Abstract
To ensure uninterrupted cryptographic security, it is important to begin planning the transition to post-quantum cryptography. In addition to creating post-quantum primitives, we must also plan how to adapt the cryptographic infrastructure for the transition, especially in scenarios such as public key infrastructures (PKIs) with many participants. The use of hybrids—multiple algorithms in parallel—will likely play a role during the transition for two reasons: “hedging our bets” when the security of newer primitives is not yet certain but the security of older primitives is already in question; and to achieve security and functionality both in post-quantum-aware and in a backwards-compatible way with not-yet-upgraded software.
In this paper, we investigate the use of hybrid digital signature schemes. We consider several methods for combining signature schemes, and give conditions on when the resulting hybrid signature scheme is unforgeable. Additionally we address a new notion about the inability of an adversary to separate a hybrid signature into its components. For both unforgeability and non-separability, we give a novel security hierarchy based on how quantum the attack is. We then turn to three real-world standards involving digital signatures and PKI: certificates (X.509), secure channels (TLS), and email (S/MIME). We identify possible approaches to supporting hybrid signatures in these standards while retaining backwards compatibility, which we test in popular cryptographic libraries and implementations, noting especially the inability of some software to handle larger certificates.
Access this chapter
Tax calculation will be finalised at checkout
Purchases are for personal use only
Notes
- 1.
A brief overview of notation for quantum computing appears in Appendix A.
References
Akleylek, S., Bindel, N., Buchmann, J., Krämer, J., Marson, G.A.: An efficient lattice-based signature scheme with provably secure instantiation. In: Pointcheval, D., Nitaj, A., Rachidi, T. (eds.) AFRICACRYPT 2016. LNCS, vol. 9646, pp. 44–60. Springer, Cham (2016). doi:10.1007/978-3-319-31517-1_3
Alkim, E., Bindel, N., Buchmann, J., Dagdelen, Ö.: TESLA: tightly-secure efficient signatures from standard lattices. Cryptology ePrint Archive, Report 2015/755 (2015)
Barreto, P., Longa, P., Naehrig, M., Ricardini, J.E., Zanon, G.: Sharper ring-LWE signatures. Cryptology ePrint Archive, Report 2016/1026 (2016)
de Beaudrap, N., Cleve, R., Watrous, J.: Sharp quantum versus classical query complexity separations. Algorithmica 34(4), 449–461 (2002)
Bellare, M., Rogaway, P.: Optimal asymmetric encryption. In: Santis, A. (ed.) EUROCRYPT 1994. LNCS, vol. 950, pp. 92–111. Springer, Heidelberg (1995). doi:10.1007/BFb0053428
Bernstein, D.J., et al.: SPHINCS: Practical Stateless Hash-Based Signatures. In: Oswald, E., Fischlin, M. (eds.) EUROCRYPT 2015. LNCS, vol. 9056, pp. 368–397. Springer, Heidelberg (2015). doi:10.1007/978-3-662-46800-5_15
Bindel, N., Herath, U., McKague, M., Stebila, D.: Transitioning to a quantum-resistant public key infrastructure (full version). Cryptology ePrint Archive, April 2017
Boneh, D., Zhandry, M.: Secure signatures and chosen ciphertext security in a quantum computing world. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8043, pp. 361–379. Springer, Heidelberg (2013). doi:10.1007/978-3-642-40084-1_21
Bos, J.W., Costello, C., Naehrig, M., Stebila, D.: Post-quantum key exchange for the TLS protocol from the ring learning with errors problem. In: 2015 IEEE Symposium on Security and Privacy, pp. 553–570. IEEE Computer Society Press, May 2015
Braithwaite, M.: Google Security Blog: Experimenting with post-quantum cryptography, July 2016. https://security.googleblog.com/2016/07/experimenting-with-post-quantum.html
Buchmann, J., Dahmen, E., Hülsing, A.: XMSS - a practical forward secure signature scheme based on minimal security assumptions. In: Yang, B.-Y. (ed.) PQCrypto 2011. LNCS, vol. 7071, pp. 117–129. Springer, Heidelberg (2011). doi:10.1007/978-3-642-25405-5_8
