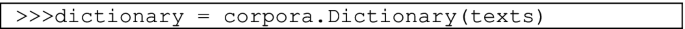Abstract
Cyber attackers gain access into systems, networks and cyberinfrastructure by escalating privileges to confidential information regardless of the efforts systems engineers put into security. The chess game between cyber offense and defense destabilizes the ability of organizations to protect their information assets. This research employs the lens of Activity Theory to study the interaction through the contradictions embedded between the cyber attackers and cyber defenders. These types of contradictions were forcefully created and simulated in the cyber security virtual lab at Florida State University for the purpose of facilitating real-world scenario-based learning experiences. Both network traffic data and interviews were collected in order to identify the boundary objects that intersect the two activity systems. Natural language processing (NLP) was adopted to explore and extract topics frequently used by both activity systems. Consciousness of cyber defense was expanded by creating contradictions, and boundary objects were identified by comparing the interactions between these two activity systems.
You have full access to this open access chapter, Download conference paper PDF
Similar content being viewed by others
Keywords
- Activity theory
- Activity system
- Human-computer interaction
- Sociotechnical systems
- Boundary objects
- Natural language processing (NLP)
- Cybersecurity
- System penetration
- Cloud security
1 Introduction
The pervasiveness of technology enables modern organizations to use computer-mediated and cloud-based technologies to share data, information and services through cyberspace. However, putting any information online faces a significant threat from malicious hackers. The global 2018 Verizon Data breach Investigation Report suggests that compared to the last ten years, the number of breaches remains high, while hacking techniques are getting more sophisticated and elaborate. In general, 68% of breaches take a month or longer to discover, and 94% of the security incidents—and 90% of confirmed data breaches—fall into the categories of web hacking, privilege misuse, cyber espionage, compromised assets, crimeware and payment card skimmers [1, pp. 6–7]. Cyber espionage does not occur as frequently as other forms of cyber-crime, but the fundamental goal of such attacks is to capture trade secrets and proprietary information. Attackers are now developing enhanced mechanisms to bolster penetration speed.
Though systems engineers and IT professionals work diligently to secure the network and block attackers, hackers seem to find better angles for system penetration, understanding system vulnerabilities and backdoors. Hence, they can more quickly perform loophole analysis. This finding suggests either one of two things: (1) systems engineers do not have a holistic view of the computing service environment when configuring the systems, or (2) hackers have a more creative, outside the box understanding of relevant security loopholes and system vulnerabilities, to adopt advanced tools for exploiting systems and networks. Willison and Warkentin [2] suggested that many violations can also be the result of simple mistakes, or non-malicious noncompliance, poor employee awareness training, low motivation and commitment or weak oversight from management. However, security breaches can also be malicious and deceptive in nature. Ho and Hancock [3,4,5,6] suggested that disgruntled insiders with malicious intent can threaten an organization’s ability to protect their own intellectual property. Our ability to make sense of group communication and group interaction can provide insights into these complex problems. Vance and Lowry [7] offered approaches to reduce insider abuse and policy violation, along with different mechanisms to increase awareness and accountability. Although other studies have offered ways to train, secure and monitor our computing environment (such as awareness training, auditing of electronic presence), there has not been an effective approach proposed to enhance cyber defense activities.
Cyber defense itself is an activity, and the activity itself provides the context [8]. As such, we propose to study the consciousness of cyber defense, and examine the interactions between attackers and defenders as an activity system, as well as to gain insight that might have practical implications for organizational information security. With this goal in mind, our research [9] aims to address the following questions: How do we uncover the consciousness of cyber defense in a way that can transform organizational information systems security? More specifically, what are the boundary objects created through the contradictions embedding between cyber attack teams and cyber defense teams that impact their knowledge and their cyber defense tactics?
We adopt the lens of Activity Theory [10] to examine the interactions and activities to capture the differences in motivation and behavior between cyber attackers and defenders. To do so, we (1) compare objects, goals, actions, tools, and operations of both groups and (2) examine how the social environment has shaped the values and skillsets demonstrated by each respective team. This will help identify the boundary objects created through contradicting values. In this paper we will first discuss the theoretical lens of activity theory from existing literature. Then, we will describe our own study framework, the research design, method, data collection, data analysis, and research limitations. Finally, this paper concludes with the research contribution to this field, and future works.
