Abstract
In (TCC 2017), Hofheinz, Hövelmanns and Kiltz provided a fine-grained and modular toolkit of generic key encapsulation mechanism (KEM) constructions, which were widely used among KEM submissions to NIST Post-Quantum Cryptography Standardization project. The security of these generic constructions in the quantum random oracle model (QROM) has been analyzed by Hofheinz, Hövelmanns and Kiltz (TCC 2017), Saito, Xagawa and Yamakawa (Eurocrypt 2018), and Jiang et al. (Crypto 2018). However, the security proofs from standard assumptions are far from tight. In particular, the factor of security loss is q and the degree of security loss is 2, where q is the total number of adversarial queries to various oracles.
In this paper, using semi-classical oracle technique recently introduced by Ambainis, Hamburg and Unruh (ePrint 2018/904), we improve the results in (Eurocrypt 2018, Crypto 2018) and provide tighter security proofs for generic KEM constructions from standard assumptions. More precisely, the factor of security loss q is reduced to be \(\sqrt{q}\). In addition, for transformation T that turns a probabilistic public-key encryption (PKE) into a determined one by derandomization and re-encryption, the degree of security loss 2 is reduced to be 1. Our tighter security proofs can give more confidence to NIST KEM submissions where these generic transformations are used, e.g., CRYSTALS-Kyber etc.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
The message m here is picked at random from the message space of underlying PKE.
- 2.
When comparing the tightness of different reductions, we assume perfect correctness of underlying scheme for brevity.
- 3.
Here, for TPunc and KC, we just follow [10] and assume the perfect correctness of underlying PKE.
- 4.
Although \({H}_q\) here is the whole truth table of \({H}_q\), it is just taken as an oracle to make queries (with at most \(q_H\) times) in algorithm A. Thus, we can also take \({H}_q\) as an accessible oracle instead of a whole truth table.
- 5.
For a classical query input \(m^*\), \(\mathcal {O}_{m^*}^{{SC}}\) always outputs 1.
References
Rackoff, C., Simon, D.R.: Non-interactive zero-knowledge proof of knowledge and chosen ciphertext attack. In: Feigenbaum, J. (ed.) CRYPTO 1991. LNCS, vol. 576, pp. 433–444. Springer, Heidelberg (1992). https://doi.org/10.1007/3-540-46766-1_35
Bellare, M., Rogaway, P.: Random oracles are practical: a paradigm for designing efficient protocols. In: Denning, D.E., Pyle, R., Ganesan, R., Sandhu, R.S., Ashby, V. (eds.) Proceedings of the 1st ACM Conference on Computer and Communications Security, CCS 1993, pp. 62–73. ACM (1993)
Dent, A.W.: A designer’s guide to KEMs. In: Paterson, K.G. (ed.) Cryptography and Coding 2003. LNCS, vol. 2898, pp. 133–151. Springer, Heidelberg (2003). https://doi.org/10.1007/978-3-540-40974-8_12
Hofheinz, D., Hövelmanns, K., Kiltz, E.: A modular analysis of the Fujisaki-Okamoto transformation. In: Kalai, Y., Reyzin, L. (eds.) TCC 2017. LNCS, vol. 10677, pp. 341–371. Springer, Cham (2017). https://doi.org/10.1007/978-3-319-70500-2_12
Fujisaki, E., Okamoto, T.: Secure integration of asymmetric and symmetric encryption schemes. In: Wiener, M. (ed.) CRYPTO 1999. LNCS, vol. 1666, pp. 537–554. Springer, Heidelberg (1999). https://doi.org/10.1007/3-540-48405-1_34
Fujisaki, E., Okamoto, T.: Secure integration of asymmetric and symmetric encryption schemes. J. Cryptol. 26(1), 1–22 (2013)
Targhi, E.E., Unruh, D.: Post-quantum security of the Fujisaki-Okamoto and OAEP transforms. In: Hirt, M., Smith, A. (eds.) TCC 2016. LNCS, vol. 9986, pp. 192–216. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-53644-5_8
Okamoto, T., Pointcheval, D.: REACT: rapid enhanced-security asymmetric cryptosystem transform. In: Naccache, D. (ed.) CT-RSA 2001. LNCS, vol. 2020, pp. 159–174. Springer, Heidelberg (2000). https://doi.org/10.1007/3-540-45353-9_13
Jean-Sébastien, C., Handschuh, H., Joye, M., Paillier, P., Pointcheval, D., Tymen, C.: GEM: a generic chosen-ciphertext secure encryption method. In: Preneel, B. (ed.) CT-RSA 2002. LNCS, vol. 2271, pp. 263–276. Springer, Heidelberg (2002). https://doi.org/10.1007/3-540-45760-7_18
Saito, T., Xagawa, K., Yamakawa, T.: Tightly-secure key-encapsulation mechanism in the quantum random oracle model. In: Nielsen, J.B., Rijmen, V. (eds.) EUROCRYPT 2018. LNCS, vol. 10822, pp. 520–551. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-78372-7_17
Jiang, H., Zhang, Z., Chen, L., Wang, H., Ma, Z.: IND-CCA-secure key encapsulation mechanism in the quantum random oracle model, revisited. In: Shacham, H., Boldyreva, A. (eds.) CRYPTO 2018. LNCS, vol. 10993, pp. 96–125. Springer, Cham (2018). https://doi.org/10.1007/978-3-319-96878-0_4. https://eprint.iacr.org/2017/1096
Bernstein, D.J., Persichetti, E.: Towards KEM unification. Cryptology ePrint Archive, Report 2018/526 (2018). https://eprint.iacr.org/2018/526
Szepieniec, A., Reyhanitabar, R., Preneel, B.: Key encapsulation from noisy key agreement in the quantum random oracle model. Cryptology ePrint Archive, Report 2018/884 (2018). https://eprint.iacr.org/2018/884
Hövelmanns, K., Kiltz, E., Schäge, S., Unruh, D.: Generic authenticated key exchange in the quantum random oracle model. Cryptology ePrint Archive, Report 2018/928 (2018). https://eprint.iacr.org/2018/928
Xagawa, K., Yamakawa, T.: (Tightly) QCCA-secure key-encapsulation mechanism in the quantum random oracle model. Cryptology ePrint Archive, Report 2018/838 (2018). https://eprint.iacr.org/2018/838
