Abstract
MANETs are collection of independent nodes, which communicate with each other to perform a task. Broadcasting methods are widely used in this infrastructureless networks. Although broadcasting is easy to implement and a method to perform routing and safety functions, in a wide and high mobility MANET it is a difficult and expensive task to achieve. It is required that the underlying algorithm used for communication must consider parameters such as neighborhood density, the size and shape of the network, and the efficient use of channel. Probabilistic strategies are frequently used, as they do not introduce additional latency. Several researchers have proposed using various parameter instances which are managed dynamically, for instance, the change in the number of neighbor nodes and corresponding change in retransmission probability. But the authors did not optimize the parameters for specific environments. The proposed work in this research article suggests and determines the most efficient strategy for each node to decide the retransmission probability according to its neighborhood density, available bandwidth and remaining energy of a node. It describes a tool combining a network simulator (ns-2) and a particle swarm optimization algorithm. Then, it is applied to the MANET broadcasting problem. The simulation results show that the proposed particle swarm optimization probabilistic broadcasting (PSOPB) scheme is reliable and efficient in comparison with the other artificial intelligence broadcasting schemes such as elitist simulated binary evolutionary algorithm (ESBEA), multi-objective problems with Pareto front solution (MOP_PF) and efficient fuzzy logic-based probabilistic broadcasting (EFPB).
Similar content being viewed by others
1 Introduction
The mobile ad hoc network (MANET) is defined as an arrangement of movable nodes conveying via remote associations with no previous system base. The mobile nodes can be portable nodes, cell phone or some other hardware with a remote system gadget. MANETs were primarily employed to create the foundation of network systems simpler in the relief work subsequent to a disaster.
The various purposes of these nodes are: data sharing, game playing, transmitting traffic data, etc. In signal propagation like limiting factors (distance and/or obstructions), every node has a limiting exposure.
In such a surroundings, if a node desires to send a message outside its coverage area, in any case one of the neighbors through whom it can communicate must give consent to transmit its message. Various kinds of communications include unicast, multicast and broadcast. In unicast there is single source to single destination communication, in multicast a single source to various destination communication and in broadcast a source transmits to each and every node within its area of coverage. Broadcast is the most extensively employed in MANETs, particularly for transmitting safety messages as well as routing information. Because the wireless channel (for example, bandwidth) is low and restricted, the communication should be controlled efficiently and it implies that the communication should avoid redundant repeated transmissions.
The bandwidth utilization depends on the quantity of nodes that are in the same coverage area. In a crowded environment, if each node broadcasts each message immediately, it is received, the figure of collisions will rapidly increase, stopping extremely relevant as well as time-dependent messages from getting access to the shared wireless channel. In a less crowded environment where we are assuming a realistic propagation model, if nodes hardly transmit the message, the broadcasting sequence might be wrecked. With respect to retransmissions, the conduct of the nodes must rely on the setting. The issue is the manner in which to impart viably without pointlessly soaking the channel. A lot of researches focus on message broadcasting techniques in MANETs. In [1, 2], the author proposes several ways to reduce redundancy, conflicts as well as collisions in mobile ad hoc networks.
Retransmission is variable with probability according to the number of adjacent nodes. In [1], the authors have proposed a classification of two types of nodes relying on a known threshold t. Those nodes having a number of adjacent nodes more than t fit into class A.The remaining nodes belong to class B. The entire messages transmitted and received at nodes B are given greater priority. In [2], the retransmission probability P lies among a lower bounded and an upper bounded limit; P decreases if the total quantity of neighboring nodes is more than a known threshold, otherwise P increases. In [3], the authors have put forward a philanthropic communication method that discriminates messages by their significance. This system is said to be philanthropic for the reason that all node’s within the network does not consider only about their own benefit. In addition, it considers the relation and the possible recipient’s advantages to allocate precedence to the messages. So in all of these techniques, deciding the values of the factors (like lowered and higher bounds of probability as well as threshold values) is the most important difficulty. In best cases, a small number of authors have presented procedures to adjust these factors or to calculate them, but they have not optimized them for a variety of situations. In this article, we put forward a scheme that uses three parameters: the node density, remaining energy and available bandwidth to adjust the probability of broadcasting through fuzzy logic and particle swarm optimization. Employing these three factors, we have designed a self-reliable scheme that considers the network topology framework in relation. Our goal is to reduce the broadcasting storm problem which is due to the contention and collision of broadcast packets and has opened a new window of research issues. The remainder of this article is organized as follows. Section 2 presents different methods of broadcasting in wireless ad hoc networks. Section 3 describes concepts of particle swarm optimization. Section 4 describes our approach, i.e., PSOPB which consists in combining a PSO and a network simulator. In Sect. 5, the proposed method is evaluated and the results are discussed. Section 6 presents the concluding remarks and outlines future work.