2 Activity Theory: Context and Conflict
Activity Theory first originated in the late 70s and early 80s through the work of Soviet developmental psychologist Leont’ev [11] as a response to the work of Vygotsky [12]. This theory embodies a concept in which activity is represented as the interaction between subject and object, and is further defined by the subject’s motive. Activity in this context is also a system of processes that reflect the subject’s motive. The original generation of this Activity Theory as developed by Vygotsky [12] focused on the interaction between human agents (subject) and the world (object) as mediated by tools and signs [13, 14]. Leont’ev [11] advanced Vygotsky’s [12] work by proposing a three-level model of activity. That is, activity does not occur without a motive. The subject would take certain actions directed towards a specific goal. An action is a conscious choice and a representation of progress toward a desired outcome. In this scenario, operations can be subconsciously performed or mediated by tools (e.g., technology). Leont’ev [11] advocated for the notion of collective activity rather than individual focus. However, Leont’ev [11] did not illustrate a model of collective activity until after Engeström [10, 15] proposed the expanded triangle representation and introduced the community, rules and norms, as well as division of labor which became the collective aspects and elements of an activity system, providing a root model of human activity [10, 16].
Since the conception of Activity Theory, it has been adopted in a wide range of domains and studies such as genre systems [17], writing instructions [17, 18], designing learning environments [19], innovation [20], organizational learning [21], strategic practices [22, 23], mobile health systems [24], incident control systems [24], ICT4D [25], CHAT [26, 27], and software development [28]. Kuutti [29,30,31,32] suggested this 3 × 6 (levels × elements) Activity Theory concept to be further adopted in information systems research (ISR) [29, 31], computer-supported cooperative work (CSCW) [32], and human computer interaction (HCI) [30] when studying organizational learning. The three (3) levels refer to top-tier executives, middle management and front-line workers in an organization. The six (6) elements refer to subject, object, tool, rule, community and division of labor of an activity system. Kuutti and Arvonen [32] criticized that limited view of CSCW design, and suggested re-conceptualizing the structure of (work) activity by defining an activity as a collective phenomenon, which is “work by multiple subjects sharing a common object, supported by information technology” (p. 234). Moreover, an activity not only exists in a material environment, but is historically developed and culturally mediated by a tool (instrument, i.e., information technology). Kuutti and Arvonen [32] illustrated the role and importance of “tools” being able to mediate organizational learning. That is, the creation of new information technology can assist in organizational learning, transfer shared knowledge, meaning, or materials, to construct, maintain and sustain a community (i.e., a community with shared interests). Interestingly, Kuutti and Arvonen [32] emphasized that “contradictions are the force behind the development of an activity” (p. 235). That is, the driving force for an organization to learn, to advance, and to grow is the existence of conflicts, contradictions, and tensions [10].
Since an activity is a collective phenomenon [32] that focuses on the interaction of human activity and consciousness [19, 30, 33] within its relevant context. Jonassen and Ronrer-Murphy [19] emphasized that “an activity cannot be understood or analyzed outside the context” (p. 62). Nardi [8] compared the differences between activity theory, situated action models, and distributed cognition, and emphasized that in activity theory, the unit of analysis is an activity itself whereas the situated actions views the “person-acting in settings” as a unit of analysis. An activity takes place in a particular situation [34]. Distributed cognition, on the other hand, requires a cognitive system composed of individuals and artifacts. The distributed cognition emphasizes the system as the unit of analysis. Distributed cognition is concerned with the structures of the system, and the transformations of these structures, the coordination among the individuals and artifacts, and the process of how individuals align or share information [8, p. 39]. Nardi [8] suggested that activity theory offers a richer framework that can help capture consciousness, intentionality, and history of human-computer interaction when studied in context. That is, context is not a random composite of people and artifacts, but rather a “specific transformative relationship between people and artifacts” (p. 38). People consciously and deliberately generate context through interacting with objects mediated by artifacts. In short, the subject is engaged in an activity, and the object held by the subject can motivate the activity, and can be transformed in the course of an activity (p. 37). An activity can be mediated by artifacts [29] such as signs, symbols, language, machines, information systems, and instruments, etc. That is, “the activity itself is the context” (p. 38).
To help explain this view of the context, Kaptelinin and Nardi [35] provided a checklist to define the “space” of context. Basically, the transformation of activity involves both internalization and externalization activities. Internalization refers to a cognitive process in the transformation of external activities to internal cognition. Externalization transforms the internal cognitive states or activities into external ones (such as for visualization or coordination purposes). This activity checklist includes the following: (1) identifying the hierarchies of goals, (2) actively transforming the objects in the social and physical aspects of the environment, (3) being able to internalize and externalize objects so transformation can take place, and (4) analyzing both history and potential changes in the environment for further development.
