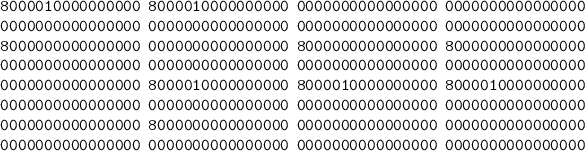Abstract
Since Wang’s attacks on the standard hash functions MD5 and SHA-1, design and analysis of hash functions have been studied a lot. NIST selected Keccak as a new hash function standard SHA-3 in 2012 and announced that Keccak was chosen because its design is different from MD5 and SHA-1/2 so that it could be secure against the attacks to them and Keccak ’s hardware efficiency is quite better than other SHA-3 competition candidates. However, software efficiency of Keccak is somewhat worse than present standards and other candidates. Since software efficiency becomes more important due to increase of kinds and volume of communication/storage data as cloud and big data service spread widely, its software efficiency degradation is not desirable.
In this paper, we present a new fast hash function family LSH, whose software efficiency is above four times faster than SHA-3, and 1.5–2.3 times faster than other SHA-3 finalists. Moreover it is secure against all critical hash function attacks.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
References
ehash webpage - sha-3 hardware implementations. http://ehash.iaik.tugraz.at/wiki/SHA-3_Hardware_Implementations
Intel intrinsics guide. http://software.intel.com/sites/landingpage/IntrinsicsGuide
Measurements of sha-3 finalists, indexed by machine. http://bench.cr.yp.to/results-sha3.html
Neon. http://www.arm.com/products/processors/technologies/neon.php
Rcis webpage (other asic implementations). http://staff.aist.go.jp/akashi.satoh/SASEBO/en/sha3/others.html
x86, x64 instruction latency, memory latency and cpuid dumps. http://instlatx64.atw.hu
Amd64 architecture programmer’s manual volume 6: 128-bit and 256-bit xop, fma4 and cvt16 instructions. Technical report, May 2009
Sha-3 standard: Permutation-based hash and extendable-output functions, May 2014
Akin, A., Aysu, A., Ulusel, O.C., Savaş, E.: Efficient hardware implementations of high throughput sha-3 candidates keccak, luffa and blue midnight wish for single- and multi-message hashing. In: Proceedings of the 3rd International Conference on Security of Information and Networks, SIN 2010, pp. 168–177. ACM, New York (2010)
Aoki, K., Sasaki, Y.: Meet-in-the-middle preimage attacks against reduced SHA-0 and SHA-1. In: Halevi, S. (ed.) CRYPTO 2009. LNCS, vol. 5677, pp. 70–89. Springer, Heidelberg (2009)
Aumasson, J.-P., Henzen, L., Meier, W., Phan, R.C.-W.: Sha-3 proposal blake. Submission to NIST (Round 3) (2010)
Barker, E.B., Barker, W.C., Lee, A.: Guideline for implementing cryptography in the federal government (2005)
Bernstein, D.J.: Second preimages for 6 (7? (8??)) rounds of keccak? NIST mailing list (2010)
Biham, E., Biryukov, A., Shamir, A.: Cryptanalysis of skipjack reduced to 31 rounds using impossible differentials. In: Stern, J. (ed.) EUROCRYPT 1999. LNCS, vol. 1592, pp. 12–23. Springer, Heidelberg (1999)
Biham, E., Dunkelman, O., Keller, N.: Enhancing differential-linear cryptanalysis. In: Zheng, Y. (ed.) ASIACRYPT 2002. LNCS, vol. 2501, pp. 254–266. Springer, Heidelberg (2002)
Biham, E., Shamir, A.: Differential Cryptanalysis of the Data Encryption Standard. Springer, London (1993)
Biryukov, A., Khovratovich, D.: Related-key cryptanalysis of the full AES-192 and AES-256. In: Matsui, M. (ed.) ASIACRYPT 2009. LNCS, vol. 5912, pp. 1–18. Springer, Heidelberg (2009)
Black, J.A., Rogaway, P., Shrimpton, T.: Black-box analysis of the block-cipher-based hash-function constructions from PGV. In: Yung, M. (ed.) CRYPTO 2002. LNCS, vol. 2442, pp. 320–335. Springer, Heidelberg (2002)
Bogdanov, A., Khovratovich, D., Rechberger, C.: Biclique cryptanalysis of the full AES. In: Lee, D.H., Wang, X. (eds.) ASIACRYPT 2011. LNCS, vol. 7073, pp. 344–371. Springer, Heidelberg (2011)
Bogdanov, A., Wang, M.: Zero correlation linear cryptanalysis with reduced data complexity. In: Canteaut, A. (ed.) FSE 2012. LNCS, vol. 7549, pp. 29–48. Springer, Heidelberg (2012)
Canteaut, A., Chabaud, F.: A new algorithm for finding minimum-weight words in a linear code: application to mceliece’s cryptosystem and to narrow-sense bch codes of length 511. IEEE Trans. Inform. Theory 44(1), 367–378 (1998)