NIST: National institute for standards and technology. Post quantum crypto project (2017). https://csrc.nist.gov/projects/post-quantum-cryptography/round-1-submissions
Boneh, D., Dagdelen, Ö., Fischlin, M., Lehmann, A., Schaffner, C., Zhandry, M.: Random oracles in a quantum world. In: Lee, D.H., Wang, X. (eds.) ASIACRYPT 2011. LNCS, vol. 7073, pp. 41–69. Springer, Heidelberg (2011). https://doi.org/10.1007/978-3-642-25385-0_3
Menezes, A.: Another look at provable security (2012). Invited Talk at EUROCRYPT 2012: https://www.iacr.org/cryptodb/archive/2012/EUROCRYPT/presentation/24260.pdf
Ducas, L., Stehlé, D.: Assessing the security of lattice-based submissions: the 10 questions that NIST should be asking the community (2018). http://prometheuscrypt.gforge.inria.fr/2018-06-04.assessing-security.html
Ambainis, A., Hamburg, M., Unruh, D.: Quantum security proofs using semi-classical oracles. Cryptology ePrint Archive, Report 2018/904 (2018). https://eprint.iacr.org/2018/904
Unruh, D.: Revocable quantum timed-release encryption. J. ACM 62(6), 49:1–49:76 (2015)
Zhandry, M.: Secure identity-based encryption in the quantum random oracle model. In: Safavi-Naini, R., Canetti, R. (eds.) CRYPTO 2012. LNCS, vol. 7417, pp. 758–775. Springer, Heidelberg (2012). https://doi.org/10.1007/978-3-642-32009-5_44
Ambainis, A., Rosmanis, A., Unruh, D.: Quantum attacks on classical proof systems: the hardness of quantum rewinding. In: 55th IEEE Annual Symposium on Foundations of Computer Science, FOCS 2014, pp. 474–483. IEEE (2014)
Hülsing, A., Rijneveld, J., Song, F.: Mitigating multi-target attacks in hash-based signatures. In: Cheng, C.-M., Chung, K.-M., Persiano, G., Yang, B.-Y. (eds.) PKC 2016. LNCS, vol. 9614, pp. 387–416. Springer, Heidelberg (2016). https://doi.org/10.1007/978-3-662-49384-7_15
Bellare, M., Boldyreva, A., O’Neill, A.: Deterministic and efficiently searchable encryption. In: Menezes, A. (ed.) CRYPTO 2007. LNCS, vol. 4622, pp. 535–552. Springer, Heidelberg (2007). https://doi.org/10.1007/978-3-540-74143-5_30
Bellare, M., Halevi, S., Sahai, A., Vadhan, S.: Many-to-one trapdoor functions and their relation to public-key cryptosystems. In: Krawczyk, H. (ed.) CRYPTO 1998. LNCS, vol. 1462, pp. 283–298. Springer, Heidelberg (1998). https://doi.org/10.1007/BFb0055735
Acknowledgements
We would like to thank Rainer Steinwandt, Fang Song, and anonymous reviewers of PQCrypto 2019 for their comments and suggestions. We are also grateful to Dominique Unruh for helpful discussions on the one way to hiding lemma. This work is supported by the National Key Research and Development Program of China (No. 2017YFB0802000), the National Natural Science Foundation of China (No. U1536205, 61472446, 61701539), and the National Cryptography Development Fund (mmjj20180107, mmjj20180212).
Author information
Authors and Affiliations
Corresponding authors
Editor information
Editors and Affiliations
Appendices
A Cryptographic Primitives
Definition 1
(Public-key encryption). A public-key encryption scheme \(\mathrm {PKE}\) consists of three algorithms. The key generation algorithm, Gen, is a probabilistic algorithm which on input \(1^{\lambda }\) outputs a public/secret key-pair (pk, sk). The encryption algorithm Enc, on input pk and a message \(m \in \mathcal {M}\), outputs a ciphertext \(c\leftarrow Enc(pk,m)\). If necessary, we make the used randomness of encryption explicit by writing \(c:=Enc(pk,m;r)\), where \(r \overset{\$}{\leftarrow } \mathcal {R}\) (\(\mathcal {R}\) is the randomness space). The decryption algorithm Dec, is a deterministic algorithm which on input sk and a ciphertext c outputs a message \(m:=Dec({sk},c)\) or a rejection symbol \(\perp \notin \mathcal {M}\). A PKE is determined if Enc is deterministic. We denote \(\mathrm {DPKE}\) to stand for a determined PKE.
Definition 2
(Correctness [4]). A public-key encryption scheme \(\mathrm {PKE}\) is \(\delta \)-correct if \(E[\mathop {\mathrm {max}}\limits _{m\in \mathcal {M}}\Pr [Dec(sk,c)\ne m : c \leftarrow Enc(pk,m)]]\le \delta ,\) where the expectation is taken over \((pk,sk) \leftarrow Gen\). A PKE is perfectly correct if \(\delta =0\).
Definition 3
(DS-secure DPKE [10]). Let \(D_\mathcal {M}\) denote an efficiently sampleable distribution on a set \(\mathcal {M}\). A DPKE scheme (Gen,Enc,Dec) with plaintext and ciphertext spaces \(\mathcal {M}\) and \(\mathcal {C}\) is \(D_\mathcal {M}\)-disjoint simulatable if there exists a PPT algorithm S that satisfies the following,
-
(1)
Statistical disjointness:
$$\begin{aligned} {\textsc {Disj}}_{\mathrm {PKE},S}:=\mathop {\max }\limits _{(pk,sk)\in Gen(1^\lambda ;\mathcal {R}_{gen})} \Pr [c\in Enc(pk,\mathcal {M}): c \leftarrow S(pk)] \end{aligned}$$is negligible, where \(\mathcal {R}_{gen}\) denotes a randomness space for Gen.
-
(2)
Ciphertext indistinguishability: For any PPT adversary
 ,
, 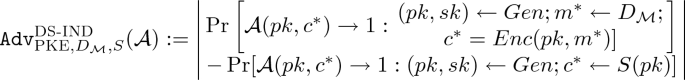
is negligible.
Games OW-ATK (ATK \(\in \) {CPA, VA, qPCA, qPVCA}) for PKE, where \(O_{\mathrm {ATK}}\) is defined in Definition 4. In games qPCA and qPVCA, the adversary  can query the \(\textsc {Pco}\) oracle with quantum state.
can query the \(\textsc {Pco}\) oracle with quantum state.
Definition 4
(OW-ATK-secure PKE). Let \(\mathrm {PKE}=(Gen, Enc, Dec)\) be a public-key encryption scheme with message space \(\mathcal {M}\). For \(\mathrm {ATK} \in \{\mathrm {CPA,VA,}\) \(\mathrm {qPCA,qPVCA}\}\) [11], we define \(\text{ OW-ATK }\) games as in Fig. 6, where