In order to understand organizational learning, Virkkunen and Kuutti [21] suggested that we revisit the units of analysis; the “activity system.” Organizational learning is a collective learning process. It involves complex interaction between six (6) elements of an activity system. Organizational learning is not only multifaceted and multi-phased, but is always local and situational (p. 293). After examining many frameworks, Virkkunen and Kuutti [21] suggested the unit of analysis for organizational learning as being an activity system. One of the key elements of an activity system is the “object,” which refers to the motive of the activity. The subject is motivated to take action to achieve the object. The outcome of an activity may likely become a component of another activity system, and thus the object is further transformed. Because of this transformation phenomenon, the activity system is always “internally heterogeneous” and contains “many competing and partly conflicting views” (p. 301). The contradictions of this process create opportunities for transformation; transitional objects becoming different elements (e.g., a tool, a community, a rule, or a division of labor) of another activity system, and this process represents the cycle of collective or “expansive” learning in an organization.
Contradictions generally refer to incompatible or opposite things [36, p. 369]. Contradictions create tension or opposition within an activity system, and this fosters change within organizations [24, p. 840]. However, Engeström and Sannino [36] emphasized that contradictions cannot be mixed with paradox, tension, inconsistency, conflict, dilemma or double bind (p. 370), and suggested that based on linguistic cues, contradictions can be identified and categorized into four types of discursive manifestations: dilemma (e.g., ‘but’), conflicts (e.g., ‘no’), critical conflict (e.g., descriptive metaphors), and double bind (e.g., using rhetorical questions) (p. 375). On the other hand, Allen and Brown [24] proposed the concept of congruencies, which foster reproduction (p. 841). Allen and Brown [24] studied technology-mediated organizational change through the lens of critical realism by analyzing the contradictions and congruencies within two scenarios: (case one) the paramedic treatment of heart attacks through the mobile health system, and (case two) the ambulance dispatch of an incident control system. In case one, the introduction of a new tool provides congruencies between the internal and the external motivation of the objects, which become a strong stabilizing influence on the activity system. In case two, when the subject accepts the conflicting use of the tools as part of the norm of the activity system, this acceptance leads to the transformation from contradictions into congruencies.
Karanasios [14] proposed a unified view of technology and activity, and worked to re-conceptualize the activity system in order to reposition the technology in terms of its role in resolving contradictions, but further argued for a new form of harmonized congruencies within the organization. Nardi [33] and Kaptelinin [37] pointed out that objects can represent the motivation of the activity system. To distinguish the motivation from the objects, and to control those objects without clearly defined boundaries—called “runaway objects”—the activity system would require and involve multiple and complex links between activities. Karanasios [14] identified this problem as a potential opportunity for the IS field to develop and advance the notion of runaway objects (p. 144), and to transform these runaway objects into something smaller and manageable.
In sum, consciousness of cyber defense can be found embedded in the social arrangements (e.g., motives and intents) and the mediated technologies (e.g., tools). The current study aims to find out how the consciousness of cyber defense manifests itself through creation of contradictions—or contradicting values—in two activity systems. Rather than identifying the differences in the discursive manifestations of contradictions [36], our study aims to identify the “boundary objects” spinning between the two activity systems that represent certain degrees of consciousness of cyber defense. Star and Griesemer [38] suggested that boundary objects are “objects” that are “enough to adapt to local needs, and “yet, robust enough to maintain a common identity across sites” (p. 393). That is, in two different activity systems, the consciousness of cyber defense can be recognized through the boundary objects “as a key process in developing and maintaining coherence across intersecting social worlds” (p. 393).
3 Study Framework
Cyber defense can be represented as an activity system (Fig. 1) where the outcome of the two activity systems is determined by whether the systems or networks have been protected or penetrated. Within a framework of cyber defense, we can assume that the subject is making sense of the object of activity [37]. The subject—as an individual or as a team—requires a long-term motive to defend their information assets, and take actions to achieve short-term goals in protecting these assets. The conscious choice of the subject in taking actions that will achieve certain outcomes is mediated by technologies such as firewalls, intrusion detection systems, networks, and various information systems. This activity system involves routine operations as well as activities occurring in confined conditions and situations [11].
This study aims to investigate the consciousness of the cyber defender as an activity system. In particular, we are interested in examining the interactive activities that explain the differences in behavior demonstrated by the attackers and defenders. Our study framework creates the contradicting values between cyber defense and offense by assigning four teams of cyber professionals (i.e., students with proficient system and network technical knowledge) with short-term goals to understand systems’ loopholes and vulnerabilities, and to protect their information assets—as well as long-term goals to acquire pragmatic know-how and skillsets in cyber defense. Each cyber defense team or cyber offense team is considered an activity system. When two competing activity systems are placed together, conflicts are created due to the overlapping outcomes. In this overlapping outcome, security incidents occur and system vulnerabilities are discovered. It is significant to study the relationships and interaction between cyber defenders and attackers in cyberspace where the two activity systems interact. Both theoretically and operationally, we can observe the contradictions of motives, goals, and conditions of cyber operations—for defenders as well as attackers—as they examine and assess system vulnerabilities. Consequently, individuals involved in both roles are likely to have very different motives.