Chang, D., Nandi, M.: Improved indifferentiability security analysis of chopMD hash function. In: Nyberg, K. (ed.) FSE 2008. LNCS, vol. 5086, pp. 429–443. Springer, Heidelberg (2008)
Dunkelman, O., Keller, N., Shamir, A.: A practical-time related-key attack on the kasumi cryptosystem used in GSM and 3G telephony. J. Cryptology, 1–26 (2013)
Duo, L., Li, C.: Improved collision and preimage resistance bounds on pgv schemes. Cryptology ePrint Archive, Report 2006/462 (2006). http://eprint.iacr.org/
Ferguson, N., Lucks, S., Schneier, B., Whiting, D., Bellare, M., Kohno, T., Callas, J., Walker, J.: The skein hash function family. Submission to NIST (Round 3) (2010)
Muheim, B., Homsirikamol, E., Keller, C., Rogawski, M., Kaeslin, H., Kaps, J., Gürkaynak, G., Gaj, K.: Lessons learned from designing a 65nm asic for evaluating third round sha-3 candidates. In: Third SHA-3 Candidates Conference (2012). http://csrc.nist/gov/groups/ST/hash/sha-3/Round3/March2012/documents/papers/GURKAYNAK_paper.pdf
Gauravaram, P., Knudsen, L.R., Matusiewicz, K., Mendel, F., Rechberger, C., Schlffer, M., Thomsen, S.S.: Grøstl - a sha-3 candidate. Submission to NIST (Round 3) (2011)
Guo, J., Karpman, P., Nikolic, I., Wang, L., Wu, S.: Analysis of blake2. Cryptology ePrint Archive, Report 2013/467 (2013). http://eprint.iacr.org/
Henzen, L., Aumasson, J.-P., Meier, W., Phan, R.C.-W.: Vlsi characterization of the cryptographic hash function blake. IEEE Trans. Very Large Scale Integration (VLSI) Syst. 19(10), 1746–1754 (2011)
Hermelin, M., Nyberg, K.: Multidimensional linear distinguishing attacks and boolean functions. Crypt. Commun. 4(1), 47–64 (2012)
Intel. Intel architecture instruction set extensions programming reference. 319433–018, February 2014
Mathew, S.K., Walker, J., Sheikh, F., Krishnamurthy, R.: A skein-512 hardware implementation. In: Second SHA-3 Candidate Conference (2010). http://csrc.nist/gov/groups/ST/hash/sha-3/Round2/Aug2010/documents/papers/WALKER_skein-intel-hwd.pdf/
Kelsey, J., Schneier, B.: Second preimages on n-bit hash functions for much less than 2\(^{n}\) Work. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 474–490. Springer, Heidelberg (2005)
Khovratovich, D., Nikolić, I.: Rotational cryptanalysis of ARX. In: Hong, S., Iwata, T. (eds.) FSE 2010. LNCS, vol. 6147, pp. 333–346. Springer, Heidelberg (2010)
Khovratovich, D., Nikolić, I., Rechberger, C.: Rotational rebound attacks on reduced skein. In: Abe, M. (ed.) ASIACRYPT 2010. LNCS, vol. 6477, pp. 1–19. Springer, Heidelberg (2010)
Khovratovich, D., Rechberger, C., Savelieva, A.: Bicliques for preimages: attacks on Skein-512 and the SHA-2 family. In: Canteaut, A. (ed.) FSE 2012. LNCS, vol. 7549, pp. 244–263. Springer, Heidelberg (2012)
Knellwolf, S., Khovratovich, D.: New preimage attacks against reduced SHA-1. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 367–383. Springer, Heidelberg (2012)
Knudsen, L.R.: Truncated and higher order differentials. In: Preneel, B. (ed.) FSE 1994. LNCS, vol. 1008, pp. 196–211. Springer, Heidelberg (1995)
Knudsen, L.R., Wagner, D.: Integral cryptanalysis. In: Daemen, J., Rijmen, V. (eds.) FSE 2002. LNCS, vol. 2365, pp. 112–127. Springer, Heidelberg (2002)
Leurent, G.: Analysis of differential attacks in ARX constructions. In: Wang, X., Sako, K. (eds.) ASIACRYPT 2012. LNCS, vol. 7658, pp. 226–243. Springer, Heidelberg (2012)
Leurent, G.: Construction of differential characteristics in ARX designs application to skein. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013, Part I. LNCS, vol. 8042, pp. 241–258. Springer, Heidelberg (2013)
Lipmaa, H., Moriai, S.: Efficient algorithms for computing differential properties of addition. In: Matsui, M. (ed.) FSE 2001. LNCS, vol. 2355, pp. 336–350. Springer, Heidelberg (2002)
Luo, Y., Gong, Z., Duan, M., Zhu, B., Lai, X.: Revisiting the indifferentiability of pgv hash functions. Cryptology ePrint Archive, Report 2009/265 (2009). http://eprint.iacr.org/