Define the OW-ATK advantage function of an adversary  against PKE as
against PKE as
 .
.
Definition 5
(IND-CPA-secure PKE). Define \(\mathrm {IND-CPA}\) game of PKE as in Fig. 7 and the \(\mathrm {IND-CPA}\) advantage function of an adversary  against PKE as
against PKE as
 .
.
Definition 6
(Key encapsulation). A key encapsulation mechanism KEM consists of three algorithms. The key generation algorithm Gen outputs a key pair (pk, sk). The encapsulation algorithm Encaps, on input pk, outputs a tuple (K, c), where \(K \in \mathcal {K}\) and c is said to be an encapsulation of the key K. The deterministic decapsulation algorithm Decaps, on input sk and an encapsulation c, outputs either a key \(K := Decaps(sk, c) \in \mathcal {K}\) or a rejection symbol \(\perp \notin \mathcal {K}\).
Definition 7
(IND-CCA-secure KEM). We define the \(\mathrm {IND-CCA}\) game as in Fig. 7 and the \(\mathrm {IND-CCA}\) advantage function of an adversary  against \(\mathrm {KEM}\) as
against \(\mathrm {KEM}\) as
 .
.
B Proof of Theorem 2
Proof
Let  be an adversary against the OW-qPCA security of PKE\('\), issuing at most \(q_{PC}\) queries to the oracle PCO, at most \(q_G\) queries to the random oracle \(G\). Denote \(\varOmega _G\) as the sets of all functions \(G:\mathcal {M} \rightarrow \mathcal {R}\). Let \(G'\) be a random function such that \(G'(m)\) is sampled according to the uniform distribution in \(\mathcal {R}_{\mathrm {good}}(pk,sk,m)\), where \(\mathcal {R}_{\mathrm {good}}(pk,sk,m):=\{{r \in \mathcal {R}}: Dec(sk,Enc(pk,m;r))= m\}\). Let \(\varOmega _{G'}\) be the set of all functions \(G'\). Let
be an adversary against the OW-qPCA security of PKE\('\), issuing at most \(q_{PC}\) queries to the oracle PCO, at most \(q_G\) queries to the random oracle \(G\). Denote \(\varOmega _G\) as the sets of all functions \(G:\mathcal {M} \rightarrow \mathcal {R}\). Let \(G'\) be a random function such that \(G'(m)\) is sampled according to the uniform distribution in \(\mathcal {R}_{\mathrm {good}}(pk,sk,m)\), where \(\mathcal {R}_{\mathrm {good}}(pk,sk,m):=\{{r \in \mathcal {R}}: Dec(sk,Enc(pk,m;r))= m\}\). Let \(\varOmega _{G'}\) be the set of all functions \(G'\). Let  as the fraction of bad randomness, where \(\mathcal {R}_{\mathrm {bad}}(pk,sk,m)=\mathcal {R}\setminus \mathcal {R}_{\mathrm {good}}(pk,sk,m)\). \(\delta (pk,sk)=\max _{m\in {\mathcal {M}}}\delta (pk,sk,m)\). \(\delta =\mathbf {E}[\delta (pk,sk)]\), where the expectation is taken over \((pk,sk) {\leftarrow }Gen\). Consider the games in Figs. 8 and 9.
as the fraction of bad randomness, where \(\mathcal {R}_{\mathrm {bad}}(pk,sk,m)=\mathcal {R}\setminus \mathcal {R}_{\mathrm {good}}(pk,sk,m)\). \(\delta (pk,sk)=\max _{m\in {\mathcal {M}}}\delta (pk,sk,m)\). \(\delta =\mathbf {E}[\delta (pk,sk)]\), where the expectation is taken over \((pk,sk) {\leftarrow }Gen\). Consider the games in Figs. 8 and 9.
Game \(G_0\). Since game \(G_0\) is exactly the OW-qPCA game,