Campagna, M., et al.: Quantum safe cryptography and security: an introduction, benefits, enablers and challengers. Technical report, ETSI (European Telecommunications Standards Institute) June 2015. http://www.etsi.org/images/files/ETSIWhitePapers/QuantumSafeWhitepaper.pdf
Chen, A.I.-T., Chen, M.-S., Chen, T.-R., Cheng, C.-M., Ding, J., Kuo, E.L.-H., Lee, F.Y.-S., Yang, B.-Y.: SSE implementation of multivariate PKCs on modern x86 CPUs. In: Clavier, C., Gaj, K. (eds.) CHES 2009. LNCS, vol. 5747, pp. 33–48. Springer, Heidelberg (2009). doi:10.1007/978-3-642-04138-9_3
Cooper, D., Santesson, S., Farrell, S., Boeyen, S., Housley, R., Polk, W.: Internet X.509 Public Key Infrastructure Certificate and Certificate Revocation List (CRL) Profile. RFC 5280, May 2008
Dierks, T., Rescorla, E.: The Transport Layer Security (TLS) Protocol Version 1.2. RFC 5246, August 2008
Ducas, L., Durmus, A., Lepoint, T., Lyubashevsky, V.: Lattice signatures and bimodal Gaussians. In: Canetti, R., Garay, J.A. (eds.) CRYPTO 2013. LNCS, vol. 8042, pp. 40–56. Springer, Heidelberg (2013). doi:10.1007/978-3-642-40041-4_3
Fischlin, R., Schnorr, C.P.: Stronger security proofs for RSA and Rabin bits. J. Cryptol. 13(2), 221–244 (2000)
Goldwasser, S., Micali, S., Rivest, R.L.: A digital signature scheme secure against adaptive chosen-message attacks. SIAM J. Comput. 17(2), 281–308 (1988)
Güneysu, T., Lyubashevsky, V., Pöppelmann, T.: Practical lattice-based cryptography: a signature scheme for embedded systems. In: Prouff, E., Schaumont, P. (eds.) CHES 2012. LNCS, vol. 7428, pp. 530–547. Springer, Heidelberg (2012). doi:10.1007/978-3-642-33027-8_31
Housley, R.: Cryptographic Message Syntax (CMS). RFC 5652, September 2009
Nielsen, M.A., Chuang, I.L.: Quantum Computation and Quantum Information. Cambridge University Press, Cambridge (2000)
Ramsdell, B., Turner, S.: Secure/Multipurpose Internet Mail Extensions (S/MIME) Version 3.2 Message Specification. RFC 5751, January 2010
Rescorla, E.: The Transport Layer Security (TLS) protocol version 1.3, draft 19, March 2017. https://tools.ietf.org/html/draft-ietf-tls-tls13-19
Sullivan, N.: Exported authenticators in TLS, draft 01, March 2017. https://tools.ietf.org/html/draft-sullivan-tls-exported-authenticator-01
Acknowledgements
NB acknowledges support by the German Research Foundation (DFG) as part of project P1 within the CRC 1119 CROSSING. DS acknowledges support from Natural Sciences and Engineering Research Council of Canada (NSERC) Discovery grant RGPIN-2016-05146.
Author information
Authors and Affiliations
Corresponding author
Editor information
Editors and Affiliations
Appendices
A A Brief Review of Quantum Computation
A full explanation of quantum computation is beyond the scope of this paper; see a standard text such as Nielsen and Chuang [21]. We can rely on a subset of quantum computation knowledge.
A quantum system is a complex Hilbert space \(\mathcal {H}\) with an inner product. Vectors in \(\mathcal {H}\) are typically denoted using “ket” notation, such as \(\left| {x}\right\rangle \), and the complex conjugate transpose of \(\left| {y}\right\rangle \) is denoted by \(\left\langle {y}\right| \), so that their inner product of \(\left| {x}\right\rangle \) and \(\left| {y}\right\rangle \) is given by \(\langle {y}|{x}\rangle \). A quantum state is a vector in \(\mathcal {H}\) of norm 1. For two quantum systems \(\mathcal {H}_1\) and \(\mathcal {H}_2\), the joint quantum system is given by the tensor product \(\mathcal {H}_1 \otimes \mathcal {H}_2\); for two states \(\left| {x_1}\right\rangle \in \mathcal {H}_1\) and \(\left| {x_2}\right\rangle \in \mathcal {H}_2\), the joint state is denoted by \(\left| {x_1}\right\rangle \left| {x_2}\right\rangle \), or more compactly as \(\left| {x_1, x_2}\right\rangle \).
Some quantum states can be represented as superpositions of other quantum states, such as \(\left| {x}\right\rangle = \frac{1}{\sqrt{2}} \left| {0}\right\rangle + \frac{1}{\sqrt{2}} \left| {1}\right\rangle \). More generally, if \(\{ \left| {x}\right\rangle \}_x\) is a basis for \(\mathcal {H}\), then we can write any superposition in the form \(\left| {y}\right\rangle = \sum _x \psi _x \left| {x}\right\rangle \) where \(\psi _x\) are complex numbers such that \(\left| {y}\right\rangle \) has norm 1.