4 Research Design
The research design of this study involved cybersecurity experiments using servers, workstations and network environments that were replicated in four distinct segments, which were enabled by virtual switches in the virtual lab, and managed by Hyper-V software. Four groups with four to five members were formed, each comprising a combination of systems engineers and penetration testers. Systems engineers protected their own systems while penetration testers attempted to exploit other teams’ systems.
The systems engineers first set up their own web servers, workstations, firewall, intrusion detection systems, honeypots, and network environment. Then, penetration testers from four (4) competing teams set up exploitation tools (i.e., Kali Linux) and stealthily began to penetrate other systems and networks—beginning with reconnaissance to scan the other three (3) groups’ networks and systems (Fig. 2). The penetration testers were given the freedom to exploit other teams’ systems and networks. We shall note that although the systems engineers and penetration testers take the same cybersecurity class, each team’s systems configuration settings and credentials differ and are determined within the team. Since these students have extensive systems’ knowledge, they are given the freedom to choose and implement their own tools and techniques in order to either (1) protect their own systems, information assets, possessions and territory, or to (2) penetrate and exploit other teams’ systems, information assets, possessions and territory.
5 Method
We collected both network traffic data as well as interviews from participants. To understand the consciousness of team interaction, this study employs a triangular mixed method approach by simultaneously collecting both quantitative data in the form of network traffic, and qualitative data in the form of semi-structured interviews. Furthermore, to capture the complexities of the participants’ interactive behavior, we observed their behavior as well as extrapolating the meaning of their interactions.
5.1 Data Collection
The experiments and the computing environments were set up on a server powered by Hyper-V management system and maintained by Florida State University College of Communication and Information Technical Support Team. Data was collected from an Advanced Information Security undergraduate class offered at the Florida State University during Spring 2017. There were 18 participants recruited for this studyFootnote 1. We first interviewed the systems administrators in the cyber defense team at the beginning phase of the experiments (January through March 2017). After the systems and networks were set up, we interviewed the penetration testers on the cyber offense team during the second phase of the experiment (April and May 2017). These participants had appropriate technical skills in areas like troubleshooting, intrusion detection, etc. because they all took prerequisite classes on Linux, web programming, networking, and database management. The tasks performed by the participants included protecting their systems, fixing vulnerabilities, and engaging in activities to prevent future attacks. A total of 28 interviews were conducted, recorded, and transcribed.
Two types of data were collected. The first type of data was the network traffic logged by the E-Detective traffic monitoring system. The second type of data was the interview transcript. Each participant participated in an hour-long face-to-face semi-structured interview, first as a systems administrator and then as a penetration tester. A member of the research team conducted the interviews with a prepared script of questions and recorded the open-ended responses for audio transcription. The interview included questions about the division of labor, context of work, tools used, activities involved in setting up the environment, in addition to the rules each team applied.
5.2 Network Traffic Data Analysis
We attempt to treat the number of DNS requests collected from network traffic as representations of routine activities. The number of requests collected from the network traffic is further processed by Python interface; a library used to create a data frame of the entire dataset, which is illustrated in Table 1.
Frequency counts were performed on the collected data frames to get the number of occurrences for each source IP. In our data collection and observation, four (4) IP addresses had the most DNS requests.
Appendix A illustrates the frequency of DNS requests. In retrospect, these high frequency counts reflect the design of the experiments because these four IP addresses were allocated as pfSense firewall used by four (4) teams.
However, this approach can at most help us identify the systems that were up and running, and interacting as the gateways (i.e., pfSense firewalls). We could objectively state that based on the requests made during the experiments, the boundary object that spans the four teams is the firewall (i.e., as represented by the most frequent DNS requests for pfSense); however, there was not much insight provided as to the consciousness of cyber defense.
5.3 Interview Data Analysis
We further analyzed the interview transcripts to explore the consciousness of the cyber defense teams during these exercises. The transcript data contained approximately 77,104 words from the 15 systems administrators, and approximately 68,295 words from the 13 penetration testers. Natural language processing (NLP) was adopted to process and analyze the transcripts. We developed Python codes to truncate the transcripts, and extract phrases and topics most frequently mentioned by the participants during the interview.
More specifically, we parsed the data on the basis of the context of the questions asked by the interviewer in the respective categories of the interacting activity systems (i.e., subject, object, tools, interacting outcomes, rules, community, and division of labor). The subject denotes the actors of the activity system; whether a systems administrator, or a penetration tester. The object denotes the intent, and motive of the actors—a cyber defender (i.e., systems administrator) or a cyber offender (i.e., penetration tester). Tools refer to the systems, software, applications, concepts, or techniques utilized by the actors to achieve their goals and outcome. Rules refer to how and what actors choose to communicate and base their decisions on. Community refers to where these actors mostly interact and obtain their knowledge. Division of labor refers to how actors divide and spread leadership and management tasks.
After dividing the data into the above categories, topic analysis was applied to extract the hidden topics from large volumes of text. Several Python modules such as NLTK (a natural language toolkit) and Gensim (a topic modeling toolkit) were leveraged to generate lists of topics from the respective categories. Below are the four steps programmed in the Python script:
-
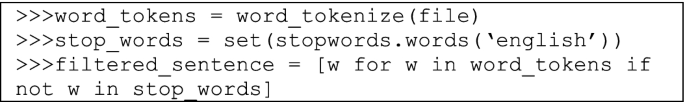
Step 1. Tokenize the transcript file, and eliminate all the stop words (e.g., of, the, an, on, etc.) using the NLTK module. A list of variables for the stop words was created to filter out the stop words from the tokenized list.
-
Step 2. After removing the stop words, we attempt to automate the process of extracting the topics from the large corpus of text obtained from the interview. A list of the words as a representation of the context was obtained for further analysis. We adopted an automated algorithm—LDA (Latent Dirichlet Allocation) from Gensim package to segregate topics. This module helps to determine the volume and percentage contribution of each topic so we get a sense of how important each topic is. We employed corpora, a method in the Gensim, to create the terms dictionary.
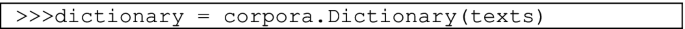
-
Step 3. A terms matrix was created based on the terms dictionary.

-
Step 4. An LDA model was created using the above variables.

6 Discussion
Several Venn diagrams represent the most frequently mentioned topics between two activity systems. From Figs. 3, 4, 5, 6 and 7, the number in brackets next to each word denotes frequency counts.
6.1 Addressing Research Questions
Consciousness of the two activity systems was identified through topic extraction from the transcripts. The subjects obviously have conflicting roles in the study. The responsibilities assigned to the systems administrators were aimed at cyber defense—which included setting up, configuring and protecting their own systems and cyber-infrastructure. They also have another conflicting role, which is to act as the penetration testers—cyber offense—poking at other teams’ systems for vulnerabilities, and attempting to break through competing teams’ cyber-infrastructure. Students were conscious of the cyber defense when they are facing potential hackers (i.e., classmates of other teams who aim to hack into their own information assets and systems). Through strategizing to exploit other teams’ systems’ vulnerabilities, students were aware of their own systems’ vulnerabilities and made attempts to bolster their own systems by fixing loopholes and solving problems.
Contradictions were manifested not only in the objects and outcome (Fig. 3), but also in the tools (Fig. 4), communities (Fig. 6), and division of labor (Fig. 7). We can identify the differences and conflicts of the intents and motives of the actors from the objects as derived from transcripts. In the cyber defense system (Fig. 3), subjects value the teamwork, and their aims were found in words such as ‘install,’ ‘scan,’ ‘protect,’ ‘monitor,’ and ‘block.’ The subjects of the cyber defense systems face ‘threats’ and ‘phishing’ attacks from the ‘attackers,’ and their strategies were to enhance security of the email systems, password, and firewalls. On the other hand, the penetration testers frequently used words such as ‘knowing,’ ‘learning,’ and their attempts were manifested in the words of ‘change,’ ‘create,’ ‘happen,’ and ‘correlate.’ Penetration testers in the cyber offense systems appeared to be more creative and innovative, collaborating about command line scripts, exploits, elevating administrative privileges, random-ware, flooding and taking down the competing teams’ networks. The word ‘team’ was mentioned 11 times in the cyber defense system, whereas the word ‘group’ was mentioned 29 times in the cyber offense system. The differences of the word choice (‘team’ vs. ‘group’) may imply that the cyber defense system appears to be more organized, whereas the cyber offense system tends to be more ad hoc. One common word; ‘tools’ seems to be a boundary object across the two activity systems [38,39,40]. Tools were frequently used in both activity systems, which imply that the professionals’ ability to know and use the right tools may have a significant impact on the success of each activity system to achieve their goals. We can confidently state that the boundary objects between both activity systems are the tools used.