Games \(G_0\)-\(G_6\) for the proof of Theorem 2
Game \(G_6\) and game \(G_7\) for the proof of Theorem 2
Game \(G_1\). In game \(G_1\), we replace G by \(G'\) that uniformly samples from “good” randomness at random, i.e., \(G' \overset{\$}{\leftarrow } \varOmega _{G'}\). Following the same analysis as in the proof of Theorem 1, we can have

Game \(G_2\). In game \(G_2\), the \(\textsc {PCO}\) oracle is changed that it makes no use of the secret key any more. Particularly, when  queries PCO oracle, \(Enc(pk,m;G(m))=?c\) is returned instead of \(Dec'(sk,c)=?m\). It is easy to verify that \(Dec'(sk,c)=?m\) is equal to \(Dec(sk,c)=?m \wedge Enc(pk,m;G(m))=?c\). Thus, the outputs of the PCO oracles in \(G_1\) and \(G_2\) merely differs for the case of \(Dec(sk,c)\ne m\) and \(Enc(pk,m;G(m))=c\). But, such a case does not exist since G in this game only samples from “good” randomness. That is, the PCO oracle in \(G_2\) always has the identical output with the one in \(G_1\). Therefore, we have
queries PCO oracle, \(Enc(pk,m;G(m))=?c\) is returned instead of \(Dec'(sk,c)=?m\). It is easy to verify that \(Dec'(sk,c)=?m\) is equal to \(Dec(sk,c)=?m \wedge Enc(pk,m;G(m))=?c\). Thus, the outputs of the PCO oracles in \(G_1\) and \(G_2\) merely differs for the case of \(Dec(sk,c)\ne m\) and \(Enc(pk,m;G(m))=c\). But, such a case does not exist since G in this game only samples from “good” randomness. That is, the PCO oracle in \(G_2\) always has the identical output with the one in \(G_1\). Therefore, we have

Game \(G_3\). In game \(G_3\), we switch the G that only samples from “good” randomness back to an ideal random oracle G. Then, similar to the case of \(G_0\) and \(G_1\), the distinguishing problem between \(G_2\) and \(G_3\) can also be converted to the distinguishing problem between G and \(G'\). Using the same analysis method in bounding the difference between \(G_0\) and \(G_1\), we can have

Game \(G_4\). In game \(G_4\), an additional query to G with classical state \(|m'\rangle |0\rangle \) is performed after  returns \(m'\). Obviously, \(G_4\) has the same output as \(G_3\) and we have
returns \(m'\). Obviously, \(G_4\) has the same output as \(G_3\) and we have

Let \(\ddot{G}\) be the function that \(\ddot{G}(m^*)=\ddot{r}^*\), and \(\ddot{G}=G\) everywhere else, where \(\ddot{r}^*\) is picked uniformly at random from \(\mathcal {R}\).
Game \(G_5\). In game \(G_5\), we replace G by a semi-classical oracle \(\ddot{G}\backslash {m^*}\). For a query input, \(\ddot{G}\backslash {m^*}\) will first query \(\mathcal {O}_{m^*}^{{SC}}\), i.e., perform a semi-classical measurement, and then query \(\ddot{G}\). Let Find be the event that \(\mathcal {O}_{{m^*}}^{SC}\) ever outputs 1 during semi-classical measurements of the queries to \(\ddot{G}\backslash {m^*}\). We note that

since  implies that \(m'=m^*\) in \(G_5\), and \(\ddot{G}\) is classically queried at \(m'\) in \(G_5\)Footnote 5. Applying Lemma 3 with \(X={\mathcal {M}}\), \(Y=\mathcal {R}\), \(S=\{m^*\}\), \(\mathcal {O}_1=G\), \(\mathcal {O}_2=\ddot{G}\) and \(z=(pk, c^*)\), we can have
implies that \(m'=m^*\) in \(G_5\), and \(\ddot{G}\) is classically queried at \(m'\) in \(G_5\)Footnote 5. Applying Lemma 3 with \(X={\mathcal {M}}\), \(Y=\mathcal {R}\), \(S=\{m^*\}\), \(\mathcal {O}_1=G\), \(\mathcal {O}_2=\ddot{G}\) and \(z=(pk, c^*)\), we can have

Game \(G_6\). In game \(G_6\), we replace \( r^*:=G(m^*)\) by \(r^*\overset{\$}{\leftarrow } \mathcal {R}\). Since \(G(m^*)\) is only used once and independent of the oracles \(\ddot{G}\) and PCO,
Note that \(G(m^*)\) is never used in \(G_6\), we can just replace \(G \overset{\$}{\leftarrow } \varOmega _G;\ddot{G}=G;\ddot{G}(m^*)\overset{\$}{\leftarrow } \mathcal {R}\) by \(\ddot{G} \overset{\$}{\leftarrow } \varOmega _G\). For brevity and readability, we will substitute the notation \(\ddot{G}\) with notation G. Then, game \(G_6\) can be rewritten as in Fig. 9.
Game \(G_7\). In game \(G_7\), we replace \(c^*=Enc(pk,m^*;r^*)\) by \(c^*=Enc(pk,m_1^*;r^*)\), where \(m_1^*\overset{\$}{\leftarrow } \mathcal {M}\). Note that the information of \(m^*\) in this game only exists in the oracle \({{G}} \backslash {m^*} \), by Lemma 4 we have

Next, we show that any adversary distinguishing \(G_6\) from \(G_7\) can be converted into an adversary against the IND-CPA security of underlying PKE scheme. Construct an adversary  on input (\(1^\lambda \), pk) as in Fig. 10, where \(\textsf {Find }\) is 1 iff the event \(\textsf {Find }\) that \(\mathcal {O}_{{m_0}}^{SC}\) ever outputs 1 during semi-classical measurements of the queries to \({G}\backslash {m_0}\) happens. Then, according to Lemma 1, if \(b''=0\),
on input (\(1^\lambda \), pk) as in Fig. 10, where \(\textsf {Find }\) is 1 iff the event \(\textsf {Find }\) that \(\mathcal {O}_{{m_0}}^{SC}\) ever outputs 1 during semi-classical measurements of the queries to \({G}\backslash {m_0}\) happens. Then, according to Lemma 1, if \(b''=0\),  perfectly simulates \(G_6\) and
perfectly simulates \(G_6\) and  . If \(b''=1\),
. If \(b''=1\),  perfectly simulates \(G_7\) and
perfectly simulates \(G_7\) and  . Since
. Since


Adversary  for the proof of Theorem 2
for the proof of Theorem 2
Finally, combing this with the bounds derived above, we can conclude that

\(\square \)
Rights and permissions
Copyright information
© 2019 Springer Nature Switzerland AG
About this paper
Cite this paper
Jiang, H., Zhang, Z., Ma, Z. (2019). Tighter Security Proofs for Generic Key Encapsulation Mechanism in the Quantum Random Oracle Model. In: Ding, J., Steinwandt, R. (eds) Post-Quantum Cryptography. PQCrypto 2019. Lecture Notes in Computer Science(), vol 11505. Springer, Cham. https://doi.org/10.1007/978-3-030-25510-7_13
Download citation
DOI: https://doi.org/10.1007/978-3-030-25510-7_13
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-030-25509-1
Online ISBN: 978-3-030-25510-7
eBook Packages: Computer ScienceComputer Science (R0)


 ,
,