Matsui, M.: Linear cryptanalysis method for DES cipher. In: Helleseth, T. (ed.) EUROCRYPT 1993. LNCS, vol. 765, pp. 386–397. Springer, Heidelberg (1994)
Mendel, F., Rechberger, C., Schläffer, M., Thomsen, S.S.: The rebound attack: cryptanalysis of reduced whirlpool and Grøstl. In: Dunkelman, O. (ed.) FSE 2009. LNCS, vol. 5665, pp. 260–276. Springer, Heidelberg (2009)
Menezes, A.J., Vanstone, S.A., Van Oorschot, P.C.: Handbook of Applied Cryptography, 1st edn. CRC Press Inc., Boca Raton (1996)
Mouha, N., Preneel, B.: Towards finding optimal differential characteristics for arx: application to salsa20. Cryptology ePrint Archive, Report 2013/328 (2013). http://eprint.iacr.org/
Nad, T.: The codingtool library (2010). Presentation
Rogaway, P., Shrimpton, T.: Cryptographic hash-function basics: definitions, implications, and separations for preimage resistance, second-preimage resistance, and collision resistance. In: Roy, B., Meier, W. (eds.) FSE 2004. LNCS, vol. 3017, pp. 371–388. Springer, Heidelberg (2004)
Sasaki, Y., Aoki, K.: Finding preimages in full MD5 faster than exhaustive search. In: Joux, A. (ed.) EUROCRYPT 2009. LNCS, vol. 5479, pp. 134–152. Springer, Heidelberg (2009)
Shimpi, A.L.: The iphone 5s. review, 17 September 2013. http://www.anandtech.com/show/7335/the-iphone-5s-review/4
Tillich, S.: Hardware implementation of the sha-3 candidate skein. Cryptology ePrint Archive, Report 2009/159 (2009). http://eprint.iacr.org/
Wagner, D.: The boomerang attack. In: Knudsen, L.R. (ed.) FSE 1999. LNCS, vol. 1636, pp. 156–170. Springer, Heidelberg (1999)
Wang, X., Yin, Y.L., Yu, H.: Finding collisions in the full SHA-1. In: Shoup, V. (ed.) CRYPTO 2005. LNCS, vol. 3621, pp. 17–36. Springer, Heidelberg (2005)
Wang, X., Yu, H.: How to break MD5 and other hash functions. In: Cramer, R. (ed.) EUROCRYPT 2005. LNCS, vol. 3494, pp. 19–35. Springer, Heidelberg (2005)
Nazhandali, L., Guo, X., Huang, S., Schaumont, P.: Fair and comprehensive performance evaluation of 14 second round sha-3 asic implementations. In: Second SHA-3 Candidate Conference (2010). http://csrc.nist/gov/groups/ST/hash/sha-3/Round2/Aug2010/documents/papers/SCHAUMONT_SHA3.pdf
Acknowledgements
We would like to thank research members in Pusan National University and COSIC, KU Leuven including Howon Kim, Donggeon Lee, Vincent Rijmen, and Nicky Mouha for helpful discussion on security and efficiency of hash function designs.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
A Differential Characteristics for Collision Attack
A Differential Characteristics for Collision Attack
LSH-256-256. The best 12-step differential characteristic with probability \(2^{-1340}\) (\(2^{-1317}\) in step functions, \(2^{-23}\) in message expansion) is as follows: Note that this characteristic starts from the step function \(\textsc {Step} _1\).
-
Difference of a chaining variable: \(\varDelta \mathsf T \)

-
Difference of sub-messages: \(\varDelta \mathsf M _1||\varDelta \mathsf M _2\)

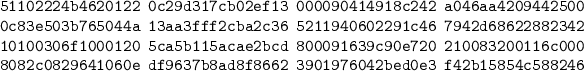
LSH-512-512. The best 13-step differential characteristic with probability \(2^{-2562}\) (\(2^{-2535}\) in step functions, \(2^{-27}\) in message expansion) is as follows: Note that this characteristic starts from the step function \(\textsc {Step} _1\).
-
Difference of a chaining variable: \(\varDelta \mathsf T \)
-
Difference of sub-messages: \(\varDelta \mathsf M _1||\varDelta \mathsf M _2\)
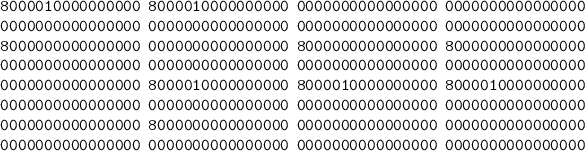
Rights and permissions
Copyright information
© 2015 Springer International Publishing Switzerland
About this paper
Cite this paper
Kim, DC., Hong, D., Lee, JK., Kim, WH., Kwon, D. (2015). LSH: A New Fast Secure Hash Function Family. In: Lee, J., Kim, J. (eds) Information Security and Cryptology - ICISC 2014. ICISC 2014. Lecture Notes in Computer Science(), vol 8949. Springer, Cham. https://doi.org/10.1007/978-3-319-15943-0_18
Download citation
DOI: https://doi.org/10.1007/978-3-319-15943-0_18
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-15942-3
Online ISBN: 978-3-319-15943-0
eBook Packages: Computer ScienceComputer Science (R0)