2 Related work
The objective of optimization of the broadcasting schemes in mobile ad hoc networks is to decrease the quantity of surplus broadcast messages with no decrease in reachability, as well as to increase the latency. The broadcasting schemes can be categorized into five groups [2, 5]: one is simple flooding, second is probabilistic broadcasting, third is counter-based broadcasting, forth is area-based and the fifth one is neighbor knowledge-based methods. Every node transmits every message precisely once using the simple flooding strategy. In the event of repetition, the copied duplicates of the message are disposed of. This procedure gives intriguing results in a decently thick environment. In any case, when the thickness is elevated, numerous handed-off messages might be repetitive, as well as waste the channel data transmission.
The probabilistic broadcasting schemes [1, 5, 6] intend to improve the simple flooding technique. Once a node receives a packet, whether the node promotes or discards it depends on a known probability. However in the probabilistic scheme, determining the suitable value of the probability is one of the challenges. In [7], the authors considered the probability values between 0.6 and 0.8 as the optimal, but it is obvious that these values are not probable to be optimal for all kinds of cases. If the probability is considered to be 1, this scheme does not remain probabilistic. The concept of counter-based schemes [2, 8] is based on the number of times a message is delivered to a node, which means that greater a message is acknowledged by a single node, the less will an additional area be covered when this node broadcasts the same message. A counter with an initial value of 1 is set whenever a node gets a message for the first time and then assigns a random assessment delay known as RAD, which is a time selected in a particular period. If the same message is received every time while RAD expires, the counter is increased by 1. After the RAD expires, the message is only broadcasted whenever the counter is smaller than a specified threshold. If not, the message is dropped. But an extra latency is involved in this scheme. The additional coverage area is the main deciding factor while forwarding a message in area-based techniques. The area-based scheme does not think about nodes’ presence within the additional area [4]. To find out the extra coverage area, the node may utilize the Euclidian distance among itself as well as every node that has earlier transmitted the message in the distance-based technique, otherwise from the geographical coordinates in the location-based technique. As the signal strength can be employed to estimate the distance, the GPS is not requisite in the distance-based scheme. In both distance-based as well as location-based schemes, a RAD is allocated before the message is transmitted or discarded. In neighbor information-based methodologies, the nodes employ “Hello” packets to build a one-hop or two-hop neighbors records. These rundowns are suffixed to the telecast bundles so that the recipient (r) can contrast the transmitter rundown with its own particular rundown. This examination decides the extra nodes that will get the message if r advances it. For stagnant or less versatile systems, it is a reasonable strategy. When the node speed is high, the data about the neighbors turn out to be rapidly off base. In [9], the authors put forward an upgradation of the information-based schemes. The authors employed a cellular multi-objective genetic scheme to get the values of the parameters that assist in reviewing for forwarding a message. There is one more version of the neighbor information-based schemes known as multi-point relay (MPR) [10] recommended by the Hypercom panel of the INRIA1 laboratory. To decrease the quantity of surplus transmissions of a packet within a network, every node selects some of the nodes from their neighboring nodes to which they will transmit the messages. The chosen nodes are defined as MPRs. As soon as a node transmits a packet on the radio channel, the entire neighbors will get it; however, only the multi-point relay of the source node will further transmit the message, which shows that every node must have a record of all the nodes that have been selected as their “repeater”. The multi-point relays choose between the one-hop neighbors so that they allow the node that has selected them to arrive at its entire two-hop neighbors. The aim is to have the minimum record of multi-point relay in the network which optimizes transmission and reception. A full duplex connection is required by the MPRs. The scheme explained in this work uses probabilistic broadcasting. This kind of broadcasting was chosen for the reason that it does not engage additional latency, in contrast to other schemes like counter-based, area-based