Abstract
For identity-based encryption (IBE) with identity revocation, or simply revocable IBE (R-IBE), an indirect revocation method in which a trusted center (i.e., private key generator, PKG) initially generates all users’ long-term private keys and periodically issues time update keys for non-revoked users seems to be a flexible choice, because it invites a sender to generate ciphertexts without caring about revoked (and non-revocked) users. However, these computation and communication overheads in frequent time keys update operations remain as a daunting task for PKG. In order to alleviate the offload of PKG and improve its scalability in the quantum computers attack environment, Dong et al. recently extended the concept of R-IBE to support outsourcing computation with a semi-trusted key update cloud service provider (KU-CSP), and proposed an outsourced revocable lattice-based IBE (OR-IBE) scheme.
In this work, we show that the OR-IBE scheme of Dong et al. does not satisfy the correctness property of OR-IBE, meanwhile, it is not decryption key exposure resistance (DKER), a default security requirement for R-IBE. In addition, we provide a modification of their construction to be a correct and secure OR-IBE scheme. In particular, the first lattice-based OR-IBE scheme with DKER is introduced.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
References
Agrawal, S., Boneh, D., Boyen, X.: Efficient lattice (H)IBE in the standard model. In: Gilbert, H. (ed.) EUROCRYPT 2010. LNCS, vol. 6110, pp. 553–572. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-13190-5_28
Ajtai, M.: Generating hard instances of lattice problems (extended abstract). In: STOC, pp. 99–108. ACM (1996). https://doi.org/10.1145/237814.237838
Alwen, J., Peikert, C.: Generating shorter bases for hard random lattices. Theor. Comput. Sys. 48(3), 535–553 (2011). https://doi.org/10.1007/s00224-010-9278-3
Boneh, D., Franklin, M.: Identity-based encryption from the Weil pairing. In: Kilian, J. (ed.) CRYPTO 2001. LNCS, vol. 2139, pp. 213–229. Springer, Heidelberg (2001). https://doi.org/10.1007/3-540-44647-8_13
Boldyreva, A., Goyal, V., Kumar, V.: Identity-based encryption with efficient revocation. In: CCS, pp. 417–426. ACM (2008). https://doi.org/10.1145/1455770.1455823
Cash, D., Hofheinz, D., Kiltz, E., Peikert, C.: Bonsai trees, or how to delegate a lattice basis. In: Gilbert, H. (ed.) EUROCRYPT 2010. LNCS, vol. 6110, pp. 523–552. Springer, Heidelberg (2010). https://doi.org/10.1007/978-3-642-13190-5_27
Chen, J., Lim, H.W., Ling, S., Wang, H., Nguyen, K.: Revocable identity-based encryption from lattices. In: Susilo, W., Mu, Y., Seberry, J. (eds.) ACISP 2012. LNCS, vol. 7372, pp. 390–403. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-31448-3_29
Cheng, S., Zhang, J.: Adaptive-ID secure revocable identity-based encryption from lattices via subset difference method. In: Lopez, J., Wu, Y. (eds.) ISPEC 2015. LNCS, vol. 9065, pp. 283–297. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-17533-1_20
Dong, C., Yang, K., Qiu, J., et al.: Outsourced revocable identity-based encryption from lattices. Trans. Emerging Tel. Tech. 30, e3529 (2018). https://doi.org/10.1002/ett.3529
Gentry, C., Peikert, C., Vaikuntanathan, V.: Trapdoor for hard lattices and new cryptographic constructions. In: STOC, pp. 197–206. ACM (2008). https://doi.org/10.1145/1374376.1374407
Katsumata, S., Matsuda, T., Takayasu, A.: Lattice-based revocable (hierarchical) IBE with decryption key exposure resistance. In: Lin, D., Sako, K. (eds.) PKC 2019. LNCS, vol. 11443, pp. 441–471. Springer, Cham (2019). https://doi.org/10.1007/978-3-030-17259-6_15
Lee, K.: A generic construction for revocable identity-based encryption with subset difference methods. PLoS ONE 15(9), e0239053 (2020). https://doi.org/10.1371/journal.pone.o239053
Lee, K., Lee, D., Park, J.: Efficient revocable identity-based encryption via subset difference methods. Des. Codes Cryptogr. 85(1), 39–76 (2017). https://doi.org/10.1007/s10623-016-0287-3
Li, J., Li, J., Chen, X., et al.: Identity-based encryption with outsourced revocation in cloud computing. IEEE Trans. Comput. 64(2), 426–437 (2015). https://doi.org/10.1109/TC.2013.208
