis and improvement of authentication and key agreement protocols for telecare medicine information systems. J Med Syst 38(10):135
Jia X, He D, Kumar N, Raymond Choo K-K (2018) Authenticated key agreement scheme for fog-driven iot healthcare system. Wirel Netw. pp 1–14
Kocher P, Jaffe J, Jun B (1999) Differential power analysis. In: Advances in cryptology–CRYPTO’99, pp 789–789. Springer, 1999
Lamport L (1981) Password authentication with insecure communication. Commun ACM 24(11):770–772
Lee Tian-Fu (2013) An efficient chaotic maps-based authentication and key agreement scheme using smartcards for telecare medicine information systems. J Med Syst 37(6):9985
Lee JK, Ryu SR, Yoo KY (2002) Fingerprint-based remote user authentication scheme using smart cards. Electronics Letters 38(12):554–555
Lee T-F, Chang I-P, Lin T-H, Wang C-C (2013) A secure and efficient password-based user authentication scheme using smart cards for the integrated epr information system. J Med Syst 37(3):9941
Li Q, Guo M, Chang E-C (2008) Fuzzy extractors for asymmetric biometric representations. In: 2008 IEEE computer society conference on computer vision and pattern recognition workshops, pp 1–6
Li C-T, Hwang M-S (2010) An efficient biometrics-based remote user authentication scheme using smart cards. J Netw Comput Appl 33(1):1–5
Li J, Sha F, Zhang Y, Huang X, Shen J (2017) Verifiable outsourced decryption of attribute-based encryption with constant ciphertext length. Security Commun Netw , 2017
Maitra T, Islam SKH, Amin R, Giri D, Khan Muhammad Khurram, Kumar Neeraj (2016) An enhanced multi-server authentication protocol using password and smart-card: cryptanalysis and design. Security Commun Netw 9(17):4615–4638
Messerges TS, Dabbish EA, Sloan RH (2002) Examining smart-card security under the threat of power analysis attacks. IEEE Trans Comput 51(5):541–552
Mir O, Nikooghadam M (2015) A secure biometrics based authentication with key agreement scheme in telemedicine networks for e-health services. Wirel Personal Commun 83(4):2439–2461
Mishra D, Mukhopadhyay S, Chaturvedi A, Kumari S, Khan Muhammad Khurram (2014) Cryptanalysis and improvement of yan et al.’s biometric-based authentication scheme for telecare medicine information systems. J Med Syst 38(6):24
Michael Burrows, Martin Abadi, and Roger M Needham. A logic of authentication. In: Proceedings of the royal society of London A: Mathematical, Physical and Engineering Sciences, volume 426, pages 233–271. The Royal Society, 1989
Pawar P, Jones V, Van Beijnum B-JF, Hermens H (2012) A framework for the comparison of mobile patient monitoring systems. Journal of Biomedical Informatics 45(3):544–556
Raghupathi W, Raghupathi V (2014) Big data analytics in healthcare: promise and potential. Health Inform Sci Syst 2(1):3
Srinivas J, Mishra D, Mukhopadhyay S, Kumari S (2018) Provably secure biometric based authentication and key agreement protocol for wireless sensor networks. J Ambient Intell Human Comput 9(4):875–895
Soni P, Pal AK, Islam SKH (2019) An improved three-factor authentication scheme for patient monitoring using wsn in remote health-care system. Comput Methods Programs Biomed 182:105054
Tan Zuowen et al (2013) An efficient biometrics-based authentication scheme for telecare medicine information systems. Network 2(3):200–204
Tan Z (2014) A user anonymity preserving three-factor authentication scheme for telecare medicine information systems. J Med Syst 38(3):16
Wei J, Xuexian H, Liu W (2012) An improved authentication scheme for telecare medicine information systems. J Med Syst 36(6):3597–3604
Wu F, Li X, Sangaiah AK, Xu L, Kumari S, Wu L, Shen J (2018) A lightweight and robust two-factor authentication scheme for personalized healthcare systems using wireless medical sensor networks. Future Generation Comput Syst 82:727–737
Xiao D, Liao X, Deng S (2007) A novel key agreement protocol based on chaotic maps. Inform Sci 177(4):1136–1142
Xin X, Zhu P, Wen Q, Jin Z, Zhang Hua, He Lian (2013) A secure and efficient authentication and key agreement scheme based on ecc for telecare medicine information systems. J Med Syst 38(1):9994
Xue K, Hong P, Ma C (2014) A lightweight dynamic pseudonym identity based authentication and key agreement protocol without verification tables for multi-server architecture. J Comput Syst Sci 80(1):195–206
Yan X, Li W, Li P, Wang J, Hao Xinhong, Gong Peng (2013) A secure biometrics-based authentication scheme for telecare medicine information systems. J Med Syst 37(5):9972
Zhu Zhian (2012) An efficient authentication scheme for telecare medicine information systems. J Med Syst 36(6):3833–3838
Zhen-Yu W, Lee Y-C, Lai F, Lee H-C, Chung Yufang (2012) A secure authentication scheme for telecare medicine information systems. J Med Syst 36(3):1529–1535
Zhang L, Zhu Shaohui (2015) Robust ecc-based authenticated key agreement scheme with privacy protection for telecare medicine information systems. J Med Syst 39(5):49
Zhou L, Li X, Yeh K-H, Chunhua S, Chiu W (2019) Lightweight iot-based authentication scheme in cloud computing circumstance. Future Generation Comput Syst 91:244–251
Author information
Authors and Affiliations
Corresponding author
Additional information
Publisher's Note
Springer Nature remains neutral with regard to jurisdictional claims in published maps and institutional affiliations.
Rights and permissions
About this article
Cite this article
Sahoo, S.S., Mohanty, S. & Majhi, B. A secure three factor based authentication scheme for health care systems using IoT enabled devices. J Ambient Intell Human Comput 12, 1419–1434 (2021). https://doi.org/10.1007/s12652-020-02213-6
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s12652-020-02213-6