as well as neighbor-knowledge-based schemes. Also, the category of probabilistic broadcasting used here is the artificial intelligence. The broadcasting scheme employed here is of an artificial intelligence type, which is used to tune the forwarding probability of the nodes. So in this category, we mainly employ genetic algorithms to tune the forwarding probability. In [11], a genetic algorithm is employed to estimate the forwarding probability. Additional parameters like the amount of replicates that a known node rebroadcasts to a receiving a packet, stoppage between replicates as well as time to live (TTL) for a packet must be taken into account to calculate the fitness function. There are three parameters to be reduced: the first one is the number of collisions; the second is the propagation time; the third is the number of retransmissions. The different density scenarios in VANET are assessed by the authors for the proposed scenario. In [12], a multi-objective genetic algorithm is employed to optimize probabilistic broadcast in adverse situations. The multi-objective problem differs from the single objective optimization problem in that in the multi-objective problem several output metrics are used to acquire the set of nondominating keys (Pareto front). In [13], an efficient fuzzy logic-based probabilistic broadcasting for the AODV protocol is used to reduce overheads. The fuzzy-based logic criteria make decisions which are based on some of the important parameters affecting broadcasting such as the number of neighbors, bandwidth available and remaining energy. The simulation result shows that the proposed algorithm is efficient and reliable with respect to the consumed power, throughput, overhead, collision rate and it also maintains low normalized routing load as compared to AODV and other routing protocols proposed in the literature in which simple flooding or fixed probability broadcasting is used. In this paper, we use a very recent evolutionary algorithm, i.e., particle swarm optimization [14–21]. The proposed scheme is based on the available bandwidth, remaining energy and node density of nodes where the RREQ packets are not broadcasted at fixed probability, but the broadcasting probability depends on the these three factors. The proposed work in this research work suggests and determines the most efficient strategy for each node to decide the retransmission probability according to its neighborhood density, available bandwidth and remaining energy of a node. It illustrates a tool joining a network simulator (ns-2) along with a particle swarm optimization technique. Then, it is employed in the MANET broadcasting problem. The simulation outcomes show that the proposed particle swarm optimization probabilistic broadcasting (PSOPB) scheme is reliable and efficient in comparison with the other artificial intelligence broadcasting schemes such as elitist simulated binary evolutionary algorithm (ESBEA), multi-objective problems with Pareto front solution (MOP_PF) and efficient fuzzy logic-based probabilistic broadcasting (EFPB).
3 Work description
In two-dimensional PSO, each particle is thought to be a probable key to the numerical optimization issue in a two-dimensional space [17–24]. The PSO process based on the above conception can be explained as follows. The bird flocking process optimizes a certain object function. Every agent identifies its preeminent value so far (\(\mathrm{p}_\mathrm{best})\) as well as its XY location. Moreover, every agent has the knowledge of the preeminent value within the group (g\(_\mathrm{best})\) between \(p_\mathrm{bests}\). For changing its location, every agent employs the present velocity as well as the distance from p\(_\mathrm{best}\) and g\(_\mathrm{best}\). The changes can be characterized in requisites of velocity. The velocity of every agent can be modified using the subsequent equation.
where
-
v \(_{{i}}\) is the velocity of agent i,
-
Rand uniformly distributed random number ranges 0–1,
-
s \(_{{i}}\) is the present location of agent i,
-
p\(_{\mathrm{besti}}\) is the pbest of agent i,
-
g\(_\mathrm{best}\) is the gbest of the group.
From the above equation, a definite velocity that steadily acquires a velocity nearer to p\(_\mathrm{best}\) and g\(_\mathrm{best}\) can be obtained. The existing position can be customized by the subsequent equation:
where
-
\(S^{{k}}\) is the present location,
-
\(S^{{k+1}}\) is the adapted location,
-
\(V_{\mathrm{orig}}\) is the present velocity,
-
\(V_{\mathrm{mod}}\) is the adapted velocity,
-
\(V_{\mathrm{pbest}}\) is the velocity based on p\(_\mathrm{best},\)
-
\(V_{\mathrm{gbest}}\) is the velocity based on g\(_\mathrm{best}.\)
A. Estimation of metrics
-
Number of neighbors (N)
Number of neighbors [22] of any node i can be known at a physical layer by sending HELLO packets at regular intervals.
-
Bandwidth available (BA)
In our PSOPB algorithm, each node is responsible for calculating the available bandwidth within a path. Let \(\beta \) be the bandwidth available as well as C be the link capacity related with single-hop neighbor for any node i [23]. \(A_\mathrm{R}\) is the collective allocated rates for all incoming as well as outgoing flows of packets. Therefore, the summation of the allocated incoming as well as outgoing flow rates of packets and the available bandwidth on the route must be equivalent to the link capacity C \(_{i}\) which can be articulated by the following equation:
Knowing the link capacity \(C_{{i}},\) the bandwidth available is calculated from the following equation:
-
Remaining energy of the node (RE).
We employ the energy utilization rate as the factor to illustrate the remaining energy of any node i. The energy utilization rate is represented as EU\(_{{ i}}\). The energy utilization of any node is because of the transmitting, receiving as well as overhearing of a packet for a node, which can be calculated using the following Eq. (5):
where P \(_{\mathrm{r}}\), P \(_{\mathrm{s}}\) and P \(_{\mathrm{o}}\) are the energy utilized by any node when any node i is receiving, sending or overhearing a packet; N \(_{\mathrm{r}}\), N \(_{\mathrm{s}}\) and N \(_{\mathrm{o}}\) are the number of the three types of packets, respectively; T is the time duration of the node i energy utilization. Thus, EU\(_{{i}}\) is the average energy utilization rate of the node i. Then the remaining time for the node i to utilize its energy, where RT\(_{{i}}\), can be calculated using the following equation:
where RE\(_{i}\) indicates the remaining battery energy of the node i and can be calculated from its physical layer.
4 Particle swarm optimization-based probabilisitc broadcasting (PSOPB)
The proposed PSOPB algorithm forecasts the node density, remaining energy and available bandwidth based on factors such as relative mobility of the nodes, energy drain rate as well as link capacity, respectively. It is illustrated below.
A. Fuzzy logic-based probability determination in PSOPB
This technique involves the prediction of broadcasting probability by the fuzzy logic technique. We have employed Mamdani’s method in the inference process as it is more frequently used in applications The steps to determine the fuzzy rule-based interference are as follows: there are five steps as shown in Fig. 1 to get the crisp value from our FIS system.
-
1.
Every rule of the antecedent in Table 1 is evaluated in the first step.
-
2.
Then in the second step, rule conclusion is achieved.
-
3.
Conclusion aggregation is done in the third step.
-
4.
The fourth step is defuzzification where the defuzzifier calculates the crisp values of the output variables, i.e., probability of broadcasting (\(P_{{i}}\)) depending upon its membership function using Eq. (7), i.e., centre of gravity (COG) method.
$$\begin{aligned} P_i = \frac{\displaystyle \int \limits _V y\times \mu ( y)\mathrm{d}(y)}{\displaystyle \int \limits _V \mu ( y)\mathrm{d}( y)}. \end{aligned}$$(7) -
5.
In the fifth step, the defuzzified output is considered as input to the RREQ probabilistic broadcasting module of the AODV. In this work, fuzzy logic is rooted in the NS2 simulator to analyze the network performance with different input parameters which are dynamic in nature.
After executing these five steps, parameters of the simulation is passed on to the network simulator. After simulating the code, the log files are then sent to the log analyzer from where again the values of objective functions are sent to the fuzzy inference engine of PSOPB.
Figure 2 shows the flowchart for PSOPB. Table 1 shows the membership value of the inputs (N, BA, RE) and fuzzy logic system rules. Figure 3a–c shows the input membership function for inputs (N, BA, RE) and Fig. 3d shows the output membership function (P \(_{i})\).
B. Advantages of PSOPB
So, the proposed scheme (PSOPB) has the following advantages as compared to other existing protocols:
-
In the proposed algorithm, we intend to tune the probability of broadcasting using particle swarm optimization algorithm that is easier to implement and very efficient in the global search.
-
In the PSOPB scheme, RREQ broadcasting is optimized through a multi-objective optimization problem after evaluating the nodes’ condition which depends on three parameters that are better than the original probability schemes, where fixed probability or blind flooding is used.