Libert, B., Vergnaud, D.: Adaptive-ID secure revocable identity-based encryption. In: Fischlin, M. (ed.) CT-RSA 2009. LNCS, vol. 5473, pp. 1–15. Springer, Heidelberg (2009). https://doi.org/10.1007/978-3-642-00862-7_1
Ma, X., Lin, D.: Generic constructions of revocable identity-based encryption. In: Liu, Z., Yung, M. (eds.) Inscrypt 2019. LNCS, vol. 12020, pp. 381–396. Springer, Cham (2020). https://doi.org/10.1007/978-3-030-42921-8_22
Micciancio, D., Peikert, C.: Trapdoors for lattices: simpler, tighter, faster, smaller. In: Pointcheval, D., Johansson, T. (eds.) EUROCRYPT 2012. LNCS, vol. 7237, pp. 700–718. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-29011-4_41
Nguyen, K., Wang, H., Zhang, J.: Server-aided revocable identity-based encryption from lattices. In: Foresti, S., Persiano, G. (eds.) CANS 2016. LNCS, vol. 10052, pp. 107–123. Springer, Cham (2016). https://doi.org/10.1007/978-3-319-48965-0_7
Qin, B., Deng, R.H., Li, Y., Liu, S.: Server-aided revocable identity-based encryption. In: Pernul, G., Ryan, P.Y.A., Weippl, E. (eds.) ESORICS 2015. LNCS, vol. 9326, pp. 286–304. Springer, Cham (2015). https://doi.org/10.1007/978-3-319-24174-6_15
Regev, O.: On lattices, learning with errors, random linear codes, and cryptography. In: STOC, pp. 84–93. ACM (2005) https://doi.org/10.1145/1060590.1060603
Seo, J.H., Emura, K.: Revocable identity-based encryption revisited: security model and construction. In: Kurosawa, K., Hanaoka, G. (eds.) PKC 2013. LNCS, vol. 7778, pp. 216–234. Springer, Heidelberg (2013). https://doi.org/10.1007/978-3-642-36362-7_14
Shamir, A.: Identity-based cryptosystems and signature schemes. In: Blakley, G.R., Chaum, D. (eds.) CRYPTO 1984. LNCS, vol. 196, pp. 47–53. Springer, Heidelberg (1985). https://doi.org/10.1007/3-540-39568-7_5
Sun, Y., Mu, Y., Susilo, W., et al.: Revocable identity-based encryption with server-aided ciphertext evolution. Theor. Comput. Sci. 2020(815), 11–24 (2020). https://doi.org/10.1016/j.tcs.2020.02.03
Takayasu, A., Watanabe, Y.: Lattice-based revocable identity-based encryption with bounded decryption key exposure resistance. In: Pieprzyk, J., Suriadi, S. (eds.) ACISP 2017. LNCS, vol. 10342, pp. 184–204. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-60055-0_10
Acknowledgments
The authors would like to thank the anonymous reviewers of NSS 2021 for their helpful comments and this research was supported by Guangxi key Laboratory of Cryptography and Information Security (Grant No. GCIS201907) and Natural Science Foundation of Henan Province (Grant No. 202300410508).
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A The ind-uka Security of OR-IBE
The ind-uka security model of OR-IBE considers the case that KU-CSP that can access to the master time update key muk is an attacker. In this security model, KU-CSP can request long-term private key, revocation, and decryption key queries. Since KU-CSP can issue an arbitrary time update key by using muk and \(\textsf {ok}_{\textsf {id}}\) (Note: KU-CSP owns all users’ identity outsourcing keys), there is a direct restriction that KU-CSP cannot request a long-term private key for the challenge identity \(\textsf {id}^{*}\) to prevent a simple attack. Finally, the goal of KU-CSP is the same as that in the ind-cpa security model, that is, to determine that the challenge ciphertext is completely random or correctly encrypted on the challenge \(\textsf {m}^{*}\) corresponding to \((\textsf {id}^{*},\textsf {t}^{*})\). A detailed definition of the ind-uka security is described as follows:
Definition 6
The ind-uka security of OR-IBE is described as the following game between the challenger \(\hat{\mathcal {C}}_{2}\) and adversary \(\mathcal {A}_{2}\):
-
\(\textsf {Initial} \): \(\mathcal {A}_{2}\) first declares a challenge identity and time pair \((\textsf {id} ^{*},\textsf {t} ^{*})\).
-
\(\textsf {Setup} \): \(\hat{\mathcal {C}}_{2}\) runs \(\textsf {Setup} (1^{n},N)\) to obtain \((\textsf {msk} ,\textsf {muk} ,\textsf {pp} ,\textsf {RL} , \textsf {st} )\). Note: RL is initially empty. \(\hat{\mathcal {C}}_{2}\) keeps \(\textsf {msk} \) in secret by himself and provides \((\textsf {pp} ,\textsf {muk} )\) to \(\mathcal {A}_{2}\).