There were about 10 tools utilized, such as Wireshark, zenmap, and Metasploit, etc. These were generally identified as being commonly adopted by both activity systems (Fig. 4). This implies that both activity systems may share similar knowledge and technological skillsets. It also implies that the same tools adopted by hackers to exploit other teams’ vulnerabilities can also be adopted by systems administrators to identify their vulnerabilities, and vice versa. From Figs. 3 and 4 we learn that knowledge of tools may be important to cyber defense. We further identified that the vulnerability scanners (e.g., Nikto, Nessus, etc.), antivirus (e.g., Kaspersky) and setting up honeypots (e.g., HoneyBot) were mentioned frequently in the cyber offense activity system. The cyber offense activity system also tended to explore the networks (e.g., NS Lookup, IP-spoof understanding the DNS) and to crack the passwords (e.g., OPHCrack, hash).
Moreover, regarding the communities, we found no interacting concepts—frequently-used words—between both activity systems (Fig. 6). However, we identified that the community referred to by the cyber defense system was the ‘company,’ whereas the community for the cyber offense system was the ‘industry.’ This difference can be easily explained by the fact that the cyber defense is the goal of IT systems administrators for the company. System administrators defend the company’s information assets, adhere to organizational goals, and interact frequently with their colleagues to ensure organizational policy is complied with and to safeguard organizational interests. However, in the cyber offense system, ‘industry’ is frequently mentioned in terms of community. They identified targets as ‘flags’ to capture. Cyber offense systems appear to be more open. Subjects in the cyber offense system constantly deal with problems, and figure out new ways to reach their goals. They tend to face ‘problems’ more ‘openly,’ and always are ready to ‘learn’ and find out ‘answers.’
Furthermore, there were no commonly used words—as boundary objects—found between the two activity systems regarding their division of labor (Fig. 7). But, we found that the cyber defense systems tend to be a little more organized as reflected in frequently used words such as ‘leader,’ ‘group,’ ‘team,’ ‘roles,’ and ‘we.’ The focus of cyber defense systems was mostly centered on the systems such as Linux, and the subjects in the cyber defense system spend ‘time’ on ‘working’ and ‘trying.’ By contrast, the cyber offense systems ‘maintain’ and ‘establish’ hidden connections with their targets. They do not shy away from using tools (e.g., Armitage), penetrating using techniques (e.g., analyzing TCP packets, SYN flooding, exploits) against targets’ systems (e.g., Ubuntu) and networks guarded by firewalls (e.g., Palo Alto Network firewalls, and pfSense). Subjects in the cyber offense system also have ad hoc ‘frameworks’ for ‘meetings’ and ‘schedules.’
Finally, when analyzing rules adopted by both activity systems, we identified ‘Internet’ and ‘checking’ as boundary objects, commonly used by both activity systems as they frequently check references and gained knowledge from the Internet (Fig. 5). Subjects in cyber defense systems use more applied technologies, frequently using words such as ‘running,’ ‘monitoring,’ ‘downloading,’ and reading ‘logs.’ The subjects in cyber offense systems, on the other hand, tend to take initiatives and use more creative terms such as ‘launch,’ ‘update,’ ‘give,’ and ‘ahead.’ The subjects in cyber defense systems also are more aware of the ‘environment’ through ‘discussion’ with their peers, and they always want to get ‘ahead.’
6.2 Limitations
This study has certain limitations. For example, the interview data is analyzed using quantitative natural language processing (NLP) approach to identify concepts and topics; thus, some contextual insights might be omitted.
7 Conclusions and Future Work
This study adopts Activity Theory to examine the interaction between cyber defense and offense activity systems. The simulation of interactions between two activity systems helps the participants to gain knowledge and insights from the expansive learning process and outcome. Contradictions to the objectives were created through the interaction between these two activity systems. The study identifies the creation of contradicting values, which assist in expanding participants’ learning in the domain of cybersecurity. The boundary objects found between two activity systems include the tools, the Internet and the inquiry/searching ‘skills’ involved in the process of checking for references. The future work will include a qualitative analysis of the interview data to derive context-specific insights, and the participants’ subjective consciousness in order to understand the contrast with the current objective approach—natural language processing (NLP).
The practical implications of the study inform the organizations, the practitioners, and the educational institutions to suggest that the best approach to learn, to teach and to enhance the consciousness of cyber defense is through the creation of contradictions; that is, looking through the lens of opposition in the activity systems in cyberspace.
Notes
- 1.
The study has been approved by the Florida State University Human Subject Committee, and obtained the Institution Review Board (IRB) protocols #2016.19676, #2017.22357, and #2018.25742.
References
Verizon 2018 Data breach investigations report. Verizon (2018). http://www.documentwereld.nl/files/2018/Verizon-DBIR_2018-Main_report.pdf. Accessed 5 Nov 2018
Willison, R., Warkentin, M.: Beyond deterrence: an expanded view of employee computer abuse. MIS Q. 37(1), 1–20 (2013)
Ho, S.M., Hancock, J.T., Booth, C.: Ethical dilemma: deception dynamics in computer-medicated group communication. J. Am. Soc. Inf. Sci. Technol. 68(12), 2729–2742 (2017)
Ho, S.M., et al.: Demystifying insider threat: language-action cues in group dynamics. In: Hawaii International Conference on System Sciences (HICSS-49). IEEE, Kauai (2016)
Ho, S.M., Kaarst-Brown, M., Benbasat, I.: Trustworthiness attribution: inquiry into insider threat detection. J. Assoc. Inf. Sci. Technol. 69(2), 271–280 (2018)
Ho, S.M.: Leader member exchange: an interactive framework to uncover a deceptive insider as revealed by human sensors. In: Proceedings of the 2019 52nd Hawaii International Conference on System Sciences (HICSS-52). Shidler College of Business, Maui (2019)
Vance, A., Lowry, P.B., Eggett, D.: Using accountability to reduce access policy violations in information systems. J. Manag. Inf. Syst. 29(4), 263–290 (2014)
Nardi, B.: Studying context: a comparison of activity theory, situated action models, and distributed cognition. In: Nardi, B. (ed.) Context and Consciousness: Activity Theory and Human-Computer Interaction, pp. 69–102. The MIT Press, Cambridge (1996)
Ho, S.M., von Eberstein, A., Chatmon, C.: Expansive learning in cyber defense: transformation of organizational information security culture. In: Proceedings of the 12th Annual Symposium on Information Assurance (ASIA 2017), pp. 23–28. Academic Track of the 20th Annual NYS Cyber Security Conference, Albany (2017)
Engeström, Y.: Expansive learning at work: toward an activity theoretical reconceptualization. J. Educ. Work 14(1), 133–156 (2001)
Leont’ev, A.N.: The problem of activity in psychology. Soviet Psychol. 13(2), 4–33 (1974)
Vygotsky, L.: Interaction between learning and development. In: Gauvain, M., Cole, M. (eds.) Readings on the Development of Children, pp. 34–40. Scientific American Books, New York (1978)
Miettinen, R., Paavola, S.: Reconceptualizing object construction: the dynamics of Building Information Modelling in construction design. Inf. Syst. J. 28(3), 516–531 (2018). Special Issue: Combined Special issues on Activity Theory and Global Sourcing and Development: New Drivers, Models and Impacts
Karanasios, S.: Toward a unified view of technology and activity: the contribution of activity theory to information systems research. Inf. Technol. People 31(1), 134–155 (2018)
Engeström, Y.: Learning by Expanding: An Activity-Theoretical Approach to Developmental Research, 2nd edn, p. 338. Cambridge University Press, New York (1987)
Karanasios, S., Allen, D.: Activity theory in information systems research. Inf. Syst. J. 28(3), 439–441 (2018). Special Issue: Combined Special issues on Activity Theory and Global Sourcing and Development: New Drivers, Models and Impacts
Russell, D.: Rethinking genre in school and society: an activity theory analysis. Writ. Commun. 14(4), 504–554 (1997)
Russell, D.: Activity theory and its implications for writing instruction. In: Petraglia, J. (ed.) Reconceiving Writing, Rethinking Writing Instruction, pp. 51–78. Lawrence Erlbaum Associates, Inc., Hillsdale (2002)
Jonassen, D.H., Ronrer-Murphy, L.: Activity theory as a framework for designing constructivist learning environments. Educ. Technol. Res. Dev. (ETR&D) 47(1), 61–79 (1999)
Miettinen, R.: The riddle of things: activity theory and actor-network theory as approaches to studying innovations. Mind Cult. Act. 6(3), 170–195 (1999)
Virkkunen, J., Kuutti, K.: Understanding organizational learning by focusing on “activity systems”. Acc. Manag. Inf. Technol. 10(4), 291–319 (2000)
Jarzabkowski, P.: Strategic practices: an activity theory perspective on continuity and change. J. Manag. Stud. 40(1), 23–55 (2003)
Jarzabkowski, P., Wolf, C.: An activity theory approach to strategy as practice. In: Golsorkhi, D., et al. (eds.) Cambridge Handbook of Strategy as Practice, pp. 165–183. Cambridge University Press, Cambridge (2015)
Allen, D., et al.: How should technology-mediated organizational change be explained? A comparison of the contributions of critical realism and activity theory. MIS Q. 37(3), 835–854 (2013)
Karanasios, S.: Framing ICT4D research using activity theory: a match between the ICT4D field and theory? Inf. Technol. Int. Dev. 10(2), 1–17 (2014)
Foot, K.A.: Cultural-historical activity theory: exploring a theory to inform practice and research. J. Hum. Behav. Soc. Environ. 24(3), 329–347 (2014)
Roth, W.-M.: Emotion at work: a contribution to third-generation cultural-historical activity theory. Mind Cult. Act. 14(1–2), 40–63 (2007)
Dennehy, D., Conboy, K.: Going with the flow: an activity theory analysis of flow techniques in software development. J. Syst. Softw. 133, 160–173 (2017)
Kuutti, K.: Activity theory and its applications to information systems research and development. In: Nissen, H.E., Klein, H.K., Hirschheim, R. (eds.) Information Systems Research: Contemporary Approaches and Emergent Traditions, pp. 529–549. Elsevier North-Holland, Inc., Amsterdam (1991)
Kuutti, K.: Activity theory as a potential framework for human-computer interaction research. In: Nardi, B.A. (ed.) Context and Consciousness: Activity Theory and Human-Computer Interaction, MIT Press, Cambridge (1996)
Kuutti, K.: Activity theory, transformation of work, and information systems design. In: Engeström, Y., Miettinen, R., Punamäki-Gitai, R.-L. (eds.) Perspectives on Activity Theory, pp. 1–360. Cambridge University Press, Cambridge (1999)
Kuutti, K., Arvonen, T.: Identifying potential CSCW applications by means of activity theory concepts: a case example. In: Proceedings of the 1992 ACM Conference on Computer-Supported Cooperative Work (CSCW 1992). ACM, Toronto (1992)
Nardi, B.: Activity theory and human-computer interaction. In: Nardi, B. (ed.) Context and Consciousness, pp. 7–16. The MIT Press, Cambridge (1996)
Suchman, L.A.: Plans and Situated Actions: The Problem of Human Machine Communication, p. 203. Cambridge University Press, Cambridge (1987)
Kaptelinin, V., Nardi, B.A., Macaulay, C.: Methods & tools: the activity checklist: a tool for representing the “space” of context. In: Interactions 1999, pp. 27–39. ACM, New York (1999)
Engeström, Y., Sannino, A.: Discursive manifestations of contradictions in organizational change efforts. J. Organ. Change Manag. 24(3), 368–387 (2011)
Kaptelinin, V.: The object of activity: making sense of the sense-maker. Mind Cult. Act. 12(1), 4–18 (2005)
Star, S.L., Griesemer, J.R.: Institutional ecology, ‘translations’ and boundary objects: amateurs and professionals in Berkeley’s Museum of Vertebrate Zoology, 1907-39. Soc. Stud. Sci. 19(3), 387–420 (1989)
Star, S.L.: This is not a boundary object: reflections on the origin of a concept. Sci. Technol. Hum. Values 35(5), 601–617 (2010)
Star, S.L.: The structure of ill-structured solutions: boundary objects and heterogeneous distributed problem solving. In: Distributed Artificial Intelligence, pp. 37–54. Elsevier (1989)
Acknowledgement
The authors wish to thank Alison von Eberstein for the contribution on the interview questionnaire, consent form, and the Institutional Review Board (IRB) protocol approved by Florida State University Human Subjects Committee. The authors also wish to thank Christy Chatmon for the effort on interviewing participants and data collection during Spring 2017, Vanessa Myron for the effort on transcribing interviews, and Sushmita Khan for the effort on interview data analysis during Fall 2018.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendix A
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Ho, S.M., Oliveira, D., Rathi, R. (2019). Consciousness of Cyber Defense: Boundary Objects for Expansive Learning Through Creation of Contradictions. In: Nah, FH., Siau, K. (eds) HCI in Business, Government and Organizations. Information Systems and Analytics. HCII 2019. Lecture Notes in Computer Science(), vol 11589. Springer, Cham. https://doi.org/10.1007/978-3-030-22338-0_28
Download citation
DOI: https://doi.org/10.1007/978-3-030-22338-0_28
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-22337-3
Online ISBN: 978-3-030-22338-0
eBook Packages: Computer ScienceComputer Science (R0)