-
Using the PSOPB scheme, the nodes having more energy, available bandwidth and less numbers of neighbors are used more which further increases the network lifetime.
5 Performance analysis
A. Simulation setup and parameters
In this section, we evaluate and compare the performance of the proposed particle swarm optimization-based probabilistic broadcasting (PSOPB) algorithm with the performance of the following broadcasting schemes which employ artificial intelligence such as elitist simulated binary evolutionary algorithm (ESBEA), multi-objective problems with Pareto front solution (MOP_PF) and efficient fuzzy logic-based probabilistic broadcasting (EFPB). Network simulator, NS2 [24–27], has been employed to assess the modified AODV using the particle swarm optimization-based probabilistic broadcasting (PSOPB) scheme. The mobility approach that has been employed in the entire simulations was the random way point. Also, the IEEE 802.11 Distributed Coordination Function (DCF) has been used as the MAC layer protocol in this setup. In all the cases, the nodes send a constant bit rate (CBR) data traffic between the source and destination over User Datagram Protocol (UDP). The transmission range of mobile nodes is set to 100 m. The 100 nodes are located evenly in grid form initially over the region of 1500 m \(\times \) 1500 m. The energy consumed while transmission and receiving can be calculated from the following equations:
where V is the operating voltage, \(I_{\mathrm{tr}}\) and I \(_{\mathrm{re}}\) are the corresponding currents for transmission and receiving, and T \(_{\mathrm{p}}\) is the corresponding time for transmitting and receiving.
We have taken V = 4.734V, I\(_{\mathrm{tr}} = \) 281 mA and I\(_{\mathrm{re}} =\) 205 mA as per the energy consumption data of Lucent WaveLAN wireless network card [28] in our simulation. The initial energy for each node is set to be 100 J. The node density is varied from 0 to maximum 10, 20, 30, 40, 50, 60, 70, 80, 90 and 100 to evaluate the the performance of particle swarm optimization-based probabilistic broadcasting scheme implemented on AODV routing protocols. The simulation parameters are shown in Table 2
B. Results discussion
The parameters that have been taken to analyze the network performance and protocols [29] are consumed power, throughput and routing overhead.
-
Consumed power This is defined as the average of power consumed by all nodes of the network. As seen in Fig. 4, PSOPB uses less energy per node as compared to the other three protocols. Mainly, the battery usage of PSOPB gets better in contrast to that of EFPB and MOP_PF. The PSOPB performs best at each and every point of the node density range. The ESBEA protocol uses additional battery in contrast to EFPB and A PSOPB. As the number of nodes increases, the energy consumption of ESBEA implemented networks enhances as compared to all protocols taken into consideration. Also, the ESBEA protocol employs a method that regularly revises knowledge about neighboring nodes because of implementation of evolutionary algorithm which considers every time new environment and as a result utilizes further energy. As we increase the density of the node within a network, necessary updates increase and therefore performance degrades, particularly when network mobility is present.
-
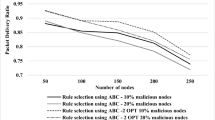
Throughput It computes the network consistency in providing information to the destination. So, throughput can be defined as the number of packets incoming at the sink in one millisecond. Data throughput of all four protocols is shown in Fig. 5. PSOPB performs well with average dense networks till the network size remains within 50 nodes. Among PSOPB and EFPB protocols, nodes are not required to have information about the route between two nodes, which decreases the total control packets required for the route discovery process. ESBEA as well as the MOP_PF perform badly in contrast to the other protocols. This is for the reason that these are multi-objective evolutionary algorithm protocols, and simulation parameter revisions are required, which create comparatively more packet overhead and an obstruction in big networks, particularly in mobile networks. It also decreases the bandwidth of the network. However, these protocols are superior for low data rate communication, as their self-revising helps in maintaining the connectivity to a certain extent as compared to the accessibility of bandwidth on behalf of application data.
-
Routing overhead Within a network, each and every control messages like RREQ, broadcasted and received, is actually known as routing overhead. Figure 6 illustrates the control message overhead of all protocols. As seen in the graph, PSOPB has lower control message overhead than the EFPB protocol. Whereas MOP_PF presents a mixed result because they use multi-objective problems which make them better than ESBEA, the ESBEA protocol shows poor performance as compared to all other protocols which further worsens the situation when the number of nodes increases from 30 to 40 because of updating of simulation parameters for different environments in evolutionary algorithms.
6 Conclusion
The purpose of this work is to apply the idea of PSO for deciding the probability in probabilistic broadcasting in MANETs. The speculative structure selected is based on the seek for food by swarms. Folks, add evolutionary benefit of membership information along with a crowd when a mission is given to them. This thought showed the way to seek out the resolution into an optimization issue. The preliminary plan of the particle swarm concept is to graphically reproduce the elegant and random management of a bird flock, the purpose of finding out patterns that manage the capability of birds to fly synchronously and to abruptly adjust the path by reorganizing in the best possible way. With the primary goal, the theory developed into a simple as well as capable optimization algorithm for deciding the rebroadcast probability. As compared to other probability-based broadcasting techniques, every node broadcasts with fixed probability without considering the node density, remaining energy and available bandwidth of the nodes. The proposed scheme in this paper decides the probability of the RREQ broadcast depending on the output of fuzzy controllers, which depend on the node density, remaining energy and available bandwidth of the nodes. PSOPB outperforms the other probabilistic broadcasting techniques based on artificial intelligence such as elitist simulated binary evolutionary algorithm (ESBEA), multi-objective problem with Pareto front solution (MOP_PF) and efficient fuzzy logic-based probabilistic broadcasting (EFPB). Moreover, PSOPB achieves better results as compared to elitist simulated binary evolutionary algorithm (ESBEA), multi-objective problem with Pareto front solution (MOP_PF) and efficient fuzzy logic-based probabilistic broadcasting (EFPB). Further, the same technique can be implemented also with the other parameters such as node velocity. It can be used in the route discovery phase and analyzed whether it can remove the broadcasting storm problem with increasing link stability.
References
Natesapillai K, Palanisamy V, Duraiswamy K (2010) Optimum density based model for probabilistic flooding protocol in mobile ad hoc network. Eur J Sci Res 39(4):577–588
Zhang Q, Agrawal DP (2005) Dynamic probabilistic broadcasting in manets. J Parallel Distrib Comput 65(2):220–233. doi:10.1016/j.jpdc.2004.09.006
Eichler S, Schroth C, Kosch T, Strassberger M (2006) Strategies for context-adaptive message dissemination in vehicular ah hoc networks. In: Proceedings of IEEE: 2006 Third Annual International Conference on Mobile and Ubiquitous Systems: Networking & Services, July 2006, pp 1–9
Williams B, Camp T (2002) Comparison of broadcasting techniques for mobile ad hoc networks. In: Proceedings of the ACM international symposium on mobile ad hoc networking and computing (MOBIHOC), pp 194–205
Hanashi AM, Siddique A, Awan I, Woodward M (2008) Dynamic probabilistic flooding performance evaluation of on-demand routing protocols in manets. In: CISIS ’08: proceedings of the 2008 International conference on complex, intelligent and software intensive systems, pp 200–204. IEEE ComputerSociety, Washington, DC. doi:10.1109/CISIS.2008.66
Hanashi AM, Awan I, Woodward M (2009) Performance evaluation based on simulation of improving dynamic probabilistic flooding in manets. In: WAINA ’09: proceedings of the 2009 International conference on advanced information networking and applications workshops, pp 458–463. IEEE Computer Society, Washington, DC. doi:10.1109/WAINA.2009.78
Li L, Halpern J, Haas Z (2002) Gossip-based ad hoc routing. In: Proceedings of the IEEE INFOCOM. IEEE Computer Society, USA
Yassein MB, Al-Dubai A, Khaoua MO, Al-jarrah OM (2009) New adaptive counter based broadcast using neighborhood information in manets. In: International symposium on parallel and distributed processing, pp 1–7. doi:10.1109/IPDPS.2009.5161179
Alba E, Dorronsoro B, Luna F, Nebro AJ, Bouvry P, Hogie L (2007) A cellular multiobjective genetic algorithm for optimal broadcasting strategy in metropolitan manets. Comput Commun 30(4):685–697. doi:10.1109/IPDPS.2005.4
Nguyen D, Minet P (2007) Analysis of mpr selection in the olsr protocol. In: AINAW ’07: proceedings of the 21st international conference on advanced information networking and applications workshops. IEEE Computer Society, Washington, DC, pp 887–892. doi:10.1109/AINAW.2007.94
Reina DG, Leon-Coca JM, Toral SL, Asimakopoulou E, Barrero F, Norrington P, Bessis N (2014) Multi-objective performance optimization of a probabilistic similarity/dissimilarity-based broadcasting scheme for mobile ad hoc networks in disaster response scenarios. Soft Comput 18:1745–1756
Abdou W, Henriet A, Bloch C, Dhouutaut D, Charlet D, Spies F (2011) Using a evolutionary algorithm to optimize the broadcasting methods in mobile ad hoc networks. J Netw Comput Appl 34:1794–1804
Kumar S, Mehfuz S (2016) Efficient Fuzzy Logic Based Probabilistic broadcasting for mobile ad hoc network. Int J Comput Intell Syst 9(4):666–675
Mehfuz S, Kumar S (2014) Two dimensional particle swarm optimization algorithm for load flow analysis. Int J Comput Intell Syst 7(6):1074–1082
Hinchey MG, Steritt R, Rouff C (2007) Swarms & Swarms Intelligence. J Comput 40(4):111–113
El-Zonkoly AM (2008) Optimal sizing of SSSC controllers to minimize transmission loss and a Novel Model of SSSC to study transient response. World Acad Sci Eng Technol 24:825–831
Kennedy J (1997) The particle swarm: Social adaptation of knowledge. In: Proceedings of IEEE International Conference on Evolutionary Computation, Indianapolis, Indiana. IEEE Service Center, Piscataway, NJ, pp 303–308
Sivanandam SN, Visalakshi P (2007) Multiprocessor scheduling using hybrid particle swarm optimization with dynamically varying inertia. Int J Comput Sci Appl 4(3):95–106
Lin L, Luo Q, Liu J, Long C (2008) An improved particle swarm optimization for reconfiguration of distribution network. IEEE Fourth Int Conf Nat Comput 3:453–457
Kennedy J, Eberhart R (1997) A Discrete binary version of the particle swarm algorithm. Proc IEEE Int Conf Syst Man Cybern 5:4104–4108
Vlachogiannis JG, Lee KY (2006) A comparative study on particle swarm optimization for optimal steady-state performance of power systems. IEEE Trans Power Syst 21(4):1718–1728
Mehfuz S, Kumar S (2015) Energy aware probabilistic broadcasting for mobile ad hoc network. In: Proceedings of the 2nd IEEE International Conference on Computing for Sustainable Global Development. New Delhi, pp 1028–1033
Vishnu KS, Sarita SB (2011) Agent based bandwidth reservation routing technique in mobile ad hoc networks. Int J Adv Comput Sci Appl 2:12
Ns-2 network simulator (2008). http://www.isi.edu/nsnam/ns/. Accessed 2 May 2008
CMU Monarch BPensions to NS-2 (2008). http://www.monarch.cs.cmu.edu/cmu-ns.html. Accessed 2 May 2008
Marc Greis’ Tutorial for the UCB/LBNL/VINT Network Simulator “ns” (2008). http://web.uct.ac.za/depts/commnetwork/tutorial_ns_full.pdf. Accessed 2 May 2008
Installing OLSR on NS-2 (2008). http://masimum.inf.um.es/um-olsr/html. Accessed 20 May 2008
Feeney L, Nilsson M (2001) Investigating the energy consumption of a wireless network interface in an ad hoc networking environment. In: Proc. 20th IEEE INFOCOM, Anchorage, USA, pp 1548–1557
Rahman A, Islam S, Talevski A (2009) Performance measurement of various routing protocol in ad-Hoc network. In: Proceedings of the International Multi Conference of Engineers and Computer Scientists (IMECS), no 1. Hong-Kong, pp 321–323
Author information
Authors and Affiliations
Corresponding author
Rights and permissions
About this article
Cite this article
Kumar, S., Mehfuz, S. Intelligent probabilistic broadcasting in mobile ad hoc network: a PSO approach. J Reliable Intell Environ 2, 107–115 (2016). https://doi.org/10.1007/s40860-016-0023-9
Received:
Accepted:
Published:
Issue Date:
DOI: https://doi.org/10.1007/s40860-016-0023-9