-
 : \(\mathcal {A}_{2}\) adaptively makes a polynomially bounded number of queries on the following oracles (Note: all oracles share the \(\textsf {st} \) and the queries also should be with some restrictions defined later):
: \(\mathcal {A}_{2}\) adaptively makes a polynomially bounded number of queries on the following oracles (Note: all oracles share the \(\textsf {st} \) and the queries also should be with some restrictions defined later):-
\(\textsf {PriKenGen} (\cdot )\): For the private key query on an identity \(\textsf {id} \in \mathcal {I}\), it returns a long-term private key \(\textsf {sk} _{\textsf {id} }\) and an outsourcing key \(\textsf {ok} _{\textsf {id} }\) by running \(\textsf {PriKeyGen} (\textsf {msk} ,\textsf {id} ,\textsf {st} )\).
-
\(\textsf {Revoke} (\cdot )\): For the revocation query on \((\textsf {id} ,\textsf {t} )\in \mathcal {I}\times \mathcal {T}\), it returns an updated \(\textsf {RL} '\) by running \(\textsf {Revoke} (\textsf {id} , \textsf {t} ,\textsf {RL} , \textsf {st} )\).
-
\(\textsf {DecKeyGen} (\cdot )\): For the decryption key query on \((\textsf {id} ,\textsf {t} )\in \mathcal {I}\times \mathcal {T}\), it returns a short-term decryption key \(\textsf {dk} _{\textsf {id} ,\textsf {t} }\) by running \(\textsf {DecKeyGen} (\textsf {sk} _{\textsf {id} }, \textsf {uk} _{\textsf {id} ,\textsf {t} })\). Note: similarly, this oracle is also used to define DKER, which is not provided by Dong et al.
-
-
\(\textsf {Challenge} \): \(\mathcal {A}_{2}\) submits a message \(\textsf {m} ^{*}\in \mathcal {M}\). \(\hat{\mathcal {C}}_{1}\) samples a bit
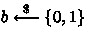 . If \(b=0\), \(\hat{\mathcal {C}}_{1}\) returns a challenge ciphertext \(\textsf {ct} ^{*}_{\textsf {id} ^{*},\textsf {t} ^{*}}\) by running \(\textsf {Encrypt} (\textsf {id} ^{*},\textsf {t} ^{*},\textsf {m} ^{*})\), otherwise, a random
. If \(b=0\), \(\hat{\mathcal {C}}_{1}\) returns a challenge ciphertext \(\textsf {ct} ^{*}_{\textsf {id} ^{*},\textsf {t} ^{*}}\) by running \(\textsf {Encrypt} (\textsf {id} ^{*},\textsf {t} ^{*},\textsf {m} ^{*})\), otherwise, a random
 .
. -
 : \(\mathcal {A}_{2}\) can continue to make additional queries as before with the same restrictions.
: \(\mathcal {A}_{2}\) can continue to make additional queries as before with the same restrictions. -
\(\textsf {Guess} \): \(\mathcal {A}_{2}\) outputs a bit \(b^{*}\in \{0,1\}\), and wins if \(b^{*}=b\).
In the above game, the following restrictions must hold:
-
\(\textsf {Revoke}(\cdot )\) can only be queried in a non-decreasing order of time (i.e., at time that is greater than or equal to the time of all previous queries).
-
\(\textsf {PriKenGen}(\cdot )\) can be queried on identity \(\textsf {id}^{*}\) while only the outsourcing key \(\textsf {ok}^{*}_{\textsf {id}^{*}}\) is returned.
-
\(\textsf {DecKeyGen}(\cdot )\) can not be queried on \((\textsf {id}^{*},\textsf {t}^{*})\).
The advantage of \(\mathcal {A}_{2}\) in the above game is defined as  . An OR-IBE scheme is ind-uka secure if for all ppt adversary \(\mathcal {A}_{2}\),
. An OR-IBE scheme is ind-uka secure if for all ppt adversary \(\mathcal {A}_{2}\),  is negligible in the security parameter n.
is negligible in the security parameter n.
B Correctness and Security
Correctness: If the above scheme is operated correctly as specified, and the recipient \(\textsf {id}\in \mathcal {I}\) is not revoked at time \(\textsf {t}\in \mathcal {T}\), then \(\textsf {dk}_{\textsf {id},\textsf {t}}=(\mathbf {E}_{0},\mathbf {E}_{1,\theta },\mathbf {E}_{2,\theta })\) satisfies that \(\mathbf {A}'_{\textsf {id}}\cdot \mathbf {E}_{0}=\mathbf {U}\ \mathrm {mod} \ q\), and \(\mathbf {A}_{\textsf {id}}\cdot \mathbf {E}_{1,\theta }+\mathbf {B}_{\textsf {t}}\cdot \mathbf {E}_{2,\theta }=\mathbf {U}\ \mathrm {mod} \ q\).
