Abstract
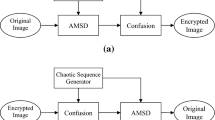
We propose here a transform which is a new kind of multi-level subband signal decomposition and reconstruction scheme. It is called Simplet which stands for Simple transform and is simple, easy to understand and perfectly reconstructible. No decomposition or reconstruction filter is explicitly required in Simplet. Another advantage of this transform is that the length of the decomposed components in each level of decomposition is equal to the length of the input signal. Computationally, Simplet can be made a constant time transform. There are various forms of Simplet that can be used in various applications of signal and image processing. Simplet is of two types. One is useful for multiresolution signal analysis and the other for signal distortion. We use the later type here for an encryption scheme. In the existing transforms, even when there is noise in the decomposed components, the reconstructed signal is perceptually intelligible. However, in Simplet the reconstructed signal is perceptually unintelligible when the decomposed components have noise in them. This property is made use of in our encryption scheme which first uses Simplet to protect the distinguishable features of the signal by decomposing it into two or more distorted components and then encrypts them by using a special sequence of numbers. This sequence is called Meitei Lock Sequence (MLS) and is generated from a non-zero key vector of an arbitrary length. An MLS is unique for a key vector. Once a signal is encrypted with an MLS, it can be decrypted only with that particular MLS. As an MLS is generated from an arbitrary vector, the search space for finding a particular MLS is very large and hence gives very tight security in our encryption scheme. We have found that the empirical correlation coefficient between an original signal and a decrypted signal using any decryption key that is different from (even if very close to) the actual key, is sufficiently small. The encryption scheme is fast as both the Simplet and MLS are fast algorithms.
Similar content being viewed by others
References
I. Daubechies, ''Orthonormal Bases of Compactly Supported Wavelets,'' Communication on Pure and Applied Mathematics, vol. 41, 1988, pp. 906–966.
I. Daubechies, Ten Lectures on Wavelets, Philadelphia, SIAM, 1992.
A. Croisier, D. Esteban, and C. Galland, ''Perfect channel splitting by use of interpolation and decimation techniques,'' Proceedings International Conference on Information Science and System, NJ, IEEE press, 1976.
Y.K. Singh and S.K. Parui, ''Criteria for Perfect Reconstructibility of Filters of QMF types,'' Technical Report, TR-CVPR/01/01, Indian Statistical Institute, May 2001. (Also available in the web site www:geocities.com/kiranisingh/criteria.html).
N. Bourbakis and C. Alexopoulos, ''Picture Data Encryption using Scan Patterns,'' Pattern Recognition, vol. 25, no.6, 1992, pp. 567–581.
Henry Ker-Chang Chang and Jiang-Long Liu, ''A Linear Quadtree Compression Scheme for Image Encryption,''Signal Processing: Image Communication, vol. 10, 1997, pp. 279–290.
Jui-Cheng Yen and Jiun-In Guo,"A new chaotic key based design for image encryption and decryption," Proceedings IEEE International Conference Circuits and Systems, vol. 4, 2000, pp. 49–52.
T.J. Chuang, and J.C. Lin, ''A New Multiresolution Approach to Still Image Encryption,'' Pattern Recognition Image Analysis, vol. 9, no. 3, 1999, pp. 431–436.
S. Sridharan, E. Dawson, and B. Goldburg, ''Fast Fourier Transform Based Speech Encryption System,'' IEEE Proc.-I Communication, Speech, Vision, vol. 138, no. 3, 1991, pp. 215–223.
Howard Cheng and Xiaobo Li, ''Partial Encryption of Compressed Images and Videos,'' IEEE Transactions on Signal Processing, vol. 48, no. 8, 2000, pp. 2439–2451.
Jinn-Ke Jan and Yuh-Min Tseng, ''On the security of Image encryption Method,'' Information Processing Letters, vol. 60, 1996, pp. 261–265.
Shujun Li and Xua Zheng, ''Cryptanalysis of a Chaotic Image Encryption Method,'' Proceedings. 2002 IEEE International Symposium on Circuits and Systems (ISCAS2002), vol. 2, May 2002, pp. 708–711.
C. Alexopoulos, N.G. Bourbakis, and N. Ioannou, ''Image Encryption Method Using a Class of Fractals,'' Journal of Electronic Imaging, vol. 4, no. 3, 1995, pp. 251–259.
Shujun Li and Xua Zheng, ''On the Security of an Image Encryption Method,'' Proceedings of 2002 IEEE Internaional Conference On Image Processing (ICIP 2002), vol. 2, Sept, 2002, pp. 925–928.
Author information
Authors and Affiliations
Rights and permissions
About this article
Cite this article
Singh, Y.K., Parui, S.K. Simplet and its Application in Signal Encryption. Multidimensional Systems and Signal Processing 15, 375–394 (2004). https://doi.org/10.1023/B:MULT.0000037347.82658.6c
Issue Date:
DOI: https://doi.org/10.1023/B:MULT.0000037347.82658.6c