Quantum operations on \(\mathcal {H}\) can be represented by unitary transformations \(\mathbf {U}\). A side effect of the fact that quantum operations are unitary transformations is that quantum computation (prior to measurement) is reversible, imposing some constraints on how we quantize classical computations. In particular, suppose we want to quantize a classical algorithm A which takes an input \(x \in \{0,1\}^a\) and gives an output \(y \in \{0,1\}^b\). First, we would imagine the classical reversible mapping \(\{0,1\}^a \times \{0,1\}^b \rightarrow \{0,1\}^a \times \{0,1\}^b : (x,t) \mapsto (x, t \oplus A(x))\). Then we construct the corresponding unitary transformation \(\mathbf {A}\) which acts linearly on superpositions of such states: \(\mathbf {A}: \sum _{x,t} \psi _{x,t} \left| {x, t}\right\rangle \mapsto \sum _{x,t} \psi _{x,t} \left| {x, t \oplus A(x)}\right\rangle \). For full generality, we may allow a workspace register alongside the input and output registers, and thus we in fact use \(\mathbf {A}: \sum _{x,t,z} \psi _{x,t,z} \left| {x, t,z}\right\rangle \mapsto \sum _{x,t,z} \psi _{x,t,z} \left| {x, t \oplus A(x),z}\right\rangle \).
B Unforgeability Separations and Implications
Theorem 6
(
\(\mathsf {Q^qQ}\implies \mathsf {Q^cQ}\implies \mathsf {C^cQ}\implies \mathsf {C^cC}\)
). If \(\varSigma \) is a  -secure signature scheme, then \(\varSigma \) is also
-secure signature scheme, then \(\varSigma \) is also  -secure. If \(\varSigma \) is a
-secure. If \(\varSigma \) is a  -secure signature scheme, then \(\varSigma \) is also
-secure signature scheme, then \(\varSigma \) is also  -secure. If \(\varSigma \) is a
-secure. If \(\varSigma \) is a  -secure signature scheme, then \(\varSigma \) is also
-secure signature scheme, then \(\varSigma \) is also  -secure.
-secure.
Theorem 7
(
\(\mathsf {C^cC}\)  \(\mathsf {C^cQ}\)
). If the RSA problem is hard for classical computers and there exists a signature scheme \(\varSigma \) that is
\(\mathsf {C^cQ}\)
). If the RSA problem is hard for classical computers and there exists a signature scheme \(\varSigma \) that is  -secure, then there exists a signature scheme \(\varSigma '\) that is
-secure, then there exists a signature scheme \(\varSigma '\) that is  -secure but not
-secure but not  -secure.
-secure.
Proof
Let \(\varPi \) be a public key encryption scheme that is IND-CPA-secure against classical adversaries and whose security relies on the hardness of the RSA problem, e.g., [17] or OAEP [5]. However, a quantum adversary could use Shor’s algorithm to factor the modulus and decrypt ciphertexts encrypted using \(\varPi \). We construct a scheme \(\varSigma '\) that is based on \(\varSigma \), but the public key of \(\varSigma '\) includes a \(\varPi \)-encrypted copy of the \(\varSigma \) secret key:
-
\(\varSigma '.\mathsf {KeyGen}()\):
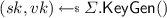 .
. 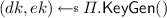 .
. 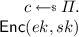 . \(vk' \leftarrow (vk, ek, c)\). Return \((sk, vk')\).
. \(vk' \leftarrow (vk, ek, c)\). Return \((sk, vk')\). -
\(\varSigma '.\mathsf {Sign}(sk, m)\): Return \(\varSigma .\mathsf {Sign}(sk, m)\).
-
\(\varSigma '.\mathsf {Verify}(vk' = (vk, ek, c), m, \sigma )\): Return \(\varSigma .\mathsf {Verify}(vk, m, \sigma )\).
The theorem then follows as a consequence of the following two claims, the proofs of which are immediate. \(\square \)
Claim 1
If \(\varPi \) is IND-CPA-secure against a classical adversary and \(\varSigma \) is  -secure, then \(\varSigma '\) is
-secure, then \(\varSigma '\) is  -secure.
-secure.
Claim 2
If there exists an efficient quantum adversary \(\mathcal {A}\) against the message recovery of \(\varPi \), then \(\varSigma '\) is not  -secure.
-secure.
Theorem 8
(
\(\mathsf {C^cC}\)  \(\mathsf {C^cQ}\)
). If the RSA problem is hard for classical computers and there exists a signature scheme \(\varSigma \) that is
\(\mathsf {C^cQ}\)
). If the RSA problem is hard for classical computers and there exists a signature scheme \(\varSigma \) that is  -secure, then there exists a signature scheme \(\varSigma '\) that is
-secure, then there exists a signature scheme \(\varSigma '\) that is  -secure but not
-secure but not  -secure.
-secure.
Since the basic idea for the proof of Theorem 8 is similar to that of Theorem 7, and due to space constraints, we leave details to the full version [7]. Briefly, the idea of the construction of the scheme for the separation is as follows. Here, we put an encrypted random challenge in the public verification key, and if the adversary asks for that challenge to be signed, we have the signing oracle return the signing key. Intuitively, only an adversary that can break the challenge while it has access to the signing oracle (i.e., a quantum stage-1 adversary) can solve the challenge. The scheme \(\varSigma '\) is shown below.
-
\(\varSigma '.\mathsf {KeyGen}()\):
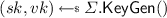 .
. 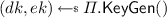 .
.  . \(ch \leftarrow \varPi .\mathsf {Enc}(ek, s^*)\). \(vk' \leftarrow (vk, ek, ch)\). \(sk' \leftarrow (sk, s^*)\). Return \((sk', vk')\).
. \(ch \leftarrow \varPi .\mathsf {Enc}(ek, s^*)\). \(vk' \leftarrow (vk, ek, ch)\). \(sk' \leftarrow (sk, s^*)\). Return \((sk', vk')\). -
\(\varSigma '.\mathsf {Sign}(sk' = (sk, s^*), m)\): If \(m=s^*\), return \(sk\). Else, return \(\varSigma .\mathsf {Sign}(sk, m)\).
-
\(\varSigma '.\mathsf {Verify}(vk' = (vk, ek, ch), m, \sigma )\): Return \(\varSigma .\mathsf {Verify}(vk, m, \sigma )\).
Theorem 9
(
\(\mathsf {Q^cQ}\)  \(\mathsf {Q^qQ}\)
). Assuming there exists a quantum-secure pseudorandom family of permutations, and a signature scheme \(\varSigma \) that is
\(\mathsf {Q^qQ}\)
). Assuming there exists a quantum-secure pseudorandom family of permutations, and a signature scheme \(\varSigma \) that is  -secure, then there exists a signature scheme \(\varSigma '\) that is
-secure, then there exists a signature scheme \(\varSigma '\) that is  -secure but not
-secure but not  -secure.
-secure.
Similar to Theorem 8, we will construct a signature scheme where the secret key is hidden behind a problem which is hard for some adversaries and easy for others. Here the hidden problem will be on oracle problem where a small number of queries suffices to retrieve a secret string when the oracle is queried in superposition, but a large number of queries is required if the oracle is queried classically. We will use the hidden linear structure problem [4].
Definition 2
[4]. The hidden linear structure problem is as follows: given oracle access to \(\mathcal {B} _{s,\pi }(x,y) = (x, \pi (y \oplus sx))\), where \(x,y,s \in GF(2^n)\) and \(\pi \in Perm({\{0,1\}}^{n})\) with s and \(\pi \) chosen uniformly at random, determine s. (Here, Perm(S) denotes the set of all permutations on a set S.)
The hidden linear structure problem requires \(2^b\) classical queries to solve with probability \(2^{2b - n + 1}\) (i.e. \(O(2^{n/2})\) queries to solve with a constant probability), and one query to solve with quantum queries [4]. Unfortunately, describing \(\pi \) requires an exponential number of bits in n, but we can replace the random permutation \(\pi \) with a family of quantum-safe pseudo random permutation with a short key. This results in an oracle with a short description. Supposing that the PRP is indistinguishable from a random permutation in time \(c_\mathcal {P}\) except with advantage \(p_\mathcal {P}\), the resulting restricted oracle problem is indistinguishable from the hidden linear structure problem except with advantage \(p_\mathcal {P}\). From now on we assume that \(\pi \) is implemented by a PRP.
Our construction starts with a  -secure signature scheme \(\varSigma \). For our purposes, we will need \(\varSigma .\mathsf {Sign}\) to be deterministic. That is, for a particular message and signing key the signature should always be the same. If this is not the case, then we can use standard techniques to make it so, for example by providing randomness through a quantum-secure PRF applied to the signing key and the message. Let us suppose that it takes at least time \(c_\varSigma \) for an adversary to win the
-secure signature scheme \(\varSigma \). For our purposes, we will need \(\varSigma .\mathsf {Sign}\) to be deterministic. That is, for a particular message and signing key the signature should always be the same. If this is not the case, then we can use standard techniques to make it so, for example by providing randomness through a quantum-secure PRF applied to the signing key and the message. Let us suppose that it takes at least time \(c_\varSigma \) for an adversary to win the  security game with probability at least \(p_\varSigma \).
security game with probability at least \(p_\varSigma \).
We will need to address several parts of messages for signing. For a message m we will define m.x, m.y, m.z to be bits 1 to 256, bits 257 to 512, and bits 513 to 768 of m, respectively. In particular, m must be at least 768 bits long. Bits beyond 768 will play no special role in the signing algorithm, but remain part of the message. Also let \(\delta _{a,b}\) be the Kronecker delta, which is 1 when \(a=b\) and 0 otherwise.
We now define our signature scheme \(\varSigma '\) as follows:
-
\(\varSigma '.\mathsf {KeyGen}()\):
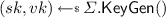 .
. 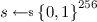 .
. 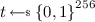 . \(vk' \leftarrow (vk)\). \(sk' \leftarrow (sk, s, t)\). Return \((sk', vk')\).
. \(vk' \leftarrow (vk)\). \(sk' \leftarrow (sk, s, t)\). Return \((sk', vk')\). -
\(\varSigma '.\mathsf {Sign}(sk', m)\): Return \((\varSigma .\mathsf {Sign}(sk, m), \mathcal {B} _{s,t}(m.x,m.y), sk\cdot \delta _{s,m.z})\).
-
\(\varSigma '.\mathsf {Verify}(vk', m, (\sigma , u,v,w))\): If \(\varSigma .\mathsf {Verify}(vk, m, \sigma )\) accepts, \((u,v) = \mathcal {B} _{s,t}(m.x, {} m.y)\) and \(w = sk\cdot \delta _{m.z, s}\) then accept, otherwise reject.
Since we are interested in the case of quantum access, we define the quantum version of the signing oracle by \(U_{\varSigma ', sk}\), which has the action
where \(\sigma = \varSigma .\mathsf {Sign}(sk, m)\), \((u,v) = \mathcal {B} _{s,t}(m.x,m.y)\), and \(w = sk\cdot \delta _{s,m.z}\). Note that \(U_{\varSigma ', sk}\) is its own inverse.
Lemma 1
Suppose that, with classical queries, at least \(c_\mathcal {B} \) queries to \(\mathcal {B} _{s,t}\) are required to determine s with probability \(p_\mathcal {B} \), and that it takes at least time \(c_\varSigma \) for an adversary to win the  security game for \(\varSigma \) with probability at least \(p_\varSigma \). If a (possibly quantum) adversary \(\mathcal {A}\) with classical access to a \(\varSigma '.\mathsf {Sign}\) oracle and \(vk\) runs for time \(c < \min \{c_\mathcal {B}, c_\varSigma \}\), then \(\mathcal {A}\) wins the
security game for \(\varSigma \) with probability at least \(p_\varSigma \). If a (possibly quantum) adversary \(\mathcal {A}\) with classical access to a \(\varSigma '.\mathsf {Sign}\) oracle and \(vk\) runs for time \(c < \min \{c_\mathcal {B}, c_\varSigma \}\), then \(\mathcal {A}\) wins the  security game for \(\varSigma '\) with probability at most \(p \le p_\mathcal {B} + p_\varSigma + 2^{-256} c\).
security game for \(\varSigma '\) with probability at most \(p \le p_\mathcal {B} + p_\varSigma + 2^{-256} c\).
The lemma can be proven by noting \(\mathcal {B} _{s,t}\) and \(\varSigma \) are not related, so we can basically add the probabilities of determining s through \(\mathcal {B} _{s,t}\), producing valid signatures without s, and guessing s directly.
Lemma 2
Suppose \(\varSigma .\mathsf {Sign}\) is deterministic. If, given quantum query access to \(\mathcal {B} _{s,t}\) it is possible to recover s with 1 query, then 3 quantum queries to \(U_{\varSigma ', sk}\) suffice to efficiently generate any polynomial number of valid signatures for \(\varSigma '\).
The basic mechanism here is to use a standard technique in quantum computing called uncomputing to construct a quantum oracle for \(\mathcal {B} _{s, t}(x,y)\) out of two calls to \(U_{\varSigma ', sk}\). Then it is possible to determine s and recover \(sk\) with one more call to \(U_{\varSigma ', sk}\).
We are now in a position to prove Theorem 9.
Proof
(Proof of Theorem 9
). We use \(\varSigma '\) as defined earlier, with \(\mathcal {B} _{s,t}\) being the oracle for a quantum safe hidden linear structure problem, which exists by the existence of \(\mathcal {P}\). By Lemma 2, \(\varSigma '\) is not  -secure since a quantum adversary allowed quantum oracle access to \(\varSigma '.\mathsf {Sign}\) can efficiently generate a polynomial number of signatures using a constant number of oracle queries.
-secure since a quantum adversary allowed quantum oracle access to \(\varSigma '.\mathsf {Sign}\) can efficiently generate a polynomial number of signatures using a constant number of oracle queries.
Now suppose we have a quantum adversary \(\mathcal {A}\) which has classical oracle access to \(\varSigma '.\mathsf {Sign}\) and runs in time \(2^b < \max \{2^{n/2 - 2}, c_\varSigma \}\). \(\mathcal {A}\) obtains s through classical oracle access to \(\mathcal {B} \) with probability at most \(2^{2b - n + 1} + p_\mathcal {P}\). Then we can set \(p_\mathcal {B} = 2^{2b - n + 1} + p_\mathcal {P}\) and apply Lemma 1 to find that \(\mathcal {A}\) breaks unforgeability of \(\varSigma '\) with probability at most \(p_\varSigma + 2^{2b - n + 1} + \delta + 2^{b - 256}\). If \(\mathcal {A}\) runs in polynomial time, then \(b \in O(\log (\mathrm {poly}(n))\) and hence \(\varSigma '\) is  -secure. \(\square \)
-secure. \(\square \)
C Proofs for Combiners
1.1 C.1 \(C_\Vert \): Concatenation
Proof
(Proof of Theorem 1 – unforgeability of \(C_\Vert \)
). Suppose \(\mathcal {A}\) is an \(\mathsf {R^sT}\)-adversary that finds a forgery in \(\varSigma ' = C_\Vert (\varSigma _1, \varSigma _2)\) — in other words, it outputs \(q_S+1\) valid signatures under \(\varSigma '\) on distinct messages. We can construct an \(\mathsf {R^sT}\) algorithm \(\mathcal {B} _1\) that finds a forgery in \(\varSigma _1\). \(\mathcal {B} _1\) interacts with an \(\mathsf {R^sT}\) challenger for \(\varSigma _1\) which provides a public key \(vk_1\). \(\mathcal {B} _1\) generates a key pair  and sets the public key for \(\varSigma '\) to be \((vk_1, vk_2)\). When \(\mathcal {A}\) asks for \(\sum _{m,t,z} \psi _{m,t,z} \left| {m,t,z}\right\rangle )\) to be signed using \(\varSigma '\), we treat t as consisting of two registers \(t_1 \Vert t_2\), \(\mathcal {B} _1\) proceeds by passing the m, \(t_1\), and z registers to its signing oracle for \(\varSigma _1\), then runs the quantum signing operation from Fig. 1 for \(\varSigma _2.\mathsf {Sign}\) on the m, \(t_2\), and z registers. There is a one-to-one correspondence between \(\mathcal {A}\)’s queries to its signing oracle and \(\mathcal {B} _1\)’s queries to its signing oracle.
and sets the public key for \(\varSigma '\) to be \((vk_1, vk_2)\). When \(\mathcal {A}\) asks for \(\sum _{m,t,z} \psi _{m,t,z} \left| {m,t,z}\right\rangle )\) to be signed using \(\varSigma '\), we treat t as consisting of two registers \(t_1 \Vert t_2\), \(\mathcal {B} _1\) proceeds by passing the m, \(t_1\), and z registers to its signing oracle for \(\varSigma _1\), then runs the quantum signing operation from Fig. 1 for \(\varSigma _2.\mathsf {Sign}\) on the m, \(t_2\), and z registers. There is a one-to-one correspondence between \(\mathcal {A}\)’s queries to its signing oracle and \(\mathcal {B} _1\)’s queries to its signing oracle.
If \(\varSigma _1\) is proven to be secure in the random oracle (rather than standard) model, then this proof of  also proceeds in the random oracle model: \(\mathcal {B} _1\) relays \(\mathcal {A}\)’s hash oracle queries directly to its oracle, giving a one-to-one correspondence between \(\mathcal {A}\)’s queries to its hash oracle and \(\mathcal {B} _1\)’s queries to its hash oracle. This holds in either the classical or quantum random oracle model.
also proceeds in the random oracle model: \(\mathcal {B} _1\) relays \(\mathcal {A}\)’s hash oracle queries directly to its oracle, giving a one-to-one correspondence between \(\mathcal {A}\)’s queries to its hash oracle and \(\mathcal {B} _1\)’s queries to its hash oracle. This holds in either the classical or quantum random oracle model.
If \(\mathcal {A}\) wins the  game, then it has returned \(q_S+1\) valid signatures \(\sigma '_i=(\sigma '_{i,1},\sigma '_{i,2})\) on distinct messages \(m_i\) such that \(\varSigma _1.\mathsf {Verify}(vk_1, m_i, \sigma '_{i,1})=1\) and \(\varSigma _2.\mathsf {Verify}(vk_2,m_i,\sigma '_{i,2})=1\). \(\mathcal {B} _1\) can extract from this \(q_S+1\) valid signatures under \(\varSigma _1\) on distinct messages. Thus,
game, then it has returned \(q_S+1\) valid signatures \(\sigma '_i=(\sigma '_{i,1},\sigma '_{i,2})\) on distinct messages \(m_i\) such that \(\varSigma _1.\mathsf {Verify}(vk_1, m_i, \sigma '_{i,1})=1\) and \(\varSigma _2.\mathsf {Verify}(vk_2,m_i,\sigma '_{i,2})=1\). \(\mathcal {B} _1\) can extract from this \(q_S+1\) valid signatures under \(\varSigma _1\) on distinct messages. Thus,  . Similarly it holds for \(\varSigma _2\):
. Similarly it holds for \(\varSigma _2\):  .
.
It follows that  Thus, if either
Thus, if either  or
or  is small, then so too is
is small, then so too is  .
.
1.2 C.2 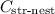 : Strong Nesting
: Strong Nesting
Proof
(Proof of Theorem 2 – unforgeability of  ). This proof follows the same approach as the proof of unforgeability for \(C_\Vert \) (Theorem 1). Details appear in the full version [7]. \(\square \)
). This proof follows the same approach as the proof of unforgeability for \(C_\Vert \) (Theorem 1). Details appear in the full version [7]. \(\square \)
Proof
(Proof sketch of Theorem 3 – 2-non-separability of  ). We can construct a reduction \(\mathcal {B} _2\) which is an
). We can construct a reduction \(\mathcal {B} _2\) which is an  adversary for \(\varSigma _2\). \(\mathcal {B} _2\) generates a keypair \((vk_1, sk_1)\) for \(\varSigma _1\), and interacts with an
adversary for \(\varSigma _2\). \(\mathcal {B} _2\) generates a keypair \((vk_1, sk_1)\) for \(\varSigma _1\), and interacts with an  challenge for \(\varSigma _2\). When \(\mathcal {A}\) classically queries its signing oracle to obtain a signature under \(\varSigma '\) of \(m_i\), \(\mathcal {B} _2\) signs \(m_i\) with \(\varSigma _1\) to obtain \(\sigma _{i,1}\). Afterwards, \(\mathcal {B} _2\) passes \((m,\sigma _{i,1})\) to its \(\varSigma _2\) signing oracle and returns the resulting \(\sigma _{i,2}\) to \(\mathcal {A}\). Eventually, \(\mathcal {A}\) returns \((\mu ^*, \sigma ^*)\) such that \(\varSigma _2.\mathsf {Verify}(vk_2, \mu ^*, \sigma ^*)=1\) but \(\varSigma '.R(\mu ^*)=0\), i.e., \(\mu ^* \not \in \{0,1\}^*\times \mathcal {S}_{\varSigma _1}\). This means in particular that \(\mu ^* \ne (m_i,\sigma _{1,i})\) for all i. Moreover, all the \((m_i,\sigma _{1,i})\) are distinct, since all \(m_i\) are distinct. This means we have \(q_S+1\) valid message-signature pairs under \(\varSigma _2\), yielding a successful forgery for the
challenge for \(\varSigma _2\). When \(\mathcal {A}\) classically queries its signing oracle to obtain a signature under \(\varSigma '\) of \(m_i\), \(\mathcal {B} _2\) signs \(m_i\) with \(\varSigma _1\) to obtain \(\sigma _{i,1}\). Afterwards, \(\mathcal {B} _2\) passes \((m,\sigma _{i,1})\) to its \(\varSigma _2\) signing oracle and returns the resulting \(\sigma _{i,2}\) to \(\mathcal {A}\). Eventually, \(\mathcal {A}\) returns \((\mu ^*, \sigma ^*)\) such that \(\varSigma _2.\mathsf {Verify}(vk_2, \mu ^*, \sigma ^*)=1\) but \(\varSigma '.R(\mu ^*)=0\), i.e., \(\mu ^* \not \in \{0,1\}^*\times \mathcal {S}_{\varSigma _1}\). This means in particular that \(\mu ^* \ne (m_i,\sigma _{1,i})\) for all i. Moreover, all the \((m_i,\sigma _{1,i})\) are distinct, since all \(m_i\) are distinct. This means we have \(q_S+1\) valid message-signature pairs under \(\varSigma _2\), yielding a successful forgery for the  experiment for \(\varSigma _2\). Thus,
experiment for \(\varSigma _2\). Thus,  \(\square \)
\(\square \)
1.3 C.3 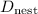 : Dual Message Combiner Using Nesting
: Dual Message Combiner Using Nesting
Proof
(Proof sketch of Theorem 4 – unforgeability of  ). This theorem contains two statements. The first statement is: If \(\varSigma _1\) is
). This theorem contains two statements. The first statement is: If \(\varSigma _1\) is  -secure, then
-secure, then  is
is  -secure with respect to its first message component only.
-secure with respect to its first message component only.  , when restricted to its first message component only, is just \(\varSigma _1\), so the first statement follows vacuously.
, when restricted to its first message component only, is just \(\varSigma _1\), so the first statement follows vacuously.
Now consider the second statement:  is
is  -secure if \(\varSigma _2\) is
-secure if \(\varSigma _2\) is  -secure. Suppose \(\mathcal {A}\) is a \(\mathsf {U^vW}\) algorithm that outputs a forgery for
-secure. Suppose \(\mathcal {A}\) is a \(\mathsf {U^vW}\) algorithm that outputs a forgery for  — in other words, it outputs \(q_S+1\) valid signatures under \(\varSigma '\) on distinct messages. We can construct an \(\mathsf {U^vW}\) algorithm \(\mathcal {B} _2\) that finds a forgery in \(\varSigma _2\). \(\mathcal {B} _2\) interacts with an \(\mathsf {U^vW}\) challenger for \(\varSigma _2\) which provides a public key \(vk_2\). \(\mathcal {B} _2\) generates a key pair
— in other words, it outputs \(q_S+1\) valid signatures under \(\varSigma '\) on distinct messages. We can construct an \(\mathsf {U^vW}\) algorithm \(\mathcal {B} _2\) that finds a forgery in \(\varSigma _2\). \(\mathcal {B} _2\) interacts with an \(\mathsf {U^vW}\) challenger for \(\varSigma _2\) which provides a public key \(vk_2\). \(\mathcal {B} _2\) generates a key pair  and sets the public key for \(\varSigma '\) to be \((vk_1, vk_2)\). When \(\mathcal {A}\) asks for \(\sum _{m,t,z} \psi _{m,t,z} \left| {m,t,z}\right\rangle )\) to be signed using \(\varSigma '\), we treat t as consisting of two registers \(t_1 \Vert t_2\), \(\mathcal {B} _2\) proceeds by passing the m, \(t_2\), and z registers to its signing oracle for \(\varSigma _2\), then runs the quantum signing operation from Fig. 1 for \(\varSigma _1.\mathsf {Sign}\) on the m, \(t_1\), and z registers. There is a one-to-one correspondence between \(\mathcal {A}\)’s queries to its oracle and \(\mathcal {B} _2\)’s queries to its oracle. As before in the proof of Theorem 1, if \(\varSigma _1\) is proven to be secure in the random oracle model, then this proof of
and sets the public key for \(\varSigma '\) to be \((vk_1, vk_2)\). When \(\mathcal {A}\) asks for \(\sum _{m,t,z} \psi _{m,t,z} \left| {m,t,z}\right\rangle )\) to be signed using \(\varSigma '\), we treat t as consisting of two registers \(t_1 \Vert t_2\), \(\mathcal {B} _2\) proceeds by passing the m, \(t_2\), and z registers to its signing oracle for \(\varSigma _2\), then runs the quantum signing operation from Fig. 1 for \(\varSigma _1.\mathsf {Sign}\) on the m, \(t_1\), and z registers. There is a one-to-one correspondence between \(\mathcal {A}\)’s queries to its oracle and \(\mathcal {B} _2\)’s queries to its oracle. As before in the proof of Theorem 1, if \(\varSigma _1\) is proven to be secure in the random oracle model, then this proof of  also proceeds in the random oracle model: \(\mathcal {B} _2\) relays \(\mathcal {A}\)’s hash oracle queries directly to its hash oracle, giving a one-to-one correspondence between \(\mathcal {A}\)’s queries to its (classical or quantum) hash oracle and \(\mathcal {B} _2\)’s queries to its (classical or quantum, respectively) hash oracle.
also proceeds in the random oracle model: \(\mathcal {B} _2\) relays \(\mathcal {A}\)’s hash oracle queries directly to its hash oracle, giving a one-to-one correspondence between \(\mathcal {A}\)’s queries to its (classical or quantum) hash oracle and \(\mathcal {B} _2\)’s queries to its (classical or quantum, respectively) hash oracle.
If \(\mathcal {A}\) wins the  game, then it has returned \(q_S+1\) distinct tuples \((m_{1,i}, m_{2,i}, \sigma _{1,i}, \sigma _{2,i})\) such that \(\varSigma _1.\mathsf {Verify}(vk_1, m_{1,i}, \sigma _{1,i})=1\) and \(\varSigma _2.\mathsf {Verify}(vk_2, {} (m_{1,i}, \sigma _{1,i}, m_{2,i}), \sigma _{2,i})=1\).
game, then it has returned \(q_S+1\) distinct tuples \((m_{1,i}, m_{2,i}, \sigma _{1,i}, \sigma _{2,i})\) such that \(\varSigma _1.\mathsf {Verify}(vk_1, m_{1,i}, \sigma _{1,i})=1\) and \(\varSigma _2.\mathsf {Verify}(vk_2, {} (m_{1,i}, \sigma _{1,i}, m_{2,i}), \sigma _{2,i})=1\).
Hence, \(\mathcal {B} _2\) can extract \(q_S+1\) valid signatures under \(\varSigma _2\) and thus it holds that  \(\square \)
\(\square \)
Rights and permissions
Copyright information
© 2017 Springer International Publishing AG
About this paper
Cite this paper
Bindel, N., Herath, U., McKague, M., Stebila, D. (2017). Transitioning to a Quantum-Resistant Public Key Infrastructure. In: Lange, T., Takagi, T. (eds) Post-Quantum Cryptography . PQCrypto 2017. Lecture Notes in Computer Science(), vol 10346. Springer, Cham. https://doi.org/10.1007/978-3-319-59879-6_22
Download citation
DOI: https://doi.org/10.1007/978-3-319-59879-6_22
Published:
Publisher Name: Springer, Cham
Print ISBN: 978-3-319-59878-9
Online ISBN: 978-3-319-59879-6
eBook Packages: Computer ScienceComputer Science (R0)


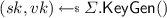 .
. 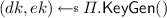 .
. 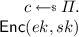 .
. 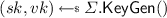 .
. 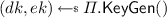 .
.  .
. 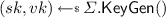 .
. 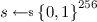 .
. 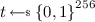 .
. 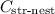 : Strong Nesting
: Strong Nesting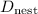 : Dual Message Combiner Using Nesting
: Dual Message Combiner Using Nesting