In the decryption algorithm, the non-revoked \(\textsf {id}\) first tries to derive \(\textsf {m}_{0}\) by using \((\mathbf {E}_{1,\theta },\mathbf {E}_{2,\theta })\):
According to our parameters settings, it can be checked that the error term \(\textsf {error}'\) is bounded by q/5 (i.e., \(\Vert \textsf {error}'\Vert _{\infty }<q/5\)), thus, we have the conclusion \(\lfloor \frac{2}{q}\mathbf {w}_{0}\rceil =\textsf {m}_{0}\) with overwhelming probability.
The non-revoked \(\textsf {id}\) then tries to derive \(\textsf {m}_{1}\) by using \(\mathbf {E}_{0}\):
Similarly, according to our parameters settings, it can be checked that the error term \(\textsf {error}''\) is bounded by q/5 (i.e., \(\Vert \textsf {error}''\Vert _{\infty }<q/5\)), thus, we have the conclusion \(\lfloor \frac{2}{q}\mathbf {w}_{1}\rceil =\textsf {m}_{1}\) with overwhelming probability.
Thus, the decryption can be successful and recovers the message \(\lfloor \frac{2}{q}\mathbf {w}_{0}\rceil \oplus \lfloor \frac{2}{q}\mathbf {w}_{1}\rceil =\textsf {m}_{0}\oplus \textsf {m}_{1}=\textsf {m}\) with overwhelming probability.
ind-cpa: For the ind-cpa security, we show the following theorem.
Theorem 3
The modified lattice-based OR-IBE is ind-cpa secure if the \(\textsf {LWE} _{n,q,\chi }\) assumption holds.
Proof. To proof this theorem, we define a list of games where the first one is identical to the original ind-cpa game as in Definition 2 and show that a ppt adversary \(\mathcal {A}_{1}\) has advantage zero in the last game. We show that \(\mathcal {A}_{1}\) cannot distinguish between these games, and thus \(\mathcal {A}_{1}\) has negligible advantage in winning the original ind-cpa game.
Let \(\textsf {id}^{*}\) be a challenge identity and \(\textsf {t}^{*}\) be a challenge time, we consider two types of adversaries:
-
Type-0: \(\mathcal {A}_{1}\) requests a long-term private key on the challenge identity \(\textsf {id}^{*}\). In this case, \(\textsf {id}^{*}\) must be revoked at time \(\textsf {t}\le \textsf {t}^{*}\).
-
Type-1: \(\mathcal {A}_{1}\) only requests a long-term private key on the identity \(\textsf {id}\ne \textsf {id}^{*}\). In this case, \(\mathcal {A}_{1}\) may request a short-term decryption key on \((\textsf {id}^{*},\textsf {t})\) where \(\textsf {t}\ne \textsf {t}^{*}\).
ind-uka: For the ind-uka security, we show the following theorem.
Theorem 4
The modified lattice-based OR-IBE is ind-uka secure if the \(\textsf {LWE} _{n,q,\chi }\) assumption holds.
Proof. The proof almost enjoys the same description as that of Theorem 3, and we will show the different details later. To proof this theorem, we also define a list of games where the first one is identical to the original ind-uka game as in Definition 3 and show that a ppt adversary \(\mathcal {A}_{2}\) has advantage zero in the last game. We show that \(\mathcal {A}_{2}\) cannot distinguish between these games, and thus \(\mathcal {A}_{2}\) has a negligible advantage in winning the original ind-uka game.
Because the KU-CSP can issue an arbitrary time update key by using the master update key muk and the outsourcing key \(\textsf {ok}_{\textsf {id}}\), a direct restriction is that KU-CSP cannot request a long-term private key for the challenge identity \(\textsf {id}^{*}\), thus, the Type-0 adversary in the proof of Theorem 3 is not considered and only a Type-1 adversary exists.
Due to the limited space, we omit the detailed proofs of Theorems 3 and 4, if any necessary, please contact the corresponding author for the full version.
Rights and permissions
Copyright information
© 2021 Springer Nature Switzerland AG
About this paper
Cite this paper
Zhang, Y., Liu, X., Hu, Y., Jia, H. (2021). On the Analysis of the Outsourced Revocable Identity-Based Encryption from Lattices. In: Yang, M., Chen, C., Liu, Y. (eds) Network and System Security. NSS 2021. Lecture Notes in Computer Science(), vol 13041. Springer, Cham. https://doi.org/10.1007/978-3-030-92708-0_5
Download citation
DOI: https://doi.org/10.1007/978-3-030-92708-0_5
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-92707-3
Online ISBN: 978-3-030-92708-0
eBook Packages: Computer ScienceComputer Science (R0)


 :
: 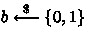 . If
. If